Michael Oliver27-Jul-2015 07:18this seller from Togo by name William is a scammer. beware of him and his scam plans. he company name Consultancy Firm
Mr. Michael Oliver25-Jul-2015 11:20We assist all buyers nationwide to confirm buyers of gold and diamond dealers in west Africa and beyond. Contact: Mr. Michael Oliver Email: moliverpmmcgh@gmail.com
James Kendall25-Jul-2015 02:37Does the Angel Security Group exist in Accra Ghana. Thank-you.
Michael Anson19-Jul-2015 08:56To John Francis and Ron George, we have also been looking for further information about Gregory Hall and United Golden Success. Does anyone have further feedback on this group? Are they genuine sellers?
Frank Rosenthal17-Jul-2015 23:25Please advise me if this person and company is for real. Thank you
Rawlin Westover
send to rawlin.westove@century21.com
Guest13-Jul-2015 15:23Tikum mines, Eric, Dose not deliver, good Cop bad Cop, Keeps asking for more money
Guest12-Jul-2015 14:53Mohamend Bello and Abraham Koffi have gold in Lome, Togo, but will not honor contracts and keep adding new fees and expenses, they won?t deliver as agreed. Avoid them.
ictc11-Jul-2015 12:34I HAVE BEEN A FINANCIAL MARKET TRADER FOR 2 YEARS NOW, BOTH STOCK, CURRENCY, METALS AND GOLD TRADING, THAT MEANS OUR CONSULTANCY GOES MORE FAR THAN CONNECTING BUYERS AND SELLERS BECAUSE WE ADVISE OUR BUYERS ON THE RIGHT TIME TO BUY AND SELL GOOD AND WE UNDERSTAND THE MARKET MOVEMENT BETTER THAN ANYONE ELSE, WE KNOW WHEN GOLD IS TO GET MOMENTUM AND WHEN IS EXPECTED TO FALL, THE RIGHT TIME TO INVEST/BUY GOLD AND THE TO SELL YOUR GOLD. WE BUY AND SELL GOLD AND MAKE PROFIT FROM THE UP AND DOWN MOVEMENT.
sama09-Jul-2015 15:27Hello
Guys when i read you tearful experiences , i just can say how sorry it could be , well if you think , you will need any help verifying any sellers in Cameroon , send me an email at info@raftcameroon.com
my company deals with precious metals and have our 100% authentic export licenses . we have take our diamonds to dubai twice although prefer selling Locally now.
So if you are finding difficulty or doubting any documentation from any seller in cameroon we will be happy to be of help.
Guest08-Jul-2015 22:52Good day all
Has anyone heard of or engaged negotiation with GDF Mining??? They apparently have offices in Zambia, Uganda and Tanzania.
Any assistance would be valued?
Wieslaw07-Jul-2015 12:34Beware of the company Chief Franklin & son. It?s scammer.
Shamsi27-Jun-2015 12:47Guinea Conakry Scammer: CAMARA FODE CABINET INTERNATIONAL MANAGER: Barrister Camara Fode CONTACT: +224621940846 email:camarafode772@gmail.com; We signed contract and we agreed to pay the shipping cost to Guifret, we have a rep in Conakry and agreed to go their Guifret office to verify the shipment but Fode and Guifret refused to meet the rep and requested for Western Union payment directly. We offered the seller to deposit the gold at the central bank and we arrange for shipment to Dubai but he refused; I can post his passport copy as well as shipping company information if there is a room in this website.
Guest17-Jun-2015 14:25Frankie is a sweet talking Taxi driver in Tanzania. He will entice you into some gold deal and promise to link you up with dealers in either Tanzania of Zambia. His cellphone no is +255 723 722 744
Edward16-Jun-2015 15:02Thank you for this site: Please be warned of the following scammers that I lost money to and they never delivered any gold:
1. Kalombo Jean Kalenga Congolese Passport No OB222551 and his email address is kajean@gmail.com. Please don?t deal with this man he has no gold to deliver but will ask you for cash advance. He will then never pick your calls. A signed contract means nothing to him.
2. Abdul Mtekela, He is a Tanzanian Member of Parliament and works in corhort. He uses his name and image to win trust and money from you. He was to deliver 100kgs but took my money and never answers or returns my calls. I cant do anything to him as he will use his position in government to intimidate. His emails: abdulnjaiti@gmail.com and tel no is +255 718 465 555 or +255 787 047 777
3. Fiston Ngirimana (Burundian passport) also travels as Fiston Mukendi a Congelese national, Keep away from him
4. Ramadhan Isaac, a Burundian national and works with Fiston above . Two sold me 3Kgs of Brass in the name of gold.
Jonathan16-Jun-2015 10:55Thanks to Mr Nicholas otieno of government of Kenya who helped me recover a small portion of the money I lost while in Kenya,you were true to your word sir.the 20kilos I bought were enough to start me over,thanks for the referrals
Nicholas15-Jun-2015 08:07I think it?s time the admin check some people posting on this site if they are the genuine name holders
Nicholas15-Jun-2015 08:01Buyers claiming to be doing FOB in Nairobi,Karen area are a fake lot,one is Ryan and the other is Pablo,fat guy with a beard.Pablo claims to take gold to Dubai without any papers,gold from Congo.He asks you to take 10kilos to their refinery yet he claims to be smuggling over 1000kilos to Dubai every month
steve12-Jun-2015 14:04Guest 11-Sep-2014 08:06
Phillip K Chibundi,
Chibundi and Co
Legal Practitioners
Unit CL1
Stand 483
Kudu Road
Kabulonga
Lusaka
Zambia
Ph: +260211848015
Mobile: +260966 888080
This man is working with gold and diamond scammers. He will claim to be honest but is not. Parcels due to be handed over, will be delayed, appointments missed, turned up drunk to one meeting which he wouldn?t hold in his office so his scam wouldnt be caught.
Others involved in gold scams
Nanou
32 Avenue Gambela
Lubumbashi Katanga
His company is MH Holdings 8647 Mwepu 2nd floor
He is also the youth national president for SCODE
Guest05-Jun-2015 09:15Anyone in Dar serious to buy kindly get in touch
Nicholas05-Jun-2015 09:14Am in Tanzania with an agent of GGR who doesn?t even know where there offices are,Phil you claim to be the know it all guy,kindly explain your incompetence in this.some of us Africans have better things to do,I brought 20kilos of gold to Dar es salaam because I was told that GGR test with XRF and pay at their facilities,now am stuck
Del05-Jun-2015 07:03
Another scammer to be aware of
mohamed nana
Jun 1 (4 days ago)
to
Sir
My name is Nana i am a local gold miner and gold seller,also sale diamond, located in Ghana, we have presently 250 kilos of GOLD bars available to sale out FOB. And we are ready to go into partnership to supply you up to 50 kilos monthly. the purity is 96.1% the carat is 22.51% we sale for very good price per a kilo, we assay to any refinery of buyer?s choices in Ghana we need serious buyer who is ready to come down to Ghana for the inspection of our Gold and signing long contract with our company. let me know your interest to Enable us proceed
immediately.
Mr. Nana
MOHAMED NANA
1:56 PM (18 hours ago)
to me
Dear:Mr.Del,
Thanks for your mail. We are not in UK our family reside in Ghana, as a family we which to good business relationship with you too. We will love to see you in Ghana for round table with the family dignities.
The family has been in the gold mining business for many decades and as I said earlier we will like to partner with you. And where do reside?
Our gold is family property, we have registered shipper, the has the company registered in Ghana that we work with and if you come you will travel our mining site for you to know we also need investor.
Regards
Nana
: ?MOHAMED NANA?
mohamed nana
Government of Kenya02-Jun-2015 07:05Let?s not use the useful important site for jokes and witch-hunting? Anyone who?s asked for my assistance in doing diligence and was never assisted to tell me in my face? Instead of calling me to a five star hotel to determine if I know your scam network..this guy calling us names that we are scammers and can?t help in doing due diligence is the SCAMMER. He cam to me to test if I know his scam fake company? Young man I work with government of Kenya and I think you saw the car I was driving in its a government car. your car is plate is KBZ 131C.. YOUNG MAN I?M COMING FOR YOU? U MUST STOP SCAMING PEOPLE? stop using the name JOHNSON.. I?ll catch u soon and post pictures of you here.
Guest02-Jun-2015 07:04Let?s not use the useful important site for jokes and witch-hunting? Anyone who?s asked for my assistance in doing diligence and was never assisted to tell me in my face? Instead of calling me to a five star hotel to determine if I know your scam network..this guy calling us names that we are scammers and can?t help in doing due diligence is the SCAMMER. He cam to me to test if I know his scam fake company? Young man I work with government of Kenya and I think you saw the car I was driving in its a government car. your car is plate is KBZ 131C.. YOUNG MAN I?M COMING FOR YOU? U MUST STOP SCAMING PEOPLE? stop using the name JOHNSON.. I?ll catch u soon and post pictures of you here.
Guest29-May-2015 06:54THE OWNER OF THIS EMAIL CLAIMING THAT THEY CAN ASSIST YOU TO DO DUE DILIGENCE IS ANOTHER SCAMMER IN KENYA, THEY WORK WITH THE SCAMMERS IN EAST AFRICA AND THEY WILL NOT ASSIST YOU PLEASE KEEP OFF FROM THEM.
Ianricyowen@yahoo.com 17-May-2015 21:42
Hello guys? If anyone wants to buy gold in Kenya just call me on +254727992453 I?ll help you to determine whether your seller is genuine or not by going to the scene and counter checking if the gold really exists or if it?s genuine? I?ll help for free since I?ve zero tolerance for scammers and swindlers.. They are defaming the good name of Kenyan gold sand he and hence making the buyers to shy away from dealing with Kenyans.
Thanks guys
Mike Mol26-May-2015 20:43Any one interested in a Joint venture on a gold mine in Peru? we have invested over 5m and looking for a joint venture partner, we are almost finished with equipment and infratucture, we only need working capital to operate the mine?..interested let me know
Guest26-May-2015 07:13Any one heard about Thai gold being sold to arabs
Guest25-May-2015 08:58We are an International company that deals in Mining,Shipping and Logistics/Chain Supply. We have branches in Kenya, Tanzania,DRC Congo,Uganda Zambia and Zanzibar.
Our clients are from all over the world and they never hesitate to come back for the quality services and goods we always offer.
Derrick23-May-2015 10:45Richard palo..I can help you to verify the document. Contact me ..deredem@live.co.uk
Richard Palo20-May-2015 18:42I?m dealing with another party in Kumasi that is offering me a percentage of their inheritance if I become the foreign beneficiary. They have me in contact with the Barrister and have shown me as several documents. I?m wondering if the case can be verified as legitimate or not ?
Raul Paul20-May-2015 09:52
This site has helped me from scammers and i have good experience of filtering scammmers from genuine and fake sellers. I contacted a logistics company in East Africa and was able to be directed to a mining site where they assisted me to buy directly and was able to export.
Ianricyowen@yahoo.com17-May-2015 21:42Hello guys? If anyone wants to buy gold in Kenya just call me on +254727992453 I?ll help you to determine whether your seller is genuine or not by going to the scene and counter checking if the gold really exists or if it?s genuine? I?ll help for free since I?ve zero tolerance for scammers and swindlers.. They are defaming the good name of Kenyan gold sand he and hence making the buyers to shy away from dealing with Kenyans.
Thanks guys
kamil16-May-2015 13:41watch out for krushev mweemba mwiinde of Zambia. his mail mweemba@gmail.com cheating with is gold and diamonds with an honest miner is plain junk I have his photograph publish them soon
Robert Garcia15-May-2015 22:15Anyone ever hear of Joseboat Ventures, a mining company and a lawyer go between named Barrister Mills Nii Osah. They have partnered me with another Ghana lady and am asking for demurrage payment of $15,000 US
INSPECTOR05-May-2015 19:25INTER CON SECURITIES IS NOT ANYWHERE IN GHANA. ANYONE USING THEM IS FALLING INTO A BIG TRAP.
ITS A BIG SCAM?RUN RUN RUN.
THANKS
Hoss29-Apr-2015 03:51Inter-con Securities
PLT45,BLKD
OSU,ACCRAhttps://www.facebook.com/elitereaderscom/posts/462803373877122
GHANA
Tel: +233245102580
Director of operations ? Dr Paul Andrews
Is this a legitimate company
hoss28-Apr-2015 04:09Has anyone heard of Inter-con Securities of Accra Ghana and is it a legitimate company
Eugene Birrer23-Apr-2015 06:59Joseph Mutua, that group only scam people.
CAM-MINE TRADING COMPANY LTD.
C.E.O Mr. Jefri Charles Lyonga, Passport No: 01723325
Bertoua, EasternRegion, Cameroon
Wayne Sullivan20-Apr-2015 00:51Does anybody know about Nikolas Josie? Is she a scammer? I would like to know before I do business with her.
Canada buyer16-Apr-2015 00:13Hello to all the real gold buyers
I have had a problem with a scammer also named
Goldcoast@email.com
He uses his Baby?s pic on his Skype
He makes you purchase tickets to Dubai from Ghana
And never brings the gold , the scam is he will get his ppl to purchase the ticket from him Probley for 200 or 300 and use your ticket stating his rep will bring the gold
So no one trust goldcoast@email.com
1 more African scam
globaltraders545@gmail.com14-Apr-2015 14:08Hello Biher Eugene,
I had a very bad experience in Kenya also with this group, is there no way to get these criminals arrested?
If you have any help to offer me, contact by email: (globaltraders545@gmail.com)
The admin of this site has done a great job in exposing the criminal, if you can also direct one to a trusted seller of gold, that would be perfect.
Andy14-Apr-2015 12:32I really admire those who have started this site ? atleast we can know who is what !!! The more we put our experiences here the more we will save ourselves and other..
Biher Eugene13-Apr-2015 16:47SCAMMERS WITH SERIOUS CONNECTIONS IN KENYA FROM CUSTOMS THROUGH TO REVENUE AUTHORITY
(This Report was sent to me by one of their Victims after they took 139,000usd and another demand of 50,500usd)
1. Benson Muhanji Mageta
Owner of Manpower Trading Co.
All the Certificates of the product is ?booked? under his company and the product is even in a Safe Keeping Facility that does not exist.
Benson?s Contact details: +254716260360 , +254202323256
Email:mtrhdirector@yahoo.co.uk
2. Jared Kiasa Otieno
Owner of Express Feeders shipping agency or shipping agent and another fake company Global Aviation Shipping International. Jared is the guy that is linked to Former Minister Odinga. This guy has a lot of connections and once he is introduced to the transaction as the shipping agent everything starts going in a different direction and this is where the lawyer is also introduced to use his Escrow account for funds to be paid in.
Jared?s Contact details: +254775588882, +254715588882
Email: gblaviationintl@gmail.com
3. ?Eric? Moussa Gakunzi. This guy is introduced as the son of a General in Congo in the Bunia district. Can ?barely? speak english and he is appointed by his ?father? as representative of the community. He disappears once in a while when he goes back to Congo to report to his father, but he was traced in Nairobi the time claimed he was in Congo.
?Eric?s? contact details: +243995014847 , +254 752524248
Email: m.gakunzi@yahoo.com. ( every mail send to this address comes back as a invalid email, even though he sends mails from this exact address)
4. John be Good. This guy was introduced as a General from a community in Congo as well(can not recall what community). Also resides in Nairobi and we only met once right in the beginning. I do not have any contact details on him.
5. Thomas Okundi the Lawyer. This guy plays his part really well. Keeps his tracks clean and then assure that nobody else is exposed. His wife works for the Kenyan Government and im sure that is one of the connections they use. He is also directly linked to Former Minister Odinga. This guy is a master mind and a huge advantage to all the above mentioned because he knows his way around the law and government contacts. He even threatened me to get me locked up if I dont give them the $50500 that I collected. Wanted to make sure I stay in Kenya with no way out, but I was one step ahead.
Thomas Contact details. +254 722973060
Email: okundi@okundiadvocates.co.ke
THANKS.
Birher Eugen13-Apr-2015 16:44SCAMMERS WITH SERIOUS CONNECTIONS IN KENYA FROM CUSTOMS THROUGH TO REVENUE AUTHORITY
(This Report was sent to me by one of their Victims after they took 139,000usd and another demand of 50,500usd)
1. Benson Muhanji Mageta
Owner of Manpower Trading Co.
All the Certificates of the product is ?booked? under his company and the product is even in a Safe Keeping Facility that does not exist (Cross Over Security).
Benson?s Contact details: +254716260360 , +254202323256
Email:mtrhdirector@yahoo.co.uk
2. Jared Kiasa Otieno
Owner of fake company Express Feeders shipping agency or shipping agent and Global Aviation Shipping International. Jared is the guy that is linked to Former Minister Odinga. This guy has a lot of connections and once he is introduced to the transaction as the shipping agent everything starts going in a different direction and this is where the lawyer is also introduced to use his Escrow account for funds to be paid in.
Jared?s Contact details: +254775588882, +254715588882
Email: gblaviationintl@gmail.com
3. ?Eric? Moussa Gakunzi. This guy is introduced as the son of a General in Congo in the Bunia district. Can ?barely? speak english and he is appointed by his ?father? as representative of the community. He disappears once in a while when he goes back to Congo to report to his father, but he was traced in Nairobi the time claimed he was in Congo.
?Eric?s? contact details: +243995014847 , +254 752524248
Email: m.gakunzi@yahoo.com. ( every mail send to this address comes back as a invalid email, even though he sends mails from this exact address)
4. John be Good. This guy was introduced as a General from a community in Congo as well(can not recall what community). Also resides in Nairobi and we only met once right in the beginning. I do not have any contact details on him.
5. Thomas Okundi the Lawyer. This guy plays his part really well. Keeps his tracks clean and then assure that nobody else is exposed. His wife works for the Kenyan Government and im sure that is one of the connections they use. He is also directly linked to Former Minister Odinga. This guy is a master mind and a huge advantage to all the above mentioned because he knows his way around the law and government contacts. He even threatened me to get me locked up if I dont give them the $50500 that I collected. Wanted to make sure I stay in Kenya with no way out, but I was one step ahead.
Thomas Contact details. +254 722973060
Email: okundi@okundiadvocates.co.ke
ivan09-Apr-2015 11:07Sino Gold Mining Limited
Be kind to revert to mypersonal email(johnmorgan2004@outlook.com)
susan walker07-Apr-2015 22:15anyone dealing with frank welch. he is a scammer of women and gold
JOSEPH MUTUA07-Apr-2015 07:26kINDLY INFORM ME IF HE IS A SCAMMER BEFORE I START TO TRADE WITH HIM
CAM-MINE TRADING COMPANY LTD.
C.E.O Mr. Jefri Charles Lyonga, Passport No: 01723325
Bertoua, EasternRegion, Cameroon
JOSEPH MUTUA07-Apr-2015 07:26kINDLY INFORM ME IF HE IS A SCAMMER BEFORE I START TO TRADE WITH HIM
CAM-MINE TRADING COMPANY LTD.
C.E.O Mr. Jefri Charles Lyonga, Passport No: 01723325
Bertoua, EasternRegion, Cameroon
Richard01-Apr-2015 21:34Is Barrester Scott Winn who works in Accra, Ghana and South Africa known to be a lawyer of good reputation?
eddy01-Apr-2015 15:47Killian Gol
Mr Noel
ETS BRAWN AND SONS
Addresse City Chemist Victoria
North West Region
Camenroon
tel +237 663685408
cell. +237678311071
mail brawnandsons@hotmail.com
Skype id killiangol
sells agricultural products corn barley soybean alfalfa meal and animal feed
are scams do not deliver orders and no longer respond to the phone as soon as you send the advance that require
careful person very polite and very helpful all religious imprint on moral values family and children
then acts unscrupulous once they receive the money
David Carpenter01-Apr-2015 14:07Dear Sir. I just wanted to let you know there is another out there:Mr. Osmond Shipping Adress is GABID ABDUL KARIM cITY:aCCRA COUNTY GHANA Zip code,00233 My dad wasd cought up in it ond lost everythin to this asshole! so please post and let people know, My Dad died on Aug.23,2015 Left everthin to them, Please HELP!!!!!
Guest01-Apr-2015 06:31Hi has anyone here dealt with a Anthony Lefale? He claims to be a broker
JOHN24-Mar-2015 15:44WE HAVE GOLD AVAILABE NOW IN ACCRA GHANA. FOR MORE DETAILS CONTACT ME ON SKYPE.
SKYPE: jh.asamoah
We Work mainly on FOB BASIS please.
John
Guest20-Mar-2015 18:52BEWARE!!! These people are scammers, they have a network of companies and ill ripp you off.
Seller Company Name: CRUZ COMPANY LIMITED
Represented by: Erick Kweku Asiedu (CEO)
Full Address: P.O. BOX 11362, Accra North, Ghana
Tel: +233 26 955 2062
E-mail danso_castle@yahoo.com
Guest20-Mar-2015 18:52BEWARE!!! These people are scammers, they have a network of companies and ill ripp you off.
Seller Company Name: CRUZ COMPANY LIMITED
Represented by: Erick Kweku Asiedu (CEO)
Full Address: P.O. BOX 11362, Accra North, Ghana
Tel: +233 26 955 2062
E-mail danso_castle@yahoo.com
Guest20-Mar-2015 18:50BEWARE!!! These people are scammers
Seller Company Name: ASSAY MINING GHANA LTD
Represented by:DANSO OFORI (Manager)
Passport #: H1929545
Full Address: P.O.BOX AN 15902 ACCRA NORTH
Tel: +233 27 062 1741
E-mail danso_castle@yahoo.com
Guest20-Mar-2015 16:50Beware of Eunice Asanti, she is a scammer, she will take your money and deliver nothing
Suku Mining Company
112 Airport Residential Area
Accra, Ghana
email: eunicenaa201@yahoo.com
Phone #: +233 20 444 6591
Phone #? +233 26 614 6003
Richard Calvy17-Mar-2015 11:54I would like to contact a Nick Harvey who named and shamed one Martin Avent a Brit
Richard Calvy17-Mar-2015 11:53I would like to contact a Nick Harvey who named and shamed a character called Martin Avent
Cynthia15-Mar-2015 17:25Has anyone had dealings with John Gatete of Logix, Inc, Logistics Company of Kampala, Uganda working in concert with Frank Nyombo of Beni Mines DRC, Christian Bakwa, alleged agent with Belgium Passport. Per my experience they have AU, but for show ONLY at Logix, Inc, office in Kampala as support for their ?UPFRONT FEE? SCAM. Please advise of experience if applicable.
kylieh10-Mar-2015 20:57John Frances and Ron George, I would like any information you have on United Gold Success and Gregory hall as I am currently looking to do business with them. You can email me direct at kylie@corinthiancapitalpartners.com
mo04-Mar-2015 13:31gemini can i contact you , concerning global aviation ?
Guest04-Mar-2015 07:56Hello
Robert A. Darreng03-Mar-2015 18:16Anyone heard about JOHN RICKETTS?, company name JOHNLEW (LEWJOHN) 111 GLOBAL INC
They say they are gold seller from Ghana, but they are asking for upfront money for shippment expenses? that doesnt sounds right?
Please advice?
Juanos10-Feb-2015 13:15Any one heard of ZILAG TRADING LLC, GULF ATLANTIC TRADING LLC, SWEETFUTURES.COM. They claim to be commodities trading and I have been offered a gold deal with 2/1 return on investment. Do these deals exist or are they all to be investigated
G?rard Ruiz10-Feb-2015 11:26Hy , I would like to give you information of the Scam I have had, Alfred Deen to Sierra leone i send him 1400$ after one year of negotiation and visite many time on freetown very bad boy and the other man work with him the name is Balansama.
My company is in Monaco and i have another company to Sierra leone
Abdulsalam W M Gashut09-Feb-2015 15:52Hello from Libya, North Africa
Buyer asked me to bring all kinds of gold to Dubai refinery for assay, then for long supply contract,
buyer experienced with Emarates airlines that accept business class passengers more weight more than 50 Kg each, , suggest to come with your representative , .
refinery will take responsibility of gold as from airport, payment transport your hotel with catering,,, full board until return , also your expenses at home country of fees & tax will be added to total account that will be holded on buyer side
I am investor of Libyan stock market LSM, share holder
This opportunity come cross, I would be happy to share a commission,
I will be happy if you FW my ambition to end sellers in West Africa region, considering that as a favour to support you at Libya stock market fron disk in the future.
Regards
Mr. A Gashut
Email: gashute@gmail.com
Tel: 00218916496449
Skype: gashute2014
Gold Buyer Canada03-Feb-2015 23:54Hello I am looking to purchase real gold from africa Specially DORE BAR gold if you can guide me through this to bring it to canada i would appreciate it
Sydney01-Feb-2015 15:29Att.Noel Am the Director of Valour Security Ltf Nrb Kenya. A guest by the Name Sure posted in the site negative and false information that we do fake due deligence and redirect people to fake companies and that we are associated with one Bradley Nelson. For your information we are looking for him he has scammed one of our client 50,000 usd and the complain is in our office and we have the proof. Please delete this info from your systems otherwise people like SURE are going to continue turnishing other people companies through this website.
jenny fox01-Feb-2015 12:45Boland smith and rosena buttler if you are looking for reliable suppliers try globetradelogitics& consultants (East Africa) email. globetradelogistics@gmail.com they are experienced in this region they have all information on procedures of gold transactions.
Esskar01-Feb-2015 08:01This site helped me not to fall pray to scammers and was able to identify a logistics company in East Africa based in Nairobi which lead me to local miners and genuine sellers. Serious buyers try this company Globe Trade Logistics & Consultants Ltd (East Africa)
www.globetradelogistics.com email. globetradelogitics@gmail & info@globetradelogistics.com they will also assist you to do due duligence and expose scammers in East Africa.
Guest27-Jan-2015 13:54To Ron George ? Riverbank House is a very prestigious office block in London ? I somehow doubt whether your people will be using it!
John Frances23-Jan-2015 15:39To Ron George ? please contact me about your post. I have some information for you.
tim18-Jan-2015 03:33why would anyone really sell gold from Nairobi for $26,000 use per kilo? how much does the refinery in Nairobi pay?
Ron George15-Jan-2015 18:52Anyone have information on United Gold Success, allegedly out of Riverbank House in London; or the names Armando Piscioneri and Gregory Hall?
jan van bruggen15-Jan-2015 12:00i need big help to arrest 419 scammers organisation
Ocean Mining Link Group
Mr Kweku Bo
mobile : +233246895315
skype : ocean.mining.group1
i come in december 2014 to arrange gold for my buyer
u small investor , pay in the airport , shipper office eur 12000 for pay export charges to government and prepare documents , i pay eur 1000 for hurry up to paris , 2 days documents finish ,3 days later ready to travel wit seller to paris , no seller he travel 1 day later , was sick, i must go . i go, waiting 5 days in paris with end buyer raffinery Ofa , no seller come . begin off january buyer travel to ghana , seller /shipper said documents expire , stories, nonsens , buyer must pAY USD 25000 !!!BUYER DOESN?T DO THAT ,so i looze alll my money very bad , because te seller not travel in december with me, and now ask buyer again for money , i hAVE ALL documents also forum a4 etc is this seller AND HIS SHIPPER BIG 419 ORGANISATION, PLEASE INTERPOL ARREST AL NO CURE NO PAY , HELP ME SOON BEFORE HE DESTROYED MORE BUYERS FROM EUROPE, EVERY DAY HE ASK FOR NEW BUYERS , VERY BAD , AND COST MY REPUTATION, BUT I PAY FOR THE BUYER , SO I THE RIGT PWERSON, PLEASE HELP ME
SEND YOU RESPONDWS TO ME PLEASE
africantimber50@gmail.com
skype:africantimber50
jan van bruggen15-Jan-2015 11:38419 scammer off gold in ghana
Ocean mining link Group
Mr.Kweku Bo
phone +233246895315
skype : ocean.mining.group1
i mr jan van bruggen .small investor pay eur 12000 to his shipper , we arrange documents with shipper in december ,after 3 weaks buyer come to ghana , he ask usd 25000 more , because documents expire , nonsens, in december i arrange everything to paris , tickets etc , i travel to PARIS, seller never come , ALLWAYS stories, sick etc , he send vip inventation letter for me and the buyer , cost usd 300 each , all is 419
also his shipper Ocean Transit Service (OTS)
Accra
interpol must arrest this organisATION VERY SOON PLEASE
I DO gunuine business, pay for the buyer, have the documents , and seller scam me, very bad
please . please Interpol help me or no cure no pay to arrest all this guys the destroyed ALL MY BUYERS IN GHANA
SEND YOU CONTACT TO ME
JAN VAN BRUGGEN
MAIL : africantimber50@gmail.com
Gemini14-Jan-2015 13:48Hi,
Anyone know Sabastien Koroma (Sierra Leone)working in Togo and Kenya and Jared at Global Aviation International global shipping company limited in Kenya?
Sabastien claim ha have gold in Sierra Leone (Goldmine), Togo, Guniea and Kenya.
Jared say he have Sabastiens gold in Kenya at bonded warehouse.
Kevin Stuart07-Jan-2015 21:10KOBBY IMES VENTURES LTD in Ghana is fake
Alhaji Seidu Sakaa and his so called wife Laila are fake gold dealers, super scammers they have dupe many prospect gold buyers million of dollars, our investigation at Ghana Register General Department shows that he is not the owner of Kobby Imes Ventures Ltd but he claimed to be CEO,
any one that want to gold must first inquire from Ghana Mineral Commission and PMMC to know the procedures, any price that is cheap is FAKE.
Sure07-Jan-2015 20:58Valor Investigating Solid Security (K) Limited
Is another big scam. They will do fake Due Diligence and redirect you to a fake company.
they are linked to a certain Bradley Nelson who is also a big scammer wanted in the US for drug scamming.
Stanley lewis07-Jan-2015 14:35anyone know of a paul nana yaw sarpong, paulnanayawsarpong@yahoo.com, CONSORTIUM GOLD GHANA LTD,
BLOCK N0 9, PREMPEH STREET, KWASHIEMAN, ACCRA
PHONE: +233 (0)277278139
Guest03-Jan-2015 10:49Has anyone heard of Bradly Nelson was based in Tanzania and now in Kenya, Gulf Gold group?
Can anyone advise if this gentleman is trustworthy and has done business before?
Sydney28-Dec-2014 12:11
We have been following this forum and we can assist many buyers who been scammed or are in the process of dealing with companies purporting to be selling gold we can check them out if they genuine licensed dealers especially here in East African region
If anyone has been scammed in East Africa in gold dealings or intending to invest in gold from East Africa, please feel free contact us in person,we shall give you an up date on all their activities in East Africa. And if you decide we handle all transactions on your behalf since we are experienced in this region in private investigations and handling valuable goods. We can also assist you in recovering your stolen monies.
At Valor Investigating Solid Security (K) Limited, our core business has always been security services. With advancements in technology and a changing security environment, we now offer integrated guarding to enhance our traditional security services. We help improve your security with confidentiality and anonymity.
Combined with a national recognition and over 6 years of experience as the preferred investigative agency in the Kenya, Valor Investigating Solid Security (K) Ltd has earned respect, success and accomplishments by providing clients with confidential and professional services. We have the capability to handle any case quickly and efficiently.
Our employees range from trained former police and CID officers with integrity and best recommended by the Kenya police.
Our current permanent staff is 17 members.
We are operating in all parts of Kenya and moving to the rest of the region.
Our company is registered under Kenya laws.
Guest21-Dec-2014 17:19Has anyone heard of crossover security in Kenya.
Also, Global Aviation Authority of companies. It has been mentioned earlier but not what they had done?
Any information gratefully received.
nkumbi10-Dec-2014 11:33Hello All!
Any buyer who plans to buyer or export minerals in Tanzania I will guide you in proper procedure and steps how to conduct it. Thanks
nkumbi10-Dec-2014 11:26Anyone who needs verification please feel free to contact me. Thank you
John10-Dec-2014 11:04Hello All,
Sad to see all Business/Investors Losses Trust, I?m from Tanzania, I will guide or assist you with the procedures of how to export and process government documentation feel free to contact me.
Pinikitan06-Dec-2014 13:59And yes mamadou Yallo from Gambia is for over 10 Yaers the biggst Gold Scammer in Gambia this Guy has every Week a criminal Case at the Court. And all his Gold Shops are Scammers in Gambia.
Pinikitan06-Dec-2014 13:58We need any real Info about the Prisam Agencies Ltd Tanzania and Mr. Pino Kabila
guest04-Dec-2014 17:19Name: Charles Tunnel
E-Mail: jetstonesjet@gmail.com
Phone number: +233 24?7593581
THIS GUY IS A SCAMMER AS WELL!!!!
Ken Wright03-Dec-2014 20:32Guest aka David Nugent is a time waster and liar who wants to taint people bad image if they see through his scam and refuse to work with him on scams.
Guest02-Dec-2014 11:31Hi Quin I know of a Bradley
Guest01-Dec-2014 22:47Can u tell me if Wendy Awal is a scammer?
Quinn30-Nov-2014 07:28Has any body heard of
Bradley Nelson
From golf gold & jeweleries group
Kenya?
Sandra27-Nov-2014 17:02Hi has anyone heard of Groupement de Cooperative Miniere de Kaiko in Mali? Are they scammers? Please let me know. Thank you
son25-Nov-2014 04:33Scammer work in indonesia and malaysia
- name : mohamed toure
- passport no : R0294883
- email : touremohamed7777@gmail.com
He work in indonesia and malaysia.
GOLD AND DIAMOND SCAMS24-Nov-2014 13:57SCAMMERS WITH SERIOUS CONNECTIONS IN KENYA FROM CUSTOMS THROUGH TO REVENUE AUTHORITY
(This Report was sent to me by one of their Victims after they took 139,000usd and another demand of 50,500usd)
1. Benson Muhanji Mageta
Owner of Manpower Trading Co.
All the Certificates of the product is ?booked? under his company and the product is even in a Safe Keeping Facility that does not exist (Cross Over Security).
Benson?s Contact details: +254716260360 , +254202323256
Email:mtrhdirector@yahoo.co.uk
2. Jared Kiasa Otieno
Owner of Global Aviation Shipping International. Jared is the guy that is linked to Former Minister Odinga. This guy has a lot of connections and once he is introduced to the transaction as the shipping agent everything starts going in a different direction and this is where the lawyer is also introduced to use his Escrow account for funds to be paid in.
Jared?s Contact details: +254775588882, +254715588882
Email: gblaviationintl@gmail.com
3. ?Eric? Moussa Gakunzi. This guy is introduced as the son of a General in Congo in the Bunia district. Can ?barely? speak english and he is appointed by his ?father? as representative of the community. He disappears once in a while when he goes back to Congo to report to his father, but he was traced in Nairobi the time claimed he was in Congo.
?Eric?s? contact details: +243995014847 , +254 752524248
Email: m.gakunzi@yahoo.com. ( every mail send to this address comes back as a invalid email, even though he sends mails from this exact address)
4. John be Good. This guy was introduced as a General from a community in Congo as well(can not recall what community). Also resides in Nairobi and we only met once right in the beginning. I do not have any contact details on him.
5. Thomas Okundi the Lawyer. This guy plays his part really well. Keeps his tracks clean and then assure that nobody else is exposed. His wife works for the Kenyan Government and im sure that is one of the connections they use. He is also directly linked to Former Minister Odinga. This guy is a master mind and a huge advantage to all the above mentioned because he knows his way around the law and government contacts. He even threatened me to get me locked up if I dont give them the $50500 that I collected. Wanted to make sure I stay in Kenya with no way out, but I was one step ahead.
Thomas Contact details. +254 722973060
Email: okundi@okundiadvocates.co.ke
THANKS.
guest0812-Nov-2014 10:45In response to Guest aka (David Nugent)
Sailin Sheth, Michael Green, Darren Pollard are NOT Scammers. David Nugent has been running around telling people he has clients in Hong Kong which he sells 5,000Mt copper per month to. I?ve spent a good 5 months speaking to him without any deal going through. DAVID NUGENT IS FULL OF SHIT! Ken Wright you are spot on.
andy cross29-Oct-2014 17:16have you heard of a justine ashley k owusu claiming she has 120 kg of gold in a security company she has given me the name of timothy asare to contact re this gold
email for him is barristerasare500@gmail.com
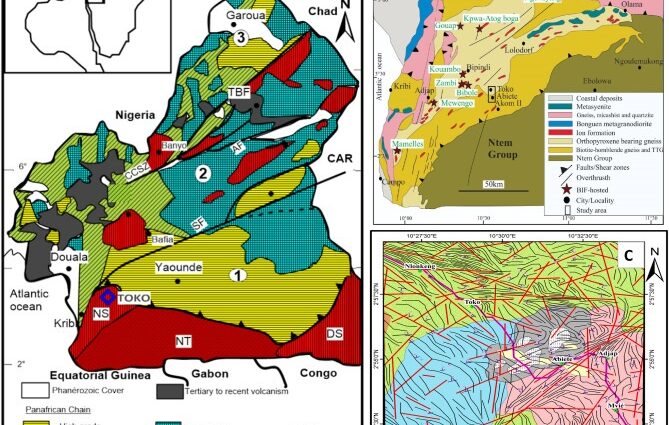
marie porilo27-Oct-2014 20:51Does anybody knows if commetals LTD is real and if the cooperative Tikum miners actually exist in Cameroon?
Guest25-Oct-2014 06:55Company Name: GIBSON MINING COMPANY LTD
Address: No 34 Tudun Wada Road, Gold House, Achimota, Accra Ghana
City: Accra
State: Greater Accra
Country: Ghana
Tel: +233549819848
e-mail : richards.mike32@yahoo.com
DEAR SIR,
I WAS DECEIVED BY THE ABOVE-MENTIONED COMPANY FROM GHANA THAT CLAIMED TO BE A GENUINE SELLER, WHEREAS THEY ARE A FAKE. THEY SELL GOLD DORES THEY DO NOT HAVE. THEY EVEN REFUSED TO SUPPLY US WITH THEIR COPY OF LICENCE TO EXPORT AND THEIR COMPANY REGISTRATION DOCUMENTS AFTER A BUYER FROM GERMANY HAD SIGNED THE SPA DOCUMENTS. FOR SAKE OF PROTECTING INNOCENT BUYERS, POST THIS SCAMMER ON YOUR WEBSITE.
REGARDS
MANDLA SHONGWE
GURA.H.Z24-Oct-2014 15:57SIR
CAN YOU CHECK THIS NAME IF HE IS CROOK OR NOT
KONO VILLAGE GOLD MINER
Address: 20 faddy Kono district
Email:sonatesidiki@gmail.com
Telephone:+23277831679
SIERRA LEONE
HASSAN.Z24-Oct-2014 15:45WHAT IS THE BEST WAY TO BUY RAW GOLD ?
TO DEAL WITH MINERS THROW LAWYER AND OR TO VISIT THEM AND TO DEAL DIRECT
Guest23-Oct-2014 12:25Sailin Sheth, Michael Greene, Darren Pollard all work in league with Samar Kambale. See note below.
Be aware of Cooperative Miniere Dekisenge, their ?headquarters? they claim is B.P 342, Kolowezi, Katanga ? DRC. This company is not registered with the ministry of mines in Congo, they are operating illegally and trying to sell ?gold? in Lusaka,Zambia.They expect buyers to pay for the TTI costs and pay for their Operations Director ? Samar Kambale Hussein? to fly with the gold to the destination. But they won?t show you all the documents, and their agent in Lusaka ? Mette Chishimba from Guardian Cargo Ltd or Suleen Investments in Lusaka,Zambia, he is also part of this scam. The CEO or Director for Cooperative Miniere Dekisenge is Zagabe Kimputu, and his secretary ? Jean Marie Kapenda. DO NOT DEAL WITH Emmanual Kazali and Samar Kabale they are all Congolese and big time scammers operating out of Zambia. They do not have gold!! copmindekisenge@gmail.com, samar.husseink@gmail.com, emmakazali@yahoo.com
Guest22-Oct-2014 12:36Sailin Seth +44 7881020743
Phillip Chibundi +260966888080
tony (sailin partner) +44 7448349953
Nanou +24399 5223310
Obid +260 972002565
Darren Pollard (London Select Academy) +44 7990038216
All scam artist, claim to be trading in Gold and precious metals. Advance money scam
Guest22-Oct-2014 12:24In response to Ken Wright, David Nugent is not a gold scammer but is someone who has brought a lot of attention on scam artists from UK and Zambia. He has shone a light on Philip Chibundi and his practice of scamming people as well as Salin Sheth in London as well as Laurus Trading and VVV Trading.
Ken Wright20-Oct-2014 09:17David Nugent of Ireland is a Gold Scammer promises that he has contacts in africa but not true as he is in league with the scammers in Zambia and Tanzania.
Guest15-Oct-2014 21:39This has nothing to do with gold, but do you know of a Gregor Alexander who states he is the Investment Controller of Business Assets Ltd in UK?
Guest09-Oct-2014 05:59We therefore strongly advise to keep clear of MEI, BERNARD KAYONDO, COMMODITY EXCHANGE LIMITED and BUPE CHIPANDO?
Guest09-Oct-2014 05:57WARNING TO GOLD BUYERS/INVESTORS ? Stay clear of MINERALS EXODUS INTERNATIONAL LIMITED run by Mr. BERNARD(BEN)KAYONDO in KAMPALA, UGANDA. This company promotes itelf as a gold clearing agent. They will give you all the detailed costs of what is required to clear your shipment out of Uganda to anywhere in the world. Within 24 hours of receiving your money you will be advised there is an unforeseen problem and they need more money. They say they cannot return your investment as it is already spent on the progress they have made. In our case the investor had no more money to advance so he lost US$25,000. The reason given was because the supplier had not supplied the correct import documentation bringing the gold into Uganda and therefore they needed more money to cover the full amount declared on the import document, which was more or less 4 times the original US$25,000 advance. BUT, prior to advancing the money, there was no problem with the incoming documentation and MEI categorically stated they would have no problem clearing the required amount, as per the agreement, out of Uganda. Of course they will offer to partially contribute to clearing the shipment but not enough to cover the whole required amount. They will still expect the investor to add more of his own money. It is a clever scam and we believe MEI and the supplier, Mr. BUPE CHIPANDO of COMMODITY EXCHANGE LIMTED registered in Zambia, were in partnership with each other to scam the investor. We therefore strongly advise to keep clear of MEI.
Maurice Bromley09-Oct-2014 03:19GUEST MESSAGE ? Avoid dealing with Minerals Exodus International (MEI) of Kampala, Uganda. Their MD is Mr. Bernard Kayondo. MEI poses as a gold clearing agent and will guanratee to ship the supplier?s gold out of Uganda. He supplies you with full details of the expenses yo u are expected to advancein order to do the clearing. Within 24 hours of receiving money from the foreign investor he comes up with an excuse as to why not enough money has been put forward and in order to complete the clearing he needs more. Our investor put up US$ 25,000 and was unable to put up more, so lost all his US$25,000. MEI said they could not refund as the money had already been spent. We believe MEI and the supplier, in this case COMMODITY EXCHANGE LIMITED registered in Zambia and represented by Mr. BUPE CHIPANDO, are in partnership with each other to scam. We therefore advise potential investors/buyers to avoid this pair.
Glenn Francis05-Oct-2014 06:44Hello, Can someone tell me if Dr Dennis Mensah from Accra in Ghana is for real, he is offering to fund my gold mine project in Canada to the tune off $7 million dollars.
He is acting on behalf of the wife and son off the former President of Ghana
Cheers Glenn
Hugo26-Sep-2014 16:49do you have the details from Mr. DR. Michel Morrinson from canada ?
Guest25-Sep-2014 11:25I keep getting ads on Facebook: Start your own goldmine in Africa for 20.000?50.000 dollar.
When you click it, all you get is a form to fill in your REAL (???) name and email.
Scam??
GOLD AND DIAMOND SCAMS25-Sep-2014 09:21These guys are time wasters and scammers, beware of any offer coming from them:
Name: Liem Dang
Skype name: Liemdang62
office nos 4126537777
Cell 7249103446
email:neymarglobal@yahoo.com
Company: Ubiquitours Trading Ltd
Name Emmanuel Coker
Address: Ratoma Centre Secture Plateau Conakry
Mobile:224 631678444
His partner?s name is heritage miners also on linkedln
Name is Mamadou Bar
Skype name: mamadu009
Tel: 224 622906144
Raja Adul23-Sep-2014 05:37Time waster based out of Miami who claims to trade diamonds and gold. His name is William D Diltz with kw investments.
david thomas appears on his email which is a red flag!
kwinvestments.wd@aol.com
jose21-Sep-2014 21:40Has anyone had dealings with a man named Mr. Kweku Bo, he is a gold seller in Ghana?.
Fred18-Sep-2014 20:26All Beware of Jacqueline Macton claims to be a USA citizen that resides in Ghana, all her claims are false and she works with others with different email address. Thanks for this site very good to check scammers.
Michael17-Sep-2014 21:47PSC PANDIC SECURITY COMPANY IN ACCRA GHANA claims they are holding 48 kilo?s in gold from new
skype-met friend who says she owes 6K in fees to get it out
mahadev16-Sep-2014 16:31Park jun (pj gold) dont trust him, thank god we got to know before it was too late. Its some African fellow pretending to be a korean.
Guest11-Sep-2014 08:06Phillip K Chibundi,
Chibundi and Co
Legal Practitioners
Unit CL1
Stand 483
Kudu Road
Kabulonga
Lusaka
Zambia
Ph: +260211848015
Mobile: +260966 888080
This man is working with gold and diamond scammers. He will claim to be honest but is not. Parcels due to be handed over, will be delayed, appointments missed, turned up drunk to one meeting which he wouldn?t hold in his office so his scam wouldnt be caught.
Others involved in gold scams
Nanou
32 Avenue Gambela
Lubumbashi Katanga
His company is MH Holdings 8647 Mwepu 2nd floor
He is also the youth national president for SCODE
Guest09-Sep-2014 18:06A fraudster calling himself Liberty Commodities LLC offers CIF gold dore so called name Victor Ingram Email libertycommoditiesllc@gmail.com.
Guest09-Sep-2014 14:44Gold Scammers in Lusaka and Ndola, Congolese nationals.
Mr Muchaila ilunga
Mr Phillip Chibundi (Lawyer)
Nanou
Obid
Alan
Scamming people in Zambia using 57kg of fake gold. Will ask for paperwork to be paid for then the man he will go missing then the lawyer will need $41k before releasing the parcel, its all fake
Joris08-Sep-2014 17:32A scammer who calls himself as Ernesto Marques, tries to sell large quantities of gold using the stolen name and passport copy of Mr. Timothy Ahlmer .
We spoke to Mr. Ahlmer who is still suffering from this identity thieft.
Always make sure you contact your seller directly.
buyer gold06-Sep-2014 05:53Be careful of seller?s gold at Tanzania.
We paid the money for free note and others but they can?t delivery.
Guest04-Sep-2014 10:38You have been scammed in Zambia I could be of help. How can I reach you?
Bev Jocumsen31-Aug-2014 23:56has anyone had dealings with a Pat Beadle or Anthony Lefale, with gold or gold filtration ststyms
Guest26-Aug-2014 23:39Attention to all Gold traders.
Please stay away from the following SCAMMERS:
1. Mineral Exodus International in Kampala /Uganda. The Director: Bernard Mwnaje Kayondo and his team are scammers. Very Organised Scammers. They scammed us US$25000
2. Commodity Exchange LtD: of Zambia, Director: Bupe Chimpando is scammer. Please stay away from him
Bupe poses as a supplier and Bernard poses as a clearing agent. Both have scammed over US$500,000 from 3 different buyers.
both these groups should prosecuted. if you can help find them and put these scammers to justice, please help.
Guest26-Aug-2014 12:06Beware of Aaron Bentil, +233554096168 as he is a fake
Name ? david cesil & tommy / thomas
Place ? namibia & south africa
Number of people ? 2
Phone number ? +264811287114 /
+27730037766 / +27731442865
Skype id ? davidrough22
jackson14-Aug-2014 10:16am jackson makoha ,this funn guy from south africa is real scammer and time waster he send me to fake seller
Phil12-Aug-2014 13:26Has anyone found GOLD LTD of Tallahassee, FL. to be fraudulent? I have been wiring them money for three years.Their website is howtobuygold.biz.
Lucas11-Aug-2014 20:22We are relaible Gold suppliers. We have Offices in Tanzania, Nairobi and Brussels. Kindly contact us for any interest.
radam.investments
Mike Hanen07-Aug-2014 13:55Has anyone had dealings with a woman named Theresa Padi (claims to be a US State Dept employee in Accra Ghana)?
She claims she has 11.76kg of certified gold bars in a safety deposit box in an Accra Bank and needs help getting it shipped to the US. Also claims all Mining Commission docs, and Customs Exit Permits are legitimate; done, and stored with the bars at the bank.
Let me know please
Jacaues Ninzi06-Aug-2014 01:40Hi there,
Thank you for these heads up.
I have also been scammed but guys from uganda and DRC.
If you are happy for me to add the names, please let me know and I can e mail you all their details.
Thank you!
GOLD AND DIAMOND SCAMS30-Jul-2014 16:14DIAMOND SCAMMER FROM CAMEROUN:
PAUL FON
TEL: +23778266649
Email: paulfon342@yahoo.com
Skype: Paul.fon1
ANOTHER GOLD SCAMMER
Jallon Mohammed
Tel: +22966575255
+23376636927
Email: jallonmohammed@yahoo.com
Skype: jallon.Mohammed
Found out on linked he scammed another buyer ticket and Dubai visa.
His name is on on the Internet he is a scammer.
We lost money on the ticket. He shipper arrived in Dubai and disappeared with no gold
jonson26-Jul-2014 03:16fann the guy from south africa he scammer he send buyer to scammer after hammer he need cummision
ruchira bhatia25-Jul-2014 04:34
All are scamers be aware
Min cam
Kamara trading
Walter naganje
Cnk mines
Folanny alkindny
Karle hans
Devid batada
Fobella johns
Universaltrade export
Guest25-Jul-2014 04:25Scam alert : HE IS NOTHIN BUT SCAMMER FOBELLA JONES , IT IS HIS ANOTHER FAKE ACCOUNT BE AWARE
samuroch24-Jul-2014 22:48are the names Jacqueline Macton or Clement Asare known to anyone
mekosam72@yahoo.fr23-Jul-2014 15:21ghana is scammers country i.was been scamme by Bismark.Odhei.is.a.big scammer he work with 2 old people.they wich fack gold.and.used A.E.R LOGISTIC FACK REFINERY.THEY ASK TO PAY 7% FOR EXPORTATION TAXES.DON?T ACCEPT THEIR OFFER.ONLY WITH PMMC EVEN.THAT.BE CAREFUL.
SAM
Keith21-Jul-2014 02:06Is Barrister Michael Asante of Power Security Company Limited a legal business dealing with gold.
Guest18-Jul-2014 10:49GOLD SCAMMER FROM CAMEROUN:
NAME: FOABEH CALEB FORLEFA
COMPANY: TAKUMBA MINERS BUAE CAMEROUN
EMAIL: warehouseproduction2010@gmail.com
TEL: +23773069065
Poirot15-Jul-2014 20:24All gold scams. Details posted on 419scammersexposed.com
akarminerlametal.org (Gold scam)
goldfingerghana.com (Gold scam)
sinobandgoldcom.webs.com/ (Gold scam)
pjgoldltd.com/ (Gold scam)
fgincltd.com (Gold scam
honnymines.com (Gold scam)
comcastminingghana.com (Gold scam)
ngminingltd.com (Gold scam)
sudkivugoldmines.com (Gold scam)
fanie09-Jul-2014 09:44Jan van Bruggen???Sellers and Buyers please do not do business with Mr Jan van Bruggen from Netherlands as he promise Buyers that he is the seller. At the end of a long up and down mail war he is just asking for money to be paid to him . He sends Fake documents via the Internet and never comes up with the real stuff . He will keep you going days on end with SKR and fotos of him owning the product but he is never true to his word . He starts of saying he is the financier and at the end of the day all he wants is for you to pay for his own gain . Mr Jan van Bruggen will then come up with a story that his money was scammed and that he needs some assistance in getting taxes paid. Please do not pay this man any money as he is a class act scammer. Not only does he operate out of Ghana but also out of Tanzania..
Fanie09-Jul-2014 09:24Jan van Bruggen???Sellers and Buyers please do not do business with Mr Jan van Bruggen from Netherlands as he promise Buyers that he is the seller. At the end of a long up and down mail war he is just asking for money to be paid to him . He sends Fake documents via the Internet and never comes up with the real stuff . He will keep you going days on end with SKR and fotos of him owning the product but he is never true to his word . He starts of saying he is the financier and at the end of the day all he wants is for you to pay for his own gain . Mr Jan van Bruggen will then come up with a story that his money was scammed and that he needs some assistance in getting taxes paid. Please do not pay this man any money as he is a class act scammer. Not only does he operate out of Ghana but also out of Tanzania..
Guest04-Jul-2014 10:09this is one more scammer from Tanzania. they let you test the gold and give the collateral also, show all the documents, export /red letter. but they ship you nothing.
Company Name: Pixel Metals & Minerals Ltd
Represented by: Mr.John Hugo
Passport No# : AB 365995
Physical Address: P. O. Box 31892, Makonde Street, Mbezi Beach, Dar es Salaam
Tel. No.: +255 22 2627316/255787209156/255787077128 Fax: +255 22 2627047
E-Mail: hugo@pixelminerals.com
Brett03-Jul-2014 09:52With regards to Ben?s comment above regarding ALISON LEE WAGNER. She is now using the online flatmate search for Australia.
jan van bruggen28-Jun-2014 14:40NOT THE SELLER IS SCAMMER, BUT ALSO MANY BUYERS FUCK THE SELLER
1 SELLER FUCK OCEAN LINK GROUP GHANA
THIS SELLER SEND 14 MAY , A CARGI WITH 1 G GOLD TO CHINA, HONG KONG .PICE USD 28000 KG , SHE NEVER PAY , VERY BAD BUYER , MUST ALSO ARREST HERE VERY SOON
COMPA NAME : LE MARS GOLD (AUSTRALASIQ )
MAIL: marcelle@lemarsgold.com
phone : +85269528993/+85281926916
Marcelle.ma Le Mars Enterprise Ltd (Austral Asia )
very bad buyer ,
I?m client off oceangroup, mr kweku bo is very correct guy m so put him out this blacklist and blame his name , and paint Mrs marcelle name black
gr jan van bruggen
jan van bruggen27-Jun-2014 10:46fanie Steyn from south afrika
time waster
false information, he have buyers , send /show his ticket , he promise everything
he never come
i stay 6 weaks for bull shit in tanzania about this crazy internet scammer
he make every bpdy crazy , tell in skype he is trade community ., that you have high groups off peoples
he have nothing
please don?t contact this scammer .
jan van bruggen
jan van bruggen27-Jun-2014 10:44katanga Export & Import scam me for ?14700
i was in the office , the security force come wth 40 kg , Mr Edwin Josuha collect 10 kg out off the box, i was there, we weight , exact 10 kg .do inside the box , we come in the office , sign contract , i pay ?14700 incl melted . i sleep 2 night with the box off really 10 kg gold in my hotel room, i never run out , when i know all before i bring to raffinery hear in dar es salaam , melted , and mone to my account in europe , now he fuck me
we come after 2 days back with the gold , we melted . i see everything , make pictures , i was there with 2 another guys for the check, total 10 peoples . after melted we come in the office off this seller , i thought , he give me the 1 kg collecteral, confirm the contract !!he show me the documents, export /red letter stop, only acceptable when we pay for the 40 kg , usd 50000 more .he sealded the box, give the key to me, but what is key right now
he run out side with the box , 5 peoples stop me, about i claim my 1 kg
so he fuck me for this money , i send mail he said , he send 1kg with dhl to europe, nothing is happen
so please how we can stop this criminal edwin josuha !!!!
damas mahoni also . he send me to this crazy seller , all was fine he promise me, i stay now 5 weaks longer in tanzania, looze all my money where i so hard for working last 2 years
i need that interpol off fbi arrest this guys
mail me : africantimber50@gmail.com
skype : africantimber50
mobile holland : 0031620825233
Geoff Kenny24-Jun-2014 12:15100% SCAMMER USING FALSE PASSPORT
Robert Jackson
Mississippi USA
Passport: P/USA/404704863
Galaxy Trade Invest ? Gold Offer
Mail: galaxytradeinvest@yahoo.com
Skype: galaxytradeinvest
Tel: + 221 777 378 425
Dan22-Jun-2014 16:13A scammer using the stolen identity of ALISON LEE WAGNER (email: allygner@gmail.com) from USA claims to have inherited $394K in gold bars from her father in Malaysia who just passed away. This scammer is well trained in psychology, has an elaborate story and works to gain your trust. She claims to have a step mum who is illegitimately trying to claim the inheritance for herself and after befriending you online she asks to have the gold transferred to you?re address where she hopes to meet with you and give you a reward of $35000 for doing so. For this she needs $5000 to be sent to to a given account to finalise courier payments
1. RTAE_METAL IN COTONOU
Djeveso pierre is the executive
Emmanuel sognonou director
Mohamed Tour? , the self-styled seller
Emmanuel Sognonou 00229 96898460
tour? mohamed 00229 97 960868
djeveso pierre 00229 95 409303
Email: Rtaemetal@ymail.com
2. Paul Mulenga of Guinea Conakry
email: mulenga006@yahoo.fr
Tel: +224 666473300
Hassan16-Jun-2014 15:54Hello,
If you are looking to buy gold in Ghana kindly contact me for details
and what we have available. We have gold available now both on FOB and CIF basis.
Minimum quantity is 10kg for CIF
Maximum quantity is 50kg for CIF.
Minimum for FOB is 20kg
Maximum is also 50KG.
Thanks
Email: goldprospects@outlook.com
eroberung10-Jun-2014 20:57Hello All, Anyone Know About Fin Vault Security and Mr mac Harrison Kwame?
Guest07-Jun-2014 16:37Anyone familiar with the names Robert Kelly? LGCY 5000? Stephan Munguti Kathaku?
Please advise good or bad experiences.
GOLD AND DIAMOND SCAMS07-Jun-2014 11:00To search if a company or name is on this scam site, kindly hold
the ctrl key and press F key on your keyboard, then type in
the company name on the find page below.
ctrl + F = Find in page.
Trolli04-Jun-2014 08:19Be aware about the following GOLD SCAMMERS:
MR. CLAUDE SHABANI MORISHO, with date of birth : 06.12.1950 and Congolese (RDC) passport number OB0572160
MR. (HARRY) HENRY SIKAZWE FROM ZAMBIA, with date of birth 22.10.1972, Zambian Passport number: ZN000983
MR. VICTOR F. BEMBE , TANZANIA PASSPORT AB348866
MR. JONES MASUNGA TANZANIA PASSPORT AB426789
Company RIVA GOLD CO. LIMITED MWANZA (TANZANIA),
Company GOLD & GEMSTONES TRADERS COMPANY LTD MWANZA (TANZANIA),
(Be warned, signed Contracts mean nothing to this persons)
Following crimes will be reported to Interpol, Europol, the Authorities of Tanzania, Kenya, Zambia DRC and South Africa and to the Highest Authorities of UAE and Bahrein:
1. Requirement of upfront payments to clear the Gold for export and through Customs, and after receiving showing ?the official needed documentation? the Gold was never delivered.
2. Falsifying of official documents and certifications
3. Provoking ? circumstances? to have reasons for further money requirements, always promising to deliver the Gold
If you are unwise enough to enter into a ?business? you will lose a lot of money because the only intentions of these Persons are fraudulently intents.
Ignore any emails or phone calls from these persons and companies. The only traders to profit from these transactions will be the Gold Scammers THEMSELVES.
PLEASE FIND ATTACHED THEIR PASSPORT COPIES AND A LIST OF THEIR E-MAILS AND TELEPHONE NUMBERS
harrysikazwe72@gmail.com, skype: jumamu4, Tel.: +2609776100174, +260968677268, +260975591240, +255688049874, +255784047074, +254733951254,
mandevu1958@gmail.com, skype: shabani.morisho, shabani.morisho1, shabani983, Tel.: +260974610126, +254737544997, +255787370571, +255713314199, +243977433364,
CHAVOT-DUPIN ETIENNE03-Jun-2014 17:05URGENT INFORMATION
I am Etienne Chavot-DUpin from France, I had to change my passport as someone in Cameroon is camming people using my previous passport copy. A claim as been made in Cameroon against X as I do not know his ID.
People who want the proof can get in touch writing to e.chavotdupin@gmail.com
The guy has a fake Facebook account, Viadeo fake account, hhe is using Email:mr.etienne1949@gmail.com
skype:mr.etienne123
My personal SKype ID is pdm.ecd
ellesram03-Jun-2014 09:03BEAWARE OF SCAMMERS!!
OCEAN LINK MINING GROUP
REPRESENTED: GEORGE KWOFIE / NANA TABIRI YEBOAH
#5TH ABOMUSO ROAD,, NYAME BEKYERE BUILDING, AKYEM ODA, GHANA
email: OCEANLINKMININGGROUP@YAHOO.COM
TEL: +233 246?895315
Horrible horrible people! FAKE EXPORT LICENSE AND WILL LURE YOU IN TO SIGN CONTRACTS AND CHANGE TERMS LAST MINUTE and NEVER DELIVER GOODS;
Name: Souleymane Camara
Company: Apex Sarl
Location: Conakry, Guinea
Associated Phone Numbers: +224621767760 or +224622759554
Associated Email Addresses: globallibertygn@gmail.com apexsarlsiss@gmail.com
gemtradeafric@gmail.com
Africagems.com
011 27 (84) 7571497
Skype name: mmanda1
Name: Dean
Paid his air ticket said he was short money never showed up to travel was a scam.
Scamwatch02-Jun-2014 02:03Please watch out to buy diamond & gold from Africa ( especially, Namibia ).
This Scam advertising on many famous web sites,
ex. India Mart, Hello Companies, Linked In, Alibaba, and so on?
They( Clime group ) are using many names, adresses, phone numbers, E-mails.
That it has become clear so far, is as follows.
* The real name of one person is : Tukondjeni Iita ( Namibia or Angola, South Africa )
* Advertising with Fake name
KAPIA HENRY / HENRY SANKO / H diamond / Moses Exporting CC ( Moses Kapia ) / Alex Palmeria / Shafa Kaulinge / Namib Mining Consolidated / Company Usher Trade Pty.Limited ( Jason Carlito ) / Ludaritz Diamond Mine / Al-maz diamond company ( Thambo Santos ) / Aluta diamond Mining Company / neto deal diamond trading company ( frank neto ) / gem diamonds / diamond works cc / sanchez diamond / Northern Namibia Diamonds Company / gems diamond pty / adrian van breda / Fran Diamond Trading Company
* Phones ( can be connect some )
+264 856?337766 / +264 855?606583 / +264 81?2114233 / +264 81?6353361 / +264 814522460 / +264 8180?39155 / +264 856?160117 / +264 81?8715490 / +244?925367?646 / +244?912637748
*E-mails : druu20055@yahoo.com / santosalex1888@gmail.com / caratsd@yahoo.com / mosesgold22@yahoo.com
* skype : milko.verga / moses.maggai
* twitter : frank@druu20055
Please be trading it after research well.
Before the transaction, to reserch the company name, phone number, address, E-mail adress.
Guest25-May-2014 09:09Guest.
Stay away from scammer and frauder in Accra, Mr. Nimako Paulinson Wilberforce and his 2 brothers, Hi ask you about some business selling gold, and at the end you lost your money fro nothing! They ask for payment in advance, and works with Gold Shop Ghana and with Global Link Logistik & Shipping company, they work also with A A Minerals, but don?t trust any way, because they will not send you any gold!
1. GOLDEN AGE MINING CENTRE
2 BOAPOSEM STREET NANA KOFI HOUSE ACHIPEM GHANA
TEL: +233232496698
EMAIL: gageminingcentre@yahoo.com
RPRESENTED BY: MR KWAME AKYEMPEM
PASSPORT NUM: 706004572
2.ITALTEC GHANA LIMITED
P.O. BOX GP 17482 ACCRA GHANA
TEL: +233302544094/233244965997/233244418822
EMAIL:italtecgh@yahoo.com
REPRESENTED BY: KWAME OFEI (CEO)
3. FREQ MINING AND MARKETING COMPANY LIMITED
P.O.BOX CC 953 CAPE COAST GHANA
TEL: +233200916867
Mob: +233262664450
EMAIL: INFO@FREQMININGGHANA.COM/FREQMINING@GMAIL.COM
WEB: FREQMININGGHANA.WEBNODE.COM
REPRESENTED BY: FRANK ANOANOH
PASSPORT NO: H2465380
4. TRADE LOCAL MINERS (GROUP OF LOCAL MINERS) ? not sure yet and needs to be identified.
35 Rue Road Bertoua, Quest Street Cameroon
Tel: +237 98651247
Fax: +237 22246598
Reg No. RC. EUA.2006.B..034
Tax Payers No. P042379809876Y
Contact Person: Helena Besong (+237 9498 5255)
Email: helenabesong2000@gmail.com ? Sales Manager who we spoke with
CEO: Dondy Syble Teclaire
Guest19-May-2014 17:13Hello Sirs,
I have been scammed and stolen by thief by thes fake seller from Burkina Faso,
I want to give their names an phones to d?ont be scammed like me.
Moussa Sana +22673416664 negociant.inter@gmail.com
Ibrahim Sawadogo +22670641919 +22670876060 +22678700105
ladies, gentel man, becarfull and think 1000 times before going to make any commerce from Africa, ther is no law, everything is corumped ( police, trubinal, minsters?.) everything.
it is a jungle and not human like us.
regards
walid
jane14-May-2014 13:18dpes anyone have any idea if this copany is real
e also like to know if this person is real and if he is really a Mandate for oil company in Russia, his name is Evans Bulkin, company, resurstsentrgaz, ltd resursTsentrGaz.ltd@bk.ru
+79685339751 (work)
if before my boss deals with him we are doing a due diligence on him and his company.
admin group12-May-2014 10:33NEVER EVER PA EXPORT TAXES IN ADVANCE,AND ITS BETTER TO PAY FOR THE GOODS AT SOURCE, ON FOB BASIS, THEN SHIP THE GOODS OUT WITH SELLERS EXPORT LICENSE.
IF SELLER DOES NOT HAVE EXPORT LICENSE THEN HE HAS NOTHING!!
Todd08-May-2014 07:23@Frank, I was in contact with this security company when I was in Ghana, they are reliable and not scammers. Thanks.
Me07-May-2014 12:51WARNING-WARNING-WARNING:
Name:GILDAS CHARPENTIER
E-mail: transiteur@orange.fr
Tel: +33 641 937 237
You can check is profile on Linkedin.
Fake proof of funds from HSBC, timewaster, liar, intermediary who makes a lot of promises, but never cope with them! provide fake documents did have problems with the French authorities, the last one has been in 2009. Be careful this guy is putting people in troubles. He has no cash at all even if he present himself as investor. He says he doesn?t use Skype for contacts but has a few etc.
R Barry05-May-2014 14:09To concerned from 13th April 2014,
Nina Brown is a convincing scammer who will try everything to part your friend with his money. Tell him do not send her money under any circumstances and that the attached photos are not of the person communicating with him. I didn?t get scammed but played her along for a period of time just to see how far she would go with the scamming. Don?t get conned.
Asamoah05-May-2014 12:29Dear Sir,
We have up to 100kilos of gold and we work on through PMMC Ghana for both assaying, payment and shipment.
We encourage buyers to visit us here in Ghana for us to proceed to PMMC premises to conduct the assay.
Price is 37,000usd.
Asamoah
Email: nkanetetegold2011@gmail.com
Marco04-May-2014 17:59SCAMMER!!!!!!!
JIM KALUSHA ETS.COSMIC METALS 445rue des France TOGO
+22822200111,+22898608039 jimkalusha5454@gmail.com Skyp:Jim.kalusha
Marco03-May-2014 14:58SCAMMERS
STAN KISTER Passp.No02482104 Kudzai Goche Passp.No: DN022319
ZIMBABWE +263775091445
zimzend@gmail.com
SKYP : stanstan147
ellesram01-May-2014 06:50Rhonda. I have received the same offer! Can I confirm is it Ocean Link Mining Group or OCEANS link mining group?
Did you receive their FCO with stated address?
The one i received is 5th Abomuso road, Nyame Bekyere Buuilding, Akyem Oda, Ghana
Helen Williams29-Apr-2014 13:26Anyone been scammed by the following??:
Enock Koomsen
Lovia Mills
Scottish Security Company
Awuni Joseph
Roland Wanders
GoCrest Shipping
Michael Addo -Barclays Bank
BEV25-Apr-2014 01:21HAS ANYONE HAD GOLD DEALINGS WITH A MR PATRICK BEADLE OR ANTHONY LEFALE , STAY CLEAR THEY ARE DEAD SET CROOKS , AND ARE STILL PLAYING THEIR CROOKED GAMES GET THE NAMES OUT THERE
Rhonda14-Apr-2014 21:45I have been contacted on facebook I made as a friend named john morgan AKA miller said he own a mining company in Ghana called oceans link mining group said he well pay me commissions of 5000 dollars a kilo I he shippes the bars to me but I pay the shipping cost so I can get a buyer here to sell it to I sent me documents but I don?t trust him
Guest14-Apr-2014 10:11Please send me info on real gold sellers. No scammers. Any good person pls email me I have good clients who are looking for gold.
thabomokhachane@yahoo.com
Concerned13-Apr-2014 04:44If R Barry is checking in here since Jan. 2, 2014, I would like your input regardng ?Nina Brown.? Concerned that a very close friend is being scammed by this woman. Same crazy story of gold and needing money to cover insurance, etc. It?s obvious it?s a complete sham.
Armede12-Apr-2014 18:00Good evening
It is with a great pleasure that we contact you in order to
to share with you an opportunity and business for which we
are looking for a serious partner. Indeed, we are at the head
a company of Transit and consignment based in the Republic of
Benin. Our company represents and helps a group of Stampeders
Burkina Faso villagers; Chad and Ghana to sell metals
precious natural; mainly gold.
We have currently for the 300 kilograms of gold export
(TO THE) Gross whose characteristics are as follows:
_Form: Ghana
_Quantite: 300 kilograms
_Qualite: 22 karats +.
_Nature: metal (in the) powder
_Taux purity: 97% *.
_Prix: 20,000$US
Impurity composition: 3% (primarily iron oxide) buyer accepts the
offer and will sign a contract with the vendors, then will visit
Cotonou (Rep. of Benin) for finding on-site
effective of the goods proceed to its re-export. One delegate of the
sellers will follow the merchandise for the result of the Foundry. All
expenditure incurred by the buyer will be
deducted from the total amount before payment of the difference to the
seller This after the final result of the foundry. The Stampeders
peuvent provided by a 30 month period to 50 kilograms Gold. Then we
want to choose you as representative in your countries so that we buy
or you find buyers Gold regular.
complementary.
boland04-Apr-2014 10:44Do anybody know Agbor Festus Ambi from Cameroon. He states I need to pay a fee for buyers permit.
boland04-Apr-2014 10:40Gold sellers no scammers for Dubai required.
bolandsmithuk@gmail.com
Guest04-Apr-2014 10:36Urgently looking for gold sellers no scammers for delivery in Dubai.
bolandsmithuk@ gmail.com
Melvin A.04-Apr-2014 09:28I Have contacts with a reliable gold seller from Africa, He has been supplying gold to our refinery and I must say he is trusted and efficient in business.
Gold buyers looking to buy gold should kindly contact me.
Email: m_akridge@aol.com
Mr Melvin
Guest02-Apr-2014 17:52Hello
I just want to know if anyone had any dealings with the courier company virgin Atlantic courier services in USA and Jerry Anderson ? I think I am being scammed since they require all kinds of document like yellow tag and anti drug and terrorist certificates
Pepita29-Mar-2014 12:22Araga Local Gold Mines SARL in Mali; signed contract for delivery to Dubai, refinery guarantee in process then he wants US$37k in ?export costs?. Liar and scammer. Name of Director: Oumar Medideur.
ellesram29-Mar-2014 09:43SCAMS ALERT!!! CAMEROON?s BUYERS PERMIT!!
First he claims his name is Hons Jackson from Skype, using another name in email named edward Powell. He states that buyer can never buy any gold in central and west africa without the buyers permit and can be obtained both ways: 1) through them 2) through our own embassy ? it looks like they give you choice but we know embassy wont do this for you so you are only left with the choice to go through them..
they state the permit ranges from 2800USD to 8000USD, which our other associates company CONFIRMED THAT IT DOESN?T REQUIRE A PERMIT TO BUY GOLD IN CAMEROON?
SCAMS!
Guest26-Mar-2014 11:07Any body who gets approached by bacon miners company limited AKA bacon group or bacon group of companies THIS IS A SCAM ? they originate from Cameroon and claim the CEO is HENRY AMBE CHIE passport no: 01450545 dob 30.12.74 Skype name : Bacon Group. email:bacongroupofcompanies@gmail.com.
They will convince you to send $3000 for a buyers permit and get the ministry of mines to email you and call you. the email that comes from the ministry is : minimidt.depsa@execs.com this is also nonsense. We contacted the british high commission to confirm any need for buyers permit and it is not required in any way.
The other company that is trying the same thing is UNIVERSAL TRADES LTD cameroon
YOU DO NOT NEED A BUYERS PERMIT IN CAMEROON from the ministry of mines
Guest25-Mar-2014 12:50This website
WWW.FEDAG.COM is a scam website. Desist from dealing with him. His other emails are; inquiry@fedag.com, vivagroupultd@gmail.com. This company is fake.
The owner of this website is a big time criminal who has been plying this ?criminal? trade in South Africa, Uganda, Zambia, Malawi, Kenya, Congo and has accomplices scattered allover those countries. He has a small quantity of genuine gold which he uses to win the confidence of his victims, after that, he starts endlessly asking for money till you give up. Run away from him!
He uses the names Owen Ntege aka Bwire Joseph. Sometimes, he calls himself Craig Willis, or Garry. Do not send him any coin of your money.
Joan25-Mar-2014 09:083000usd buyers permit is a scam, there is no such thing.
Thanks.
Guest24-Mar-2014 17:21Has anyone had any dealings in Cameroon involving the purchase of a $3000 ?buyers permit? i have seen a number of people ask the same question but no reply as of yet
yusup23-Mar-2014 10:02JUDYB30-Oct-2013 21:01Does anyone know if the ?Emmali Company Ghana Limited? are scam artists? Please advise. It is most appreciated. I believe my mother to be involved in a scam
@Judy : They are top scammer
Guest23-Mar-2014 09:41JUDYB30-Oct-2013 21:01Does anyone know if the ?Emmali Company Ghana Limited? are scam artists? Please advise. It is most appreciated. I believe my mother to be involved in a scam
@judy : they are a big scam and please dont deal with them
Guest23-Mar-2014 04:36To the guy about Impex Gold, I know someone who is currently I the exact same situation, it?s a scam!
Guest22-Mar-2014 08:17sapavcentrac@yahoo.com
One of the liars from Ghana ? dont believe this scammer.
Richard Cole19-Mar-2014 23:48The lady named Iris Salazar is a great scammer from Mexico but reside in Riverside CA. He just scammed my friend Kelly of $700 and which is why we are on the look out for her. Pls be careful in dealling with her.
GOLD AND DIAMOND SCAMS19-Mar-2014 16:34Hello Jason, Please kindly contact the right government body in Togo to check on the company for you.
Hello Guest, I hope you are not being lured into romace scam. Kindly write me by email for details,
Email: noelmegumichan @yahoo.com
Thanks
Guest19-Mar-2014 15:59So I have one for you guys ? Impex Gold. This guy skypes me and shows me some gold bars. Story is this woman I met online inherited gold from her dad and the folks who have been storing it want $200,000 to release it. The guys name that is posing is gille jean robert. Someone look at the site for Impex Gold and let me know your thoughts!
Thanks
Jason T.17-Mar-2014 13:39Togo is a country in West Africa and is bordering Ghana to the west, Benin to the East, Burkina Faso to the North and its narrow coastline stretches onto the Gulf of Guinea in the South.
Where is Republic of Toga?
Jason T.16-Mar-2014 21:07Does anyone know ?Mr. John Adjovi? owner of company ?GTA Metals Import & Export?
out of Republic of Toga?? Thank you in advance.
Is there a search function for this excellent database??
Guest13-Mar-2014 15:50I am from Cameroun and there is nothing like buyers permit to buy gold, engage with genuine gold sellers and stop wasting time with scammers. God bless the person who started this blog.
ellesram11-Mar-2014 07:53We have been receiving a lot of offers from the Cameroon side for CIF transaction asking for buyers permit. They give you the contact of the ministry of mines. We asked who the contact person is and some of them gave us the names which are no longer working in the ministry or retired. I am not sure how to post on your website to notify all other people as well.
NKANGU MINING COMPANY -
http://www.linkedin.com/pub/nkangu-mining-company-ltd/44/803/411 ? FOR SURE SCAM!
Email: nkangugoldgood@gmail.com
Skype: leelee2690
Number: +237 79209300
The person to contact for the ministry of mines which we confirmed is fake because the person stated is retired and spoke with us to confirm this already! After I confronted why would the director uses a personal email address, he went offline on skype right away! He used a real name of a person that?s retired to ask us to go through interviews and eventually need to send the money to obtain the buyers permit.
Mr.Maurice Mouafo
Director of Mines.
Ministry of Industry,Mines and Technological Development
Department of Mines and Geology.The Lidap Property Storage House and
Buyers Permit.
Boite Postale 1604 2nd Floor Buyamasi Building Yaounde Cameroon
Tel: 00237 330 868 13
Email:mauricemauriceministryofmines@hotmail.com
2. TRADE LOCAL MINERS (GROUP OF LOCAL MINERS) ? not sure yet and needs to be identified.
35 Rue Road Bertoua, Quest Street Cameroon
Tel: +237 98651247
Fax: +237 22246598
Reg No. RC. EUA.2006.B..034
Tax Payers No. P042379809876Y
Contact Person: Helena Besong (+237 9498 5255)
Email: helenabesong2000@gmail.com ? Sales Manager who we spoke with
CEO: Dondy Syble Teclaire
I have attached all the documents including licence, spa, fco and she encouraged me to check her company as she claimed its 100% legititate and the buyer?s permit is 7700USD
Hope these can be posted to alert other poeple or to do more investigations to se if the second one is legit.
For the first one, it?s for sure not because we confirmed from the retired Maurice Mouafo.
GOLD AND DIAMOND SCAMS08-Mar-2014 10:55Hello Guest,
Please kindly do your due diligence from the right Government office in Tanzania, we dont have much information on these two companies.
Thanks.
Guest07-Mar-2014 17:45Please advice on legitimacy of ?Saad Bazie Saad? or company called ?MURU PLATNUM TANZANIA INVESTMENT COMPANY LIMITED?
Seller wants to sell Gold nuggets at significant discount from spot price.
Gregg03-Mar-2014 17:34Thanks for this list, very helpful.
Gregg.
Address Post Office Box Tw 60, Twifu Praso,C/R, Ghana
Tel: +233-(0)200?916?867
Frank Anoanoh (Manager)
freqmining1@gmail.com
FreQ Mining & Marketing Company Limited
4615 Discovery Dr Campbell River, BC V9W 4Y1,Canada
Gold River, British Columbia 253, Canada map
+1?250?999?5067
Dr.Freeman Quansah, President,CEO
Dr.Freeman Quansah
President,CEO
+233?266136869
John Quansah, Coordinating Director(Africa Rep)
John Quansah
Coordinating Director(Africa Rep)
CHIEF Nana Kwaku Boateng, Sales/Marketing/Promotional Manager
CHIEF Nana Kwaku Boateng
Sales/Marketing/Promotional Manager
+233?262120870
They are all scammers and should be avoided.
CP Spencer12-Feb-2014 21:14Has anyone been contacted by a Marri Coxz offering to ship gold from Ghana at her expenses.
CP Spencer12-Feb-2014 21:14Has anyone been contacted by a Marri Coxz offering to ship gold from Ghana at her expenses.
GOLD AND DIAMOND SCAMS12-Feb-2014 11:06Aloysius, if you cannot find the Ministry of mines in Cameroun then know its a scam and dont pay anything untill you confirm from the minitry direct.
Guest, What is Mr Jallow mamadou company name? Different people can use the same name, so asking about a particular name is a waste of time.
Thanks.
Guest11-Feb-2014 15:17Hello everybody,
did someone know about Mr. Jallow mamadou from Gambia?
guest08-Feb-2014 21:15is there an email e.djan@rocketmail.com? Person by the name of Djan Emmanuel, or Emmanuel Djan or Annang Djan Emmanuel?
Guest08-Feb-2014 21:13Anyone know of this email? e.djan@rocketmail.com , this mans name is emmanuel djan or djan emmanuel or anang djan emmanuel, is he real?
Aloysius Dalli08-Feb-2014 04:39I received numerous Gold offers from Cameroon on CIF basis, however, in each case they stated that I must pay to obtain a Buyer?s Permit from the Ministry of Mines? The problem is that I cannot find the Ministry of Mines in Cameroon? There must be one real one, but I cannot find him?
Your response would be much appreciated.
Thank you
ALBERTO07-Feb-2014 19:47alguien sabe de la empresa madasi oil y diversifed multi business Nig LTD
Guest06-Feb-2014 13:58@jhone methew: Bhagyalaxmi Impex Ltd. is the company in the business of discovering and developing gold deposits and is a well-financed precious metals company engaged in the development of mineral properties in West Africa. It is a public company registered in Ghana. Its registered office is Accra Ghana was established in early 2012 to explore and develop mineral deposits in Ghana. The Board of Bhagyalaxmi Impex Ltd Limited Company is composed of highly experienced professionals spanning Business exploration, Product development, Project finance and financial control of public companies. It is supported by well trained and highly motivated Ghanaian staff that operates from Gold Mine exploration offices in Accra. The Company is focused on enhancing the value of the Ghana Gold Project by both production growth and an aggressive exploration program on the highly prospective tenements and identifying new growth opportunities, through judicious and profitable acquisition programs. Bhagyalaxmi Impex Ltd Limited has been eyeing on getting listed on The London Stock Exchange and on the New York Stock Exchange along with Ghana Stock Exchange.
The assets of the Company are the new revealed mining Gold deposit sites.
Alex06-Feb-2014 13:54Erik Osaro with this number 233540572446 is a scammer, do not send him any money for gold because you will not recieve even a gram from him. He has no gold.
Thanks
Susana Rubio05-Feb-2014 00:54I am trying to get information about Erik Osaro I need to know if he is a scammer or real. thank you
Guest05-Feb-2014 00:50Does anybody knows if Mr Erik Osaro is a scam or real his phone number is 233540572446, he is asking for me to send 510 US dollar to ship 1 Kilogram of gold. Thanks Susana
jhone methew04-Feb-2014 15:41A indian company Name BLImpex Ltd Ghana ,They says they can export gold, we want to this company have the capacity ?.
Guest01-Feb-2014 16:36And whoever has like even 5 kg of gold, that person is wealthy, just 5 kg is asset worth like US $200,000 and if you think that whoever has 5 kg, probably has double in assets, that person would have US $400,000, very nice house, the front side of his company building with nice advertising, and on pictures you would see some professional gold weight scales and larger molds and crucibles. Gold dust? No. Nuggets? No. Small cheap Chinese scales for rings and jewelry to measure large dore bars? No. They would be able to show the production on the gold mine. They would be able to clearly explain how they get the gold. You must have some serious production going on when you have quantities of gold ?available? in stock.
Gold is not a tomato that is sold on the market.
This is real gold in my hand:
it is 250 grams.
This is fake gold in the hand of an Indian client who has got scammed in Tanzania believing that this is 250 grams of gold:
COMPARE THE SIZES. I don?t need the calculation, I just need to see the gold to determine if it is brass or not. However, here is the calculation for many of you to understand why a simple observation of gold on the picture may be enough to understand that something is wrong.
Use this picture to observe the gold and dimensions:
For consulting, guidance and contract on how to setup your gold and diamonds purchasing business, contact us over
http://www.goldivanti.com ? some real sourcing is possible, provided you are ready to go at ground to understand the business. In general, do not expect any quantities ?ready and available in stock?, you must come closer to the production, otherwise you cannot get better prices. In Tanzania gold may be sold for above the spot gold price, so don?t be lured into thinking someone there is going to give you free money just that you can make some profits. In Ghana gold may be sold for 2?3% spot prices, for cash, in Accra. Put yourself in a position of someone in Africa who really need to sell the gold, he is going to sell it locally. Unless you become ?local company? ? you are not going to make commissions.
Feel free to contact me for true verification of sellers. I am also ready to travel anywhere in the world to verify any gold deals on distance, with most accurate methods.
Start Your Own Gold Mine
Coppel, TX
United States
call: +1 214?269?0623
UK number: +441412892273
Guest01-Feb-2014 16:36Good thread with valuable information for newbie buyers and lured intermediaries in gold business. Just like a grandmother that knows how to recognize the best tomato on the marketplace, a buyer shall be able to recognize fake gold just by indications or observing the size, volume and weight.
My advice:
1. Are you putting your priorities when checking out the deal on due diligence, papers, documents, assays? In my opinion this is wrong, you are wasting your time, that is Africa, whatever document you may get it may be also real, including also passports and all. I have found some people being real people, without license, with fake documents, but selling and doing real stuff. Documents are burden for everyone, you should ask for that at the point of purchase, when you are ready to arrange exporting papers.
2. Put your attention on the product. Know your stuff. If you don?t know the specific weight of water or don?t know metrics system, and that one liter of water should be equal to one kilogram, and how one milliliter is equal to one cubic centimeter and how to measure water displacement or how to use those gold scales which determine the gold purity even though not exact, or the specific weight of the gold, or if you never kept the real gold in your hand ? you are moving on the dangerous path. Learn from your grandmother, she knows how to choose best fruits on the marketplace, so should you. Make your homework, go to some nearest dealer, observe, learn the basics of physics that relates to gold.
3. Don?t forget that expensive and illegal drugs are easily sold in United States, Europe and just about everywhere. You get high money as easy as that. In those ?regulated? countries. Why do you think that in African mining countries someone who really have the gold would have any problems selling it without papers? Put all the stories aside, put all the explanations aside, the justifications and all that, and put your attention on the product. If product is there, the guy wants money, you want gold. Why would you put any attention to something else but to arrange the fake gold deal! He needs money as soon as possible. Gold may be sold in each African country without documents, even though they might be required by the law. But reality is totally different. I am not asking you to purchase without documents, but to put yourself in a position of someone in Africa who is owner of gold and who needs money right there. He would bring the gold to the local dealer and get his money. No questions asked.
4. In general, there are no gold nuggets that look all the same just as small buttons that are made out of the welding sticks, and gold dust is not any kind of final product. Simple fact that you are offered ?dust? or ?nuggets? is indication that something is smelly. Further, gold is not cheap. It may be sold locally both in West Africa and East Africa for spot prices or very small discounts.
5. To establish proper purchasing operation I am advising local company setup. Yes, you can make money on gold trade with Africa, but in general, you don?t need to export gold yourself in order to sell it, you can be a local broker and dealer and come directly to mines and re-sell the gold from there.
Charly30-Jan-2014 15:53FROM GHANA (ACCRA): PRECIOUS STONE RESOURCES LTD.
MANAGER: JONAS ADU DANSO
SCAMMER ASSOCIATED WITH GOLD SHOP GHANA LIMITED
Frank30-Jan-2014 09:08
WARNING:
Please DO NOT enter into any dealing with below mentioned companies and persons, as they are VERY CLEVER and BIG TIME SCAMMERS!
Company: Societe Sankaran Sarl. (Persons. Aboubacar Oumar, Rabbi Fafona, Philip Robert.).
Company: West Coast Mineral Consulting Sarl (wecmcsarl.com).
Atorney/Lawyer: Moussa Traore from lawfirm. Bile-Aka, Brizoua-Bi & Assoccies.
I have ALL needed doc?s, fco?s, undertakens, mou?s from the persons, companies and the lawyer to prove it all!
They have made a ?set-up?, which is very clever done. BUT they ARE ALL scammers.
If anyone have had contact with any of the mentioned companies or people, don?t hesitate to contact me.
I will update further as investigation progresses.
NB. All above mentioned are from Guinea.
Co franknmadsen@gmail.com
anonomous29-Jan-2014 17:18Has anyone been ripped off by Michael Watson and Brad St. John .. St Watsons Mining Company,. Mali
FMSC29-Jan-2014 10:22For information: all the gold offers from Ghana does not run via the PMMC, are scammers. Low cost gold there is not there. Only at PMMC with a price of -2% LMBA. All other are dreams, believe me.
eguavon29-Jan-2014 06:57Please does any one knowns about Gallant mining? They said they are african employment essy access agency to Australia and Indonesia.
Charly28-Jan-2014 12:21GOLD SHOP GHANA LIMITED and his manager Godfried Tawiah
Scammers, they will ask money in advance for a high discount gold.
K Dreistadt27-Jan-2014 22:13Can Anyone tell me if Gold Coast Company or Global Security are valid companies in Accra, Ghana.
Viktor27-Jan-2014 11:15Is anybody knows Mr. Haidara Chemchoudine or Gold Afric? Company? I would be thaknsfull if I get some information within 2 days.
MARCO27-Jan-2014 11:07Alex Owusu Mensah
CEO-CROWN PREMIER INVESTMENT LIMITED GHANA
SCAMMER ????
Kenneth27-Jan-2014 09:51Mr. Ameh Jacob is using the company name ?Clenam Company Ltd?
He also has a partner called ?Dr Awuni Francis?
Their updated contacts are,
amehjacob01@gmail.com
ADDRESS : P.O. BOX C247 CANTONMENT ACCRA GHANA
TEL: Tel:+233- 278585517/+233?209611029
i have copies of their fake document (FCO)
Tom Musonge27-Jan-2014 08:51I was recently in talks with Ameh Jacob, but when my buyer was in Ghana, he made an excuse not to meet him, and he kept using the word Royal Family and that got me suspicious.
Thank you for exposing them!
FMSC24-Jan-2014 15:57Hi Franke, please let the finger dupin of which he is not a Frenchman he is a simple fraudsters is black where nothing is wrong also be passport. comes later with $ 5500 that you have to pay. Be careful!
Guest24-Jan-2014 13:10Be careful everyone
Marco24-Jan-2014 13:00HANGHA MINING COMPANY Ibrahim thuallan
Skype {ibrahimthullan2000}
Moble 00232 77 40 11 87
ibrahimthullan2000@gmail.com SCAMMER????
Franke20-Jan-2014 11:31I?m in contact with the GMT MINERS COMPANY LTD Mr Etienne Chavot Dupin a frenchman he ve send me copy of his passport, about gold transaction and ve send me the FCO,he say me that I need to buy a buying permit of cost of 3000USD for 5 years to can make exportation of the gold and need to pay on the Ministry account ,he ve give me the account number compleet,can you verify is this company is right or if it?s one scammer more trying to take money
bev11-Jan-2014 23:26has anyone had any dealings with a mr anthony lefel or mr pat beadle, with gold investments or gold filtration plant
PT10-Jan-2014 21:26Dear Roger Taylor
We attempted to contact you but your provided email:rojertaylor@aol.com does not work. Kindly contact me precioustradesca@gmail.com.
Guest10-Jan-2014 21:15Please note that maccus forna and his accomplice Harriet Munezero from sierra leone and rwanda respectively are scammers.Please do notdo any business with them.
PT10-Jan-2014 20:17As the accounts executive of a registered and connected marketing firm for a precious metals and seeking genuine, proven performers, and reliable END sellers or DIRECT MANDATES of a gold and gemstones. Please note we perform exceptional DD on all our contacts. We are professionals seeking ONLY competent professionals for intercontinental trade deals. Please contact me at precioustradesca@gmail.com. Include ?Pbase.com? in your Subject line as we receive high volume of e-mails.
Note we have spidy senses for scammers and are not afraid to expose them for the benefit of this community.
Kind regards,
Guests10-Jan-2014 19:53Hello friends, Ive come to this site as a result of google search of this company:
HADI10-Jan-2014 19:13some one knows this company scamers or not:
CROWN PREMIER INVESTMENT LIMITED
P.O.BOX KN6026 KANESHIE,
ACCRA-GHANA, WEST-AFRICA
Tel: +233?246?790887/ +233?246?624812
Fax: +233?302?258811
E-mail: crowninvestcom@gmail.com
Skype: crowninvestcom
marko09-Jan-2014 10:53Kwadwo Obeng-Darko (ghana) scammer ??
Jason08-Jan-2014 08:32Add this email address to your list Edie Bless , supposedly representing Assay Mining Ghana limited. Sent me phony contracts, did not even have the common sesne to change the date on the contracts. One was dated August 6th 2013?lol Seriously!
Nneo04-Jan-2014 17:35In your (jonnie)entry of 26-Jul-2013 12:15:
?100 % fraud company: resurstsentrgaz.ltd@bk.ru
Could you provide your basis for this? And evidence or FACTS & information we can verify to support or prove this? That will be very helpful in order for us to do further research on this entity and to make the case.
M.A.M. THOWFEEK04-Jan-2014 04:12Please help me to get genuine gold seller name and address and e.mail address.
With out your help I can not genuine gold sellers.
Please I need your help.
R Barry02-Jan-2014 11:30nina brown is still up & running. I am still having an ongoing discussion with her. She approached me on the Cupid dating site. She has a slick approach and within 2 days is deeply in love with her contact. She is worth conning for a while if you want to receive explicit photos of her, But eventually when she thinks you are hooked the pictures of the gold bars held in trust for her late father are sent. All she has to do then is get them out of Ghana and then bring them to you so you can both live happily ever after. I am waiting now to see how much money she will try to extort. Pictures were good though. Email address she is currently is ninabrown339@hotmail.com
Nathan C01-Jan-2014 13:22If you have a seller from Guinea in West Africa, I may be able to assist you, as I am an Australian, who has setup our own company with Gold export license (known as Comptoir in French)in Conakry, Guinea. We also have our own melting and assay facilities in house, and we are able to use Brinks to ship gold (with Insurance). Buyers should never give sellers any cash upfront. As the Comptoir holders we are able to pay the export taxes and Central Bank charges.
If you have a seller in Guinea, let me know and I can tell you if they are genuine (because we have dealt with many crooks in Guinea) and I can let you know the procedures the seller must adhere to.
Nathan C ? nathan@metroctl.com
Tim21-Dec-2013 09:09Does any body know this email ninabrown339@hotmail.com
Her name Nina Brown from north Africa I want to
If this a scam seems real
Jackie18-Dec-2013 22:49Last month,I sent a strong email to Own Gold LLC in Texas about their unacceptable customer service via their website telephone number. The next day I received a phone call and an email apologising for causing me stress. I had been reassured that delivery of gold to customers would start in 10 weeks. Telephone 001 (USA code) 850 417 4155
Email: customerservice@owngold.us
juan fermin valladares Palma18-Dec-2013 00:21Hi My name is Juan Fermin Valladares, any one knows about jp gold limited ( Jung Park Gold Limited in Birmingham Engalnd). They send me a final contract to sign with my end buyer after a few weeks of negotiations. I want to be sure nothing bad pups up about them. I really aprecciate your help. Its urgent. Thanks for your help
Todd17-Dec-2013 15:18Dear Guest, do not do any business with Mr Etienne Chavot Dupin,
he and his group are scammers and you have to avoid them.
Todd
tseigmeister@aol.com
Guest17-Dec-2013 11:54CEO
Mr Etienne Chavot Dupin
Rue 14 Mamfe SW Region Cameroon
Tel: +237 72 26 57 88
Email:mr.etienne1949@gmail.com
skype:mr.etienne123?..Does Anybody have done business with this guy.
Guest17-Dec-2013 11:53CEO
Mr Etienne Chavot Dupin
Rue 14 Mamfe SW Region Cameroon
Tel: +237 72 26 57 88
Email:mr.etienne1949@gmail.com
skype:mr.etienne123??Does any one have done business with this guy?
Belinda Botha17-Dec-2013 10:43Can you help me, is the following actual
Gold Bar Investors chez NYARSU MINING COMPANY LIMITED
Prince Tease Williams
Virgilio16-Dec-2013 14:44dear all anybody knows about BAKARI FAMILY GOLD IN BUKINA FASO , they send to me an ?offer FCO but there is something not clear and actualy I don?t trust this offer are there somebody who already know them Thanks for your help.
note // I am looking for realable supplyer of gold Bulion seans I have a real good Buyer interested if there is a real good supplyer you all can indicate to me I will be gratfull Thanks
Steve15-Dec-2013 16:53We are buying gold from Ghana based on FOB through Asap Vasa, its hard to get any deal based on CIF. If you need gold you have to move to get it.
Martin Steve
martinstv007@hotmail.com
Guest13-Dec-2013 17:54Question: I have been weeding Ghana Sellers our for years. Does anyone here Close proper FOB Deals there?
DAVID LAWRENCE11-Dec-2013 15:41DO YOU KNOW OF A COMPANY CALLED FRANKOMINES CO, LTD. AT 25 TEMA HIGHWAY ACCRA, GHANA 00233?
ANY INFORMATION WILL BE APPRECIATED.
suzanne11-Dec-2013 06:32Does anyone know of a scammer called Marshall Schroeder Chamber he has taken 600,000 australian dollars off of a dear friend of mine 4 years ago for a gold scam saying it woudl be mature in 4 years and recieve 5million AU back but then he was told he had to send another 40,000 au for malaysian taxes to release the money, so he did!!!!!
now he is trying to find another 60,000 to send and i am stopping him and saying its a scam, please if anyone has any info on this con artist, and also a Barrister so called Lee STeven Chong
Joe21-Nov-2013 14:00Joe 03-Sep-2013 16:33
If you are looking to get in contact with reliable gold seller and miners
from Ghana and Africa, contact me on skype: jh.asamoah
Skype name is: jh.asamoah
Roberto G.17-Nov-2013 22:44mi nombre es Roberto G.
soy mandatario de compra de oro. tambien mandatario de venta sobre algunas obras de arte de primer orden.
No hay vendedores reales de oro??
llevamos m?s de un a?o buscando y todo son estafas. mis clientes compran una vez recibido y refinado en Espa?a. quien trabaje con estas condiciones estoy dispuesto a escuchar oferta seria y firme.
procedimiento con obras de arte:
LOI de compra en firme firmada por el comprador final condicionada a la presentacion de fondos cuando sea verificada la obra y su documentaci?n.
estoy en tratos con Pierre Djevesso.. alguno tiene datos de este contacto??
supuestamente quiere comprar unas obras de arte que tengo en venta.
saludos
robertog_005@hotmail.com
kenny16-Nov-2013 18:24Can any body tell me if the Anglo Gold Ashantisecurity company exsists in Kumasi and is a gentle
man by the name of dennis miller is the manager of that company?
Guest16-Nov-2013 07:41who knows Franco mines Ghana Limited from Ghana
guest15-Nov-2013 10:49Can you tell me please if KEN-AKINMINERAL ENTERPRISE is for real? Pls help me, coz i am being press by a friend to send money to them. Pls. give me an answer immediately, it will be very much appreciated and you can save me. Thanks a lot, hoping for your earliest reply.
Martin14-Nov-2013 16:06Own Gold LLC is a not a reliable company, they are fraudulent, advertising online about selling gold but its all a scheme, they have nothing and they will never return your call once you pay them.
Martin Steve
martinstv007@hotmail.com
Guest12-Nov-2013 18:54I?ve purchased gold from Own Gold LLC and yet to receive it. I?ve phoned them several time in Houston to enquire about my delivery and am put through to a voice mail. They haven?t returned my call so I?m seriously wondering if they?re genuine.
Ghufran Hashmi11-Nov-2013 17:55Dear i read that all page that is ok and any one tell me where we find the real seller with real business please i am waiting bqz i am serious buyer from dubai i need 576 kg.
Guest06-Nov-2013 05:12Any body dealt with GEMCO International ? Lome ? Togo
Lare Kamal is in contact with my people and he sent invitation letters to togo, gold photos and authorized govt documentation he claimed is original
Eri Barron05-Nov-2013 21:59I wasn?t aware that there are nothing but scammers in Ghana. I?ve been scammed by a man that goes by the name of Frank Asiedu out of Accra-Ghana. His documents look real. If anyone want to see the documents he uses, just email me at barron_eri@hotmail.com and I will gladly provide them. His information is as follows:
Frank Asiedu
Medimafo Mining Co. LTD
12 Senchi St.
South Tantra Hill-Accra, Ghana
Mob: 011?233?266?363?681
Tel: 011?233?287?203?815
E-mail: medimafominingc@yahoo.co.uk
He?s a fraudster. Promised 1 kilogram of gold dust with 20% payment due now and the rest after delivery. It?s been 5 days since he received his 20% and still hasn?t performed. He doesn?t answer emails, calls, nor text.
guest05-Nov-2013 01:36anyone heard of Jason Mills?
VBV Metals Philippines02-Nov-2013 18:45yes he is my country men precious metal brokers. from philippines live in brisbane asutralia.
guest02-Nov-2013 04:07Has anyone heard of Wilhelma Ford, gold and diamond buyer from Brisbane Australia?
harry dillon31-Oct-2013 17:21Does anyone know or heard of Own Gold LLC out of Houston Texas
Guest31-Oct-2013 12:03How can we distinguish the real from the fake in the first place? can anybody assist on that? fraudsters are everywhere. how can people make honest money?
Manny30-Oct-2013 23:47Please complile list also of genuine gold sellers and buyers.
JUDYB30-Oct-2013 21:01Does anyone know if the ?Emmali Company Ghana Limited? are scam artists? Please advise. It is most appreciated. I believe my mother to be involved in a scam
Guest29-Oct-2013 07:48KENYAN SHIPPING & CUSTOMS FRAUDSTERS: Keep away from Mausa (Moses) Changaa (+254 733 272 837/+254 733 904 594) claims to be GAA Africa shippers in Nairobi, he works with his sidekick Peter Likongu (Allegedly Customs), his driver Humphrey. He will claim to solve all or any paperwork and shipping issue at a price, he is false and totally untrustworthy.
Guest26-Oct-2013 19:23PLEASE THE SCAMMERS ALONE
THOSE PEOPLE THAT GET FRAUD ARE GREEDY
Badeem20-Oct-2013 06:52Hello all,
Is there such thing as payment to Ministry of Mines in Cameroon for buyer to export gold out of the Cameroon for 5 years?
What is the cost?
Any other cost incurred other than this payment to Ministry of Mines?
Please advise.
Thank you.
Steve Adamov19-Oct-2013 00:12The King Scammers in West Africa and no one can touch them
Country: C?te d?Ivoire or Ivory Coast
Village: Korhogo & Abidjan
Family Name: The Boga Family
Family Members: Kiki Luma, Jean Yapi, George Bamba, Yvonne Roche, Nicolas Bamba, Henry Adama,(TAX office) Koffe Arnaud, Linda Hans Jochin, Linda Ingeborg, Ouedraogo Yelbi Paul,(BANK EMPLOYEE WORKING WITH THEM)
E-Mails known: George Bamba George Bamba Family Boga Jean Yapi Mrs Yvonne Roche Bank Atlantic Abidjqn-Cote d`ivoire (BACI)
Bank Address: Immeuble Atlantique Avenue Nogues-04 Bp 1036 Abidjan 04.
Code Banque (10034)
Code Guichet (01042)
Beneficiary:Ouedraogo Yelbi Paul
Swift Code :ATCICIAB
IBAN No:ci93 ci03 4010 4201 3509 1100 0085
A/c No:13509110000
Cle rib (34)
DO NOT SEND MONEY TO THIS BANK THEY ARE WORKING TOGETHER WITH THE THIEVES.
Phone numbers:
+44031925520
+225 44 53 55 23
+225 44 52 00 81
+225 07 95 33 00
1- 727 242 2962
1- 513 442 2290
1- 513 442 2291
+225 06 60 16 44
Address: George Bamba
Rue 1965 Bingerville
Abidjan Ivory Coast
West Africa
+225 04 535 523
Joana Jhonson
Villa 121
Rue Virdi
Abidjan, Cote d?Ivorire
Guest18-Oct-2013 17:59Gertrud Appiah
GertrudAPP@aol.com
Police in Ghana have emailed the elderly person she was claiming to be on her way to in the USA with 13 kilos of gold. Apparently the police have asked for 15,000$ to bail her out.
Chrank17-Oct-2013 09:35Benjamin Nana Owase:
Small man, big crook. Phone +233 240 302 2021. I spent time in Ghana, and met the man through some other man. He invited me to come and stay at his house. Then I discovered that he has bad temper, and inferiority complex. Plays big man, but sucked my cash all the time. When I returned home, we sent him cash to bring 10 kg gold that we paid the owners for in part. After a week he refused to deal with us, and sold the gold for himself !!!! BE CAREFUL. BIG CROOK.
Blue2015-Oct-2013 09:54ZAMBIAN FRAUDSTERS: Shedrick (Passport ? Sedrick) Kasanda Kapasa (+260 966 19 8485) and Godfrey Seleu (+260 964 32 5007). They claim to be shareholders of Mine de Kambove, BP 680, Kolwezi, Katanga, DRC. They will provide all the necessary (false) papers with stamps (origin, ownership, assay) show you photos with current newspaper, and even bring the gold in a safe in the boot of the car, and show you ?short-time? the product before the ?customs or/and the bonded warehouse security? take the goods. BE WARNED these two guys are time wasters and fraudsters.
Blue2015-Oct-2013 09:53ZAMBIAN FRAUDSTERS: Shedrick (Passport ? Sedrick) Kasanda Kapasa (+260 966 19 8485) and Godfrey Seleu (+260 964 32 5007). They claim to be shareholders of Mine de Kambove, BP 680, Kolwezi, Katanga, DRC. They will provide all the necessary (false) papers with stamps (origin, ownership, assay) show you photos with current newspaper, and even bring the gold in a safe in the boot of the car, and show you ?short-time? the product before the ?customs or/and the bonded warehouse security? take the goods. BE WARNED these two guys are time wasters and fraudsters.
Guest14-Oct-2013 20:02Is Dennis Mensah from Golden Age Mining in Accra, Ghana, legit?
Jason13-Oct-2013 20:56Big Fish and Scam Artist in Uganda and Congo Name: Joseph Baguma Email:joebaguma@gmail.com
Also he works with another Scam artist called: Karim Nsubuga, Email: goldtrustugand@aim.com
Beware please don?t fall on their trap as I did current in Uganda.
JWNBG11-Oct-2013 08:24Now sommebody Mr. Barrister Robert Mensah Williams,Ghana, Phon: 0023326507768
dona10-Oct-2013 19:04Dear Sir,
I am doing a DD for my Boss on two persons and their companies.
we have been asked by this Russian company siyaoils Mr.dimitry semeonov to pay $35000 for Mandateship letter which we didn?t pay, we do understand this is a scam, anyone been scammed by this company?
we also like to know if this person is real and if he is really a Mandate for oil company in Russia, his name is Evans Bulkin, company, resurstsentrgaz, ltd resursTsentrGaz.ltd@bk.ru
+79685339751 (work)
if before my boss deals with him we are doing a due diligence on him and his company.
mohd09-Oct-2013 15:33WE ARE FROM INDIA.
PLEASE LET US KNOW IF ??asosamineslimited? IS REAL OR SCAMMERS
freeman06-Oct-2013 20:35its a very good news to when i see such forum here, where people are doing their best to help create the awareness of Gold scam and other scam issues worldwide.
please i am here to offer my help to anybody who will need my advice on any transaction relating to Gold Especially with Countries especially Ghana cos that?s where i resides.
i have some track records in helping many people from sending more money to this scammers in ghana and some other parts of Africa like Nigeria, Benin and some others African countries. i hope my contributions may be worth to someone too? stay bless?
Ashok Aditya04-Oct-2013 08:28This really helps many to locate fake sellers. It shall be nice to give the real sellers list also is my humble request.
Larry Lesniak03-Oct-2013 04:17Do you have any information on Eagles Gold Security Company in Accra?
Kwok-LEE03-Oct-2013 00:11will greatly appreciate if you could help to check if the following companies are fake or honest or not, the seller?s name is ocean link ocean group and want us to pay directly to the forwarding company in ghana named ce.medulla shipping agency ltd who asked for usd 45000 to be paid upfront before they will send the gold bar to GHANA KOTOBA International Airport for airfreight. thank you! KWOK
kwok LEE03-Oct-2013 00:09will greatly appreciate if you could help to check if the following companies are fake or honest or not, the seller?s name is ocean link ocean group and want us to pay directly to the forwarding company in ghana named ce.medulla shipping agency ltd who asked for usd 45000 to be paid upfront before they will send the gold bar to GHANA KOTOBA International Airport for airfreight. thank you! LEE
Jabm30-Sep-2013 17:56Barstone mining Tanzania ?. Offer CIF and turn round and ask for an upfront notary fee. Beware Mago maturity, mabuli.
jonnie26-Sep-2013 11:13100% fake , dont believe on their in their internet offers. they provide all fake documents.
guaranteedcontractors2012@gmail.com
Chuck24-Sep-2013 14:27CEO
Mr Etienne Chavot Dupin
Rue 14 Mamfe SW Region Cameroon
Tel: +237 72 26 57 88
Email:mr.etienne1949@gmail.com
skype:mr.etienne123
I found a conflict doing DD and reached out to another party with the same name. He stated his ID had been swipped by some character offering goods out of Cameroon.
Mike Ran22-Sep-2013 10:48From: messages-noreply@bounce.linkedin.com [mailto:messages-noreply@bounce.linkedin.com] On Behalf Of Mr. Abdurahma mohammed via LinkedIn
Sent: Sunday, 22 September 2013 5:42 PM
To:
Subject: GOLD SELLER FROM GHANA
Mr. Abdurahma mohammed
CEO Gold Seller at AB AND SON COMPANY IN GHANA
ATTENTION:
DEAR SIR/ MADAM,
MY NAME IS Mr. ABDURAHMA MAMOHAMMED. WE ARE GOLD SELLER FROM GHANA. WE HAVE MINING OF OUR OWN, WHICH IS OUR FAMILY BUSINESS SINCE 1982. RIGHT NOW WE HAVE 200KGS OF GOLD FOR SALE, OUR TERMS IS THAT THE BUYER WILL COME DOWN GHANA AND WE TAKE HIM TO OUR MINING SITE FOR HIM TO SEE ALL THINGS BY HIM/HERSELF BEFORE GOING INTO AN BUSINESS WITH HIM/HER.
BECAUSE THEY ARE MANY PEOPLE WHO SAY THEY HAVE GOLD BUT THEY ARE ALL FAKE THAT IS THE REASON WE HAVE TO TAKE OUR BUYER TO THE MINING SITE FIRST BEFORE ANY OTHER THINGS.ALSO WE DEAL THROUGH PMMC GHANA AND WE ALSO SHIP THROUGH PMMC.
SECONDLY WE HAVE AN AGENT WHO CAN GO TO ANYWHERE IN THE WORLD WITH 100KGS FOR ANY BUYER WHO DON?T WANT TO COME DOWN HERE IN GHANA. THEN HE/SHE CAN PICKUP THE GOODS WITH OUT ANY PROBLEM. ALL THE EXPORT DOCUMENTS WILL BE WITH THE AGENT DURING DELIVERY.
THEREFORE IF YOU ARE INTERESTED, YOU CAN CONTACT ME WITH THIS EMAIL ADDRESS, AND TEL, NUMBER: abdurahmamohammed@outlook.com Tel: +233262101889 SO TO DISCUSS ON MORE DETAILS.
COMMODITY:Gold Bars
P QUANTITY: 200KG (THIS DONE, REVOLVING CONTRACT FOLLOW)
URITY: 96.99% or better
QUALITY: 22+ CARAT PLUS
PRICE: USD16,500.00/KG
Thanks.
Mr. ABDURAHMA MAMOHAMMED.
GOLD SELLER FROM GHANA
Reply to Mr. Abdurahma
Bob19-Sep-2013 02:59Clara Jones, mother was in accident, has little money, uncle just died and left goldmine to her, crooked govt. officials are threatening to shut it down they own 40%, uncle owned 60%.
Clara falls madly in love with you. we need $ for tools right away or govt. takes over.
then lawyer Senseh emmanuel gets involved as reciever of requested small $. Then of course the lea=gal fees and neccesary bribes cost more that poor miss jones can scare up and she cajoles her would be lover with nude pictures to help out. Don?t do it and I did not. i threatened Interpole was about to show up to arrest them and they totally dissapeared. What a surprise>
GOLD AND DIAMOND SCAMS14-Sep-2013 21:08Hello Patrick, kindly let your friend know that this is a scam, he better stop now or blame himself for any loose.
Thanks.
Noel.
patrick13-Sep-2013 15:29A friend of mine has been chatting to a women from Accra,apparently her late father left 16 alluvial gold bars in trust for her,apparently the bars are being held by Diamond Security Group Ghana, and they require a fee of ?585.00 to release the gold bars,According to the Lawyer dealing with it Mr Hackman,that fee is for storage only and its in the deposit agreement form,i told him its a con,am i right.
Aissata12-Sep-2013 17:59Please, is ?GEIGH HOLDING INTERNATIONAL SA? a genuine gold seller?
Many thanks in advance
Marcel09-Sep-2013 18:52Beware of gold buyer scammer in Malaysia, he will convince you to ship him gold with his
wife address. He claims to be related to the Ambassador of Bahrain and has two names: He \
goes by these names: Cheng Do and another name: Hamzah Mohd Yusof.
Email: docheng4@gmail.com
Wife email: clementyway@yahoo.com.sg
His number is: +60163164358
Below is the address he will give for shipment. His wife uses a different name and he also
uses a different name, he is a big time scammer.
MRS / ROSLINA BTE KASMANI
Sports Unit Officer
University Technology Malaysia
Semarak Road 54100 kuala Lumpur
MALAYSIA
Marian05-Sep-2013 17:57CROM : please give your email address
m.chodacki@xtmtrade.pl
Crom04-Sep-2013 21:27There are seriously some naive people out there. I live in West Africa and trade gold. I perform the air carriage to Europe myself along with a representative from the seller. I pay 15% upfront and 85% paid only upon confirmed arrival and agreed quality, in Europe. I buy lots of 25?50 kgs per carriage.
I buy primarily from Benin, Togo and Ghana. Most of this gold originates from Mali. Buying the gold i reckon is financing rebels,
At the end of the day, on a good day i make a gross profit of 6?8%. That is before hotel, flights, insurance, risk of price fluctuation etc. So those guys out there transferring money to people in hope of generating huge fortunes in no time are, if not stupid, then naive. This is hard work and deals are not done over the internet. It requires personal relations, and lots of them. Permits are required, customs, police, quality controllers, seller and so forth.
Dont underestimate the effort required, dont sit in front of your laptop believing you hit jackpot.
Marian04-Sep-2013 20:43
Please let me know if this scammers?????
Prestige Commodities LLC
Mr. Jose Javier Oliana
Limburg, Netherlands ? 8243 GM
Phone : +31?45?5767891
Email Address : prestigecommodities@yahoo.com
Joe03-Sep-2013 16:33If you are looking to get in contact with reliable gold seller and miners
from Ghana and Africa, contact me on skype: jh.asamoah
Skype name is: jh.asamoah
Joe03-Sep-2013 16:32If you are looking to get in contact with reliable gold seller and miners
from Ghana and Africa, contact me on skype: jh.asamoah
Skype name is: jh.asamoah
Gale02-Sep-2013 18:11Looking for information on MIDO Trading INC> Tawfiq Rahaymeh/CEO.
anyone dealt with him or them?
Roger31-Aug-2013 18:25Hello Joe,
Fast delivery Transport in Benin are scammers, I was a victim and nothing good
comes from them. For more details write me: rojertaylor@aol.com
Joe Davis30-Aug-2013 09:26Do you know gold shipping comany,Fast Delivery Transport in Benin and its representative Manager,Michel Orion Daniel in Cotonou,Benin ???
Does such company exist and does he exist for the business. They request continuously requesting money so much fees as documents,renewwal,dellayed charge or penalty?..They changed shipping schedule everyday after and can?t ship gold.
Joe Davis30-Aug-2013 09:22Do you know gold shipping comany,Fast Delivery Transport in Benin and its representative Manager,Michel Orion Daniel in Cotonou,Benin ???
Does such company exist and does he exist for the business. They request continuously requesting money so much fees as documents,renewwal,dellayed charge or penalty?..They changed shipping schedule everyday after and can?t ship gold.
Wilfred29-Aug-2013 07:51Beware of this scammer, he has no gold.
Sanso Gold Corp
Medina Coura, Rue 150 Porte 25
Bamako,Republic Of Mali
Telephone:-00223?6964?9796
Fax:- 00223?4657?40023
Web:-
www.sansogoldcorp.comSkype ID: sansogold1
Email:- sansogoldcorp@gmail.com
sansogold@sansogoldcorp.com
GOLD AND DIAMOND SCAMS27-Aug-2013 08:48AA Minerals is a reliable and licensed refinery here in Accra Ghana, but the legitimacy
of this offer depends on who sent it. If its from a gold seller/miner you have to check
on him properly, but as for AA minerals they are reliable. Thank you.
Jerry27-Aug-2013 05:02AA Minerals in Ghana is licensed refinery which is readily available
to carry out assay tests on gold dust to ascertain and certify its
purity and carat of each consignment at a handling fee of .02% on the
face value of the tested, refined and certified gold dust smelted into
metal bar, plus $25.00 on each kilogram certified. This company will
arrange shipment to your designated address at the freight charge of
US$400.00 a kilogram. Does this sound legitimate? Thank you.
John26-Aug-2013 16:54Hello Krainey, you are probably being scammed by this Michael Staderfer, do no
send him anything.
Thanks.
JEOBISON25-Aug-2013 15:31FRUAD ALERT.
BEWARE OF ASAD RAZA HE IS A FULL TIME SCAMMER.
Email: alispo@yahoo.com
BE WARN BE WARN
JEOBISON25-Aug-2013 15:31FRUAD ALERT.
BEWARE OF ASAD RAZA HE IS A FULL TIME SCAMMER.
Email: alispo@yahoo.com
BE WARN BE WARN
Luke Williams25-Aug-2013 12:15Mr. Akim Johnson
is totaly fraud and he has man emails id and many mobile numbers, he work from liberia, ghana, and many other countries, he mostly work in Bagkok,
Luke Williams25-Aug-2013 11:59DEAR ALL REAL GOLD BUYERS,
LIBERIAN GOLD SUPPLY COMPANY BY NAME OF BLACK MINERS INCORPORATED,
MR. SALLEM MUTARI SALES DIRECTOR OF THE COMPANY AND
EMAIL: blackminersincorporated@gmail.com
AND MOBILE NUMBER: 0023278485080 IS A FRAUD MAN AND FRAUD COMPANY FROM LIBERIA.
Company Name: MELTRIC METALS SARL
Address: NO.25/7 Rue de Kaporo, Commune De Ratoma Conakry,
Country: Guinea
Represented by: Mr. Alli Kallon Mob: 00224?657437976/ Mr. JABUIRU TOURE CEO Mob: 00224?657032117
Email. meltric.metals@yahoo.com, allibusiness@yahoo.com
WE SENT TO MR. MUTARI FIRST 100$ THROUGH WESTERN UNION FOR GOLD SAMPLE COURIER CHARGES BUT HE DIDNT SEND SAMPLE YET, THEN HE INTRODUCED TWO AFRICAN BOYS AND THEY STOLE FROM ME IN BANGKOK 2800$ FOR GOLD, THEN THOSE BOYS SENT BOYS TO DUBAI WITH GOLD WE GIVE HIM 14000$ FOR GOLD BUT WHEN WE TEST GOLD , GOLD WAS FAKE.
WE LOST ALMOST 16900$ FOR THIS PERSON.
PLEASE I WOULD LIKE REQUEST YOU , KINDLY RECOVER MY MONEY,
BEST REGARDS
ASAD RAZA
PAKISTAN
MOBILE: 0092?300?8717212
kkrainey24-Aug-2013 04:35Does anyone know anything about Barrister Michael Standerfer of Asare Akoto & Associates Chambers? America House Rd., Cantonment, Accura Ghana? They deal in gold documents and have requested 40% upfront with a total owed of $15,300 and will ship to USA? Please give me any details that you know about this?
Thank you,
kkr
jonnie22-Aug-2013 12:20ahmed.baaqil@gmail.com
100 % time waster and fraud
jonnie22-Aug-2013 12:20100% time wasters and fraud :
ahmed.baaqil@gmail.com
GUEST20-Aug-2013 23:57
WORLDWIDE GOLD EXPORTER ? SKYPE NAME CCI115 HAS JUST CHANGE HIS NAME TO
MINING & EXPORTING GOLD TO THE WORLD
HE GOES BY THE NAME OF DR MOHAMMED TRAORE. HE HAS NO PhD.. HE IS JUST A THUG.
AND WILL STEAL YOUR MONEY.
IF YOUR CONTACT BY ANYBODY FROM SIKASSO GOLD MINE. CONTACT YOUR LOCAL POLICE
HE WILL ASK YOU TO PAY THE MONEY IN A EXPORT GOVERNEMENT ACCOUNT AND WILL SEND YOU KNOW GOLD..
DO NOT SEND HIM ANY MONEY HE IS A CROOK, THIEF
jonnie20-Aug-2013 13:16100% fraud and scammer :
ahmed.baaqil@gmail.com
its a internet fraud ? be alert of this fraud.
tayeb arabic19-Aug-2013 17:50Iam dealing with a person from LOME TOGO , his name is Sebastien KOroma as seller gold bars , his mobile is +22967518725 and I wonder he asked me to pay for shipment of gold .
can somebody helps me if this guy is fake and scammed . pls i need yr help. his e-mail is Sebastian Korom (sebastiankorom@gmail.com)
lori benz16-Aug-2013 15:08
On Fri, Aug 16, 2013 at 7:34 AM, Edward Owusu wrote:
Dearest,
We are local miners acting with full corporate authority and with full legal responsibility do hereby irrevocably confirm and commit subject to the law of perjury that we are ready willing and able to sale Raw AU Gold dust/Bullion.
We hereby notify your organization a full corporate offer for the sale of AU Gold Bullion and Bars.We are looking for commercial or private Gold buyer that can buy in large quantity. Any interested buyer should contact us for negotiation and arrangement for the sale. Our prices are as modest as can be found any where in the world and better because we are direct licensed/Authorized local miners.
I RECEIVED THIS TODAY.
In the degree of sincerity and trust found in you, if we receive your reply, we will feed you with the relevant information in this Gold business.
Thanks and hope to hear from you.
Edward Owusu
Guest12-Aug-2013 19:51a scammer arrested in Nairobi kenya-Xavier Onyango in the act of Conning!!now at the Police station !!!
Guest12-Aug-2013 19:31A scammer arrestein Nairobi in the act.Xavier Oliver onyango.thanks
hptrader09-Aug-2013 19:15Be careful of Rita Eggeraat from California. I was told from someone she scammed some rookie in the gold business over 8k. This kid actually lent her his credit and she just maxed it out on an apartment and she never paid. If you deal with her beware.
GUEST07-Aug-2013 21:15
WARNING IF YOU WANT TO KEEP YOUR MONEY.. DO NOT DO ANY BUSINESS WITH THIS SCAMMER, LIAR, AND THIEF. THEY STOLE 224KUSD FROM A BUYER?
THIS MAN DOES?NT NOT HAVE A PHD, HE USES A FAKE PASSPORT, AND HE AND HIS EXPORT COMPANY ARE A TEAM THEY WILL TAKE YOUR MONEY AND SEND YOU NO GOLD. HE USES SEVERAL ALIAS, DR. MOHAMMED TRAORE, C. CHRISTIAN IZWU TRYING TO SELL OIL, MR ALPHA DICKO, AND SEVERAL OTHER NAMES?..THEY ARE THE SAME PERSON. HE USES SIKASSO GOLD MINE OR SIKASSO GOLD VILLAGE MINE, AND ALL IS ALSO ON LINKENIN AND ALL THE PEOPLE WORKING FOR HIM. IS ACTUALLY HIM. HE HAS SEVERAL SKYPES NAMES AS WELL. AND IF YOU SEND HIM AN EMAIL. HE WILL ALSO BREAK INTO YOU EMAIL.
BRINKS IN BELGIUM WILL NOT MOVE ANY GOLD IF YOU SHOW HIM ANY DOCUMENTS THAT YOU HAVE BOUGHT GOLD WITH THIS MAN NAME. HE WILL JUST SEND A BOX OF JUNK AND NOT GOLD. BUT WILL TAKE YOUR MONEY.
CEO
SIKASSO VILLAGE GOLD MINE ? ? MALI
I am Dr. Mohammed Traore CEO Sikasso Gold Mine located in Mali and the Secretary General Of West Africa Gold Miners, I have Gold dore bars for sell at the price of $36000 per kg purity 93.5% with 22carat. Any interested buyer should contact me Via goldmining.company@yahoo.com Or Mohammedtraore24@yahoo.com Tel: (+223)60456793
jonnie03-Aug-2013 16:08100 % fraud from Nigeria.
Be aware of this fraud, He uses many email ids for fraudulent activities on internet.
rtjmnl@gmail.com
rtjmanifest@gmail.com
RTJ MENIFEST NIGERIA LTD.
ray01-Aug-2013 19:11Planet Diamond Company in Douala, Cameroon is a scam. Dont send them any money because you will never see it again.
Guest31-Jul-2013 08:45Midtown Traders are scamming people in New Zealand..ado not deal with them as you will be ripped off,
Marian Chodacki30-Jul-2013 21:07Mamoud HASSAN
General Director.
KALANA COMMUNITY GOLD COUNCIL.
Rue 205 Porte 067 Kalana.
SKRAMER ?????
Tel:+223 70394019. or +223 60966076.
Email =kalanagold@2itb.com
Email = kalanacommunitygoldcouncil@yahoo.com.ph
Email=kalanacommunitygoldcouncil@gmail.com
Skype = kalana.gold.hassan.
zane27-Jul-2013 14:02Don Peter Innocent Appiah , Massive Scammer , The old DP trick ! Sounds like Barry White lol
www.trxservices.com scrammmers????????
Thomas26-Jul-2013 15:38@ Richard
i am in touch with ancient mining..pls contact me and explain your comment below in regards to them being scammers?thanks
jonnie26-Jul-2013 12:15100 % fraud company :
resurstsentrgaz.ltd@bk.ru
jonnie26-Jul-2013 12:13100 % scammer company in russia :
resurstsentrgaz.ltd@bk.ru
resurstsentrgaz, LTD.
125083, Moscow, March eight street.
Contact : +79685339751
cervantes26-Jul-2013 10:40Has anyone been scammed by a Mr. Oti Konadu Daniel, claiming to be with Global Gold & Finance Company Limited ? Ghana?
Richard24-Jul-2013 14:14www.ancientmining.com these are scammers, beware of them and their offers.
END SELLER24-Jul-2013 10:00Hello,
If you are looking to buy gold in Ghana kindly contact me for details
and what we have available.
Thanks
Email: goldprospects@outlook.com
STEINER23-Jul-2013 10:48am looking for a serious gold supplier
nick22-Jul-2013 10:37Guys please be careful of this company AKUBEA MINING & FARMING CO. LTD.they are big time scammers in Ghana, they have scammed loads of buyers, they are located in Achimota in Accra.
Copy and paste the link below for more information:
Guest22-Jul-2013 09:35Do you know Roberts Brancato,New Branx Trading Ltd or Robert Branx he says he sells gold from Ghana
Guest22-Jul-2013 09:32Do you know Roberts Brancato,New Branx Trading Ltd or Robert Branx he says he sells gold from Ghana
Isak22-Jul-2013 08:06Firstly many thanks for the creator of this site, it is time that we fight these criminals. If anyone decide to invest in gold from Africa, please contact me in person, I travel to any destination and identify your seller. I can give you an up date on all their activities and if you decide to purchase gold, we handle all transactions. A firm warning, guys there are a few guys in Italy who claim to purchase gold, they will invite you to Italy and arrange for you to be mugged. DO NOT PAY UPFRONT for any gold. Good luck and well done to the creator of this site, saluut
Guest19-Jul-2013 08:54Monteblanc gold mine company are cheaters! They do not make any obligations by the contract and trying to steal the money! STAY AWAY FROM THIS COMPANY! The director is Shabani Juma do not let him steal your money! Do not work with his manager Bokasa Frank and anybody from this company! Please stay away from any offer coming from them.
acadien14-Jul-2013 09:01Two questions
Is it the case that anyone trying to seriously buy or sell gold bullion online has no reliable touchstone.? Is there really any product that is not traded through the major market makers? I have be looking though the internet on behalf of a legitimate buying group and it?s always the same . Some nimrod says they can source whatever you declare that you?re interested in and then when you press for proof of product ? they just stop ? the correspondence abruptly halts. I don?t really expect to find a huge bargain. But out of 20 or so responses to a one day posting ? no one came back to say ?I keep the gold here. So I just keep asking for Safe Keeping Receipts that I can verify with someone at the institution that?s holding the gold ? no one follows up from that point on.
Why would the production from any mine not just be turned over to a full time broker.
It doesn?t make sense o hear that ?Lefty and Cecile? from Cameroon somehow got it the distribution chain and now have millions in Dore bars to sell ?.. but I tried on behalf of some jewelry makers to see if there were less expensive sources ? gold is money ? would you sell a commodity that doesn?t ?spoil? for significantly less than if you had a Goldman Sachs broker get bids for you ? I?m not holding my breath ? I really don?t think that there is a vibrant second tier market of any consequence ? Just scammers
Love to hear from someone who can set me straight?.
And:
Can anyone tell me what a Certificate of Photosynatry is? Or simply tell me where to look.
I can?t seem to track it down. Not in mining terms dictionaries ?
Thanks
ENRIKE12-Jul-2013 23:31THIS IS ANOTHER SCAMMER HE CALLS FROM GEORGIA WITH AN ACCENT EMMANUEL ASANTE EMAIL;;thisisasante@gmail.com HE ACTS LIKE HE HAS CONNECTIONS IN GHANA HE CALLS FROM MOBILE PHONE# 4047077169??.ONES HE CALL ME HE ASK ME THAT I NEED IT TO TRUST HIM AND TO SEND HIS 5000 DOLLARS WHICH I SAY FUCK YOU YOU JUST A THIEVE NOW HE JUST KEEP CALLING WITH TREATS SAYING THAT HIS GOING TO LOCATE ME AND KILL ME AND MY WHOLE FAMILY WHAT MAKES ME MAD WAS THAT HE SAID I WILL RAPE YOU DAUGHTER IN FRONT OF YOU PIG ?I TOLD THE FOOL TRY MOTHERFAKER I DONT KNOW HOW THEY LET PEOPLE LIKE THAT COMIN TO OUR COUNTRY SICK PEOPLE BE ON THE ALERT HE IS IN THE U.S.
ESTEBAN V.12-Jul-2013 23:07THIS CROOKS OPERATE FROM TANZANIA Dar es Salaam,,ASKING MONEY TO PAY FED EX SHIPMENT OF 500 GRAMS OF GOLD ..HE ASK TO SENT MONEY THRU WESTERN UNION CAUSE IS FASTER THAN A BANK I SENT HIM 900 USD UNDER?? Ndi TERENCE?? BUT ONLINE HE USES NAME ??Hellen JOHNSON MAKAYA?? PROBABLY FAKE NAME BUT JUST BE ALERT HE USES SKYPE NAME ??Hellen.johnson?? his EMAIL ADDRESS IS ??Hellen_j86@yahoo.com?? I KNOW MY MONEY IS GONE BUT IF I CAN PREVENT FOR SOMEONE ELSE TO GET SCAM BY THIS LOW LIFE CRIMINALS I WILL SO EVERYTHING IF YOU HAVE FRIENDS THAT ARE IN THE TRADE BUSINESS BE A GOOD FRIEND AND PASS THIS NAMES AROUNT THE POWER OF THE WEB IS INCREDIBLE LETS DO SOMETHING TOGETHER TO STOP THIS CRIMES MY NAME IS ESTEBAN V. STAY ALERT.. GOD BLESS YOU
M guest12-Jul-2013 03:51Is Ken Akin Minerals a legitimate company to be trusted?
ATTENTION10-Jul-2013 13:00This is a very important message to anyone involved in the commodities industry on the new measures with respect to Buyers and Sellers conducting transactions.
From now on, if an ICPO, LOI, RWA, or BCL is issued and the document is not real, true and/or actually verifiably factual, the Buyer will be able to inform the FBI, ICC, and INTERPOL. In addition, after an FCO is sent to the Buyer, there should be a formal answer to Seller from Buyer in a timely manner in accordance with the agreement between parties.
If there is no response from the Buyer in a timely manner, the buying company will be reported to the FBI, ICC and INTERPOL. If this action is repeated by sellers, they too will also be reported for abuse of the NCND, LOI, ICPO, AND RWA OR BCL, FOR THIS IS NOW A FEDERAL OFFENSE.
It is important to transmit this to all clients that work with providers that are members of the ICC, FBI, and other international organizations. From this point forward, the international codes will be strictly enforced to exclude all intruders that send or transmit false information. Those who submit a false NCND/IMFPA, LOI, ICPO, RWA or BCL, or FCO, as well as FALSE PROOF OF PRODUCT (POP), FALSE PROOF OF FUNDS (POF) WILL BE CHARGED WITH A CRIME.
This offense went into effect on November 15, 2008 and re-effected this month after a meeting was held between the Federal Reserve, European Central Bank, Interpol, Federal Bureau of Investigation and Central Intelligence Agency.
The reason for this measurement is to protect the commodities industry which is a fundamental part of the world?s economy.
I have read and understood the severity of the warning above and do realize the serious impact that pertains to all oil and other commodities transactions.
?
jonnie10-Jul-2013 12:07100% time waster :
100% time waster :
dmitrykovalenko@hotmail.de
be aware of this contact.
jonnie08-Jul-2013 12:56http://www.kovalenko-investment.com/
jonnie08-Jul-2013 12:54100% time waster :
jonnie08-Jul-2013 12:32100% time waster :
dmitrykovalenko@hotmail.de
be aware of this contact.
eSTEBAN06-Jul-2013 10:09THIS GUY Ndi TERENCE HE IS FROM TANZANIA HE IS A THIEVE HIM AND HIS PARTNER HELLEN JOHNSON SEND PICTURES OF GOLD THEN HE ASK FOR MONEY FOR SHIPMENT DONT SEND THEM ANYTHING THEY USE SKYPE.
Jonnie04-Jul-2013 15:10100% fraud and time waster ? be alert of this company :
RTJ Manifest Nig Ltd. email : rtjmanifest@gmail.com
Reg Code: 411017. Address: No 9 Odusina Street Ladipo Papa Ajao Mushin Lagos State Nigeria. Contact numbers are: 2348137021972, 2348060597891, 2348136389838 and 2348026303670.
jonnie04-Jul-2013 15:05100% fraud and time waster ? be alert of this company :
RTJ Manifest Nig Ltd. email : rtjmanifest@gmail.com
Reg Code: 411017. Address: No 9 Odusina Street Ladipo Papa Ajao Mushin Lagos State Nigeria. Contact numbers are: 2348137021972, 2348060597891, 2348136389838 and 2348026303670.
jonnie04-Jul-2013 11:01100% fraud and time waster ? be alert of this company :
RTJ Manifest Nig Ltd. email : rtjmanifest@gmail.com
Reg Code: 411017. Address: No 9 Odusina Street Ladipo Papa Ajao Mushin Lagos State Nigeria. Contact numbers are: 2348137021972, 2348060597891, 2348136389838 and 2348026303670.
Antonio03-Jul-2013 22:02Is it necessary to purchase a license in the ministry of mines camerun to buy gold? and if so what price? thanks for your help can answer me this email: sientelaenergia@gmail.com appreciate your help.
orion03-Jul-2013 19:59
I have to add a new SCAMMER from Lusaka, Zambia.
His name is Francis & Thelma Mbewe after the buyer signed the contract for the supply of 200 kg of gold bars to Dubai, asked the buyer to pay, to a self-styled representative of the United Nations, the sum of 400,000 dollars for the trouble and for the documentation of gold on his arrival at Dubai airport ..
This even before it was verified that in the coffers there really was gold.
When the buyer has proposed to go to Africa to personally take the gold he refused.
His email is: fkm-minerals@zambia.co.zm.
Skype Name: Francis & Thelma Mbewe
Franco Fresi03-Jul-2013 19:56
I have to add a new SCAMMER from Lusaka, Zambia.
His name is Francis & Thelma Mbewe after the buyer signed the contract for the supply of 200 kg of gold bars to Dubai, asked the buyer to pay, to a self-styled representative of the United Nations, the sum of 400,000 dollars for the trouble and for the documentation of gold on his arrival at Dubai airport ..
This even before it was verified that in the coffers there really was gold.
When the buyer has proposed to go to Africa to personally take the gold he refused.
His email is: fkm-minerals@zambia.co.zm.
Skype Name: Francis & Thelma Mbewe
marco03-Jul-2013 01:31Priscilla Laryea, Hse 555/30 Nii Boi Town, Accra, Ghana..233547657452?big time scammer along with Falcon Shipping?beware she poses with family and also seductive photos to lure unsuspecting men to send money for gold shipping. Uses online dating sites to commit fraud with criminal intent
Guest01-Jul-2013 19:22They are on facebook too!
Mark Addo:
Hello these are my document covering my gold is worth 1.4 million dollars I need to renew my documents before I can get access to ship it cos soon I will be back home for us to plan our marriage please let this be a secret between us I hope as you promised me you will be able to send get the money for me to my client to renew my documents
Frank Chukes01-Jul-2013 09:01Be Warned when attempting to do business with Fame Kante of Phynodderrie Limited of Conakry, Guinea. email afrimaksarl@yahoo.fr, Telephone +2246267881. Kante?s associate is Mohamed Bangoura email mohamedbangoura7119@gmail.com, Telephone +224621628023. After an agreement for me to come to Conakry and pay the taxes for 3 kgs these fraudsters changed their story to say that I needed to pay the taxes for 10 kgs. I refused and requested a refund. Needless to say I am still waiting on my refund. They are bogus and they make up lies as they proceed. Do your wallet a favor and stay away from these arrogant rats.
Frank Chukes01-Jul-2013 09:01Be Warned when attempting to do business with Fame Kante of Phynodderrie Limited of Conakry, Guinea. email afrimaksarl@yahoo.fr, Telephone +2246267881. Kante?s associate is Mohamed Bangoura email mohamedbangoura7119@gmail.com, Telephone +224621628023. After an agreement for me to come to Conakry and pay the taxes for 3 kgs these fraudsters changed their story to say that I needed to pay the taxes for 10 kgs. I refused and requested a refund. Needless to say I am still waiting on my refund. They are bogus and they make up lies as they proceed. Do your wallet a favor and stay away from these arrogant rats.
nick29-Jun-2013 14:26BOB and Antonio, please do not think Gold stinks everywhere in Ghana, I can assure you that before gold comes out of the ground it has already been paid for, so if anybody offers you FCO for gold purchase, automatically know that the person or company is a scammer, my advise to you is to team up with small scale concessionaires and mine the gold by providing support in the form of equipments and then you can get the gold. if you intend coming over to Ghana in the first week of july i will be happy to assist you. Thanks
Ben24-Jun-2013 14:55Good day all, if you are a buyer of Bitumen or gold, kindly contact me. We can supply both products.
Email: benjaminkayle@gmail.com
Ben.
Bob22-Jun-2013 13:40How best can i buy gold from Accra Ghana, am planning to travel there by first week of July, i have many offers from sellers but don?t know the right person to work with. Please any help or guidelines will be appreciated.
Thanks,
Bob
Antonio20-Jun-2013 12:31hi i am looking for a serious seller to purchase gold bullion 150kgs of 12.5 kgs coined, the payment would be carried out by letter of credit, being liberated at the time of receipt of gold in my country.
Guest19-Jun-2013 08:25Dear Sir,
I am trying to ascertain the best method of getting a refund for tax money I put up in Guinea, Conakry. The orginal trial was for 3 kgs they said I needed to pay for 10 kgs and I refused the bait and switch tactic. I have wire records for most of the transaction. Thank you in advance for any recommendations to get my money back and let everyone know that they are crooks.
Guest19-Jun-2013 08:24Dear Sir,
I am trying to ascertain the best method of getting a refund for tax money I put up in Guinea, Conakry. The orginal trial was for 3 kgs they said I needed to pay for 10 kgs and I refused the bait and switch tactic. I have wire records for most of the transaction. Thank you in advance for any recommendations to get my money back and let everyone know that they are crooks.
Rosena Butler17-Jun-2013 19:47Hello,
Am a direct buyer for gold looking to buy 10kg to 20kg monthly, please can you link
me to a reliable seller that is no scams and time waster.
I buy on CIF to Los Angeles and can pay shipping cost direct to out shipper.
Email me: butlerconsultant@gmail.com
Thanks
Oleg17-Jun-2013 08:59@Lawrence Hello, one of my buyers is finalizing a 2kg trial deal with this seller, I hope it all goes well. lev.oleg@bk.ru
lawrence16-Jun-2013 18:35so has anybody contacted this ?gold seller??
if they only have 1?10kgs then they cant have many customers!!
Alhaji 12-Jun-2013 21:31
To all genuine buyers of gold bars, I want to let you know that we can supply you gold dore bars. If you are a direct buyer kindly contact us today for gold. We are small scale miners here in Ghana and we can supply from 1kg to 10kg only. We need buyers for long terms both on FOB and CIF.
Email: goldprospects@outlook.com
Seun16-Jun-2013 15:02My name is seun. Please is there any company bearing Galant mining incorporation in Indonesia and Australia?
www.galantmining.com They said their African employment agent in Africa is one Easy Access Nigeria Limited, easyaccess@galantminig.com, they are currently recruiting workers to work as goldminers in Australia and Indonesia. PLEASE ARE THEY GENUINE OR SCAMMERS?
A RIP16-Jun-2013 07:53Franko MINING GHANA LIMITED
P.O.Box 292 Accra Ghana
Email: donfree22@gmail.com
Tel: + 233541291733
Fax: + 23321400810
Contact:
Yam George Freeman (George Freeman)
Samuel Freeman (son)
Rita Nagel (Mandate seller)
Directed by Yaw George Freeman (George Freeman) and his son Samuel Freeman, they publish false document false SPA in order to trick you into financial instruments to be able to sell and raise funds. It uses a person named Rita Nagel (seller mandate) for the preparation of documents and other conference calls, this person is in Pretoria, South Africa. These people are extremely safe way to put you under pressure to push yourself to the fault. You find yourself in a situation where you do not want to lose your deal, and you agree to your bank officer against a bank officer who knows nothing of this.
You make your bank instrument for a period of 30 days and you?re done, you will never see the product and they have earned money by selling the financial instrument.
Martin14-Jun-2013 09:36@Andre, you can contact me by email for more details on NADISCO Ghana.
email: martinstv007@hotmail.com
paul14-Jun-2013 06:06hi has anyone had contact with midtowntraders.com either good or bad
paul mcewan14-Jun-2013 06:03Hi has anyone had contact with MIDTOWNTRADERS.Com re gold optruions or oil options
Andre13-Jun-2013 20:30Any one knows a company in Ghana trading as Nadisco?
Guest13-Jun-2013 20:21Do you know a mining company with the name of NADISCO in Ghana. Are they for real or is thid s dcam?
colin13-Jun-2013 16:53do you no enething about global world gold company from accra ghana address 2456 ochoco billa avenue k.i.a accra ghana also global freight agency accra gana
asare.thomas@rocketmail.com is email address for maniger of global world gold
colin13-Jun-2013 16:53do you no enething about global world gold company from accra ghana address 2456 ochoco billa avenue k.i.a accra ghana also global freight agency accra gana
asare.thomas@rocketmail.com is email address for maniger of global world gold
Guest13-Jun-2013 15:47www.coastalminers.webs.com
1.White Metal International Ltd
Nairobi East
Building No LR20
P.O Box 00400?12656
Mobile: 254708277571
Email: white_metalinternationalltd@yahoo.com
Contact person: Mr. Nsabimana Moussa : 254718999821
2.Company: Keka Mining Society
Contact Person: Yahaya Noor
Jobtitle: Director
Location: Kivu, Congo ? Bouenza
E-Mail Address: kekasociety@gmail.com
Phone: 243?992?232212
Fax: 243?992?232212
Website URL:
http://kekasociety.bloombiz.comAlhaji12-Jun-2013 21:31To all genuine buyers of gold bars, I want to let you know that we can supply you gold dore bars. If you are a direct buyer kindly contact us today for gold. We are small scale miners here in Ghana and we can supply from 1kg to 10kg only. We need buyers for long terms both on FOB and CIF.
Email: goldprospects@outlook.com
We get gold on weekly basis from the mining site, so feel free to contact me directly for price and terms.
Thanks,
easternfunds12-Jun-2013 09:18@Ric Its a scam, do not send her $36,000, if you love yourself
Guest12-Jun-2013 06:04Anyone know if Midtown Traders are genuine. Gold traders?
cal11-Jun-2013 17:59I?m talking to a lady friend living in Ghana, who wants to change ownership to me (i live in the U.S.) of a 1 kilo 22k gold bar and send it to me by way of Chrom cargo co., she will pay the $600 transfer fee n $3,000 of the $5,000 fee(for taxes, secrity etc?) n i will pay the remaining $2,000 to chrom cargo co. upon delivery(to take procession) of the package(bar. Is this a scam? I asked why she not sell it there n she says bcoz she doesn?t have a license to sell the bar there in Ghana. I?m suppose to sell the bar which is worth around $44,000 n send her back $20,000 she is suppose to use a small portion of the money i send back to come here n marry me. I?m telling her i will be liable for taxe?s n irstaxe?s. I also would like to know if custom taxes r include in with the fee we are paying the shipping company(i checked the shipping co. on the web n it is legit but i still wonder if they r legally able to a 22k gold bar here even though they are not a dealer. please email me someone as this is an urgent matter
M. Murrell09-Jun-2013 08:57Fahad,
I am in Tanzania right now, maybe I can do some checking for you. You can reach me at +255 785 422 684
We are involved in mining here and I have not heard of that company. Their web site is vague on their actual operations.
Fahad Hashem08-Jun-2013 09:33Hello, does anyone know what is going on with American Auropean Gold Cooperation (AEGOLD.COM). They have not processed my withdrawals for over a month, they have not replied to my support tickets, emails and voice mails again for over a month, they have not even made any announcements to the shareholders. This is seriously alarming. I know from other shareholders I know from other part of the world stating they have the same problems. As such, all my family members are shareholders as well and they are also facing the same. If anyone can tell us what is going on, I would be really thankful and grateful
Guest07-Jun-2013 16:54Has anyone been scammed by DAVID HARTMAN, white male of German decent? He was very active in 2011 and 2012, but uses different photos now as other scammers are using his photos. Please let me know if any info is available on this man?
LOKESH.V07-Jun-2013 16:04HI THIS IS RAVI FROM BANGALORE, IF ANY ONE WANTS MATERIAL IN INDIA IN DISCOUNT BASIS CONTACT LOKESH +91 7795506170
Jeffery Lininger07-Jun-2013 07:06AUSTRALIA WATCH OUT FOR THESE CON MEN JASON BROWN AND THEO VOURAKAS VOURAKAS CORPORATION SYDNEY AUSTRALIA THESE PEOPLE SHOW HIGH DISCOUNTS FISHING FOR BUYERS AND COMPLETE NONPERFORMERS EXTREMELY DECEPTIVE WITH A FAKE MANDATE FOOLS GOLD
Jeffery Lininger07-Jun-2013 07:06AUSTRALIA WATCH OUT FOR THESE CON MEN JASON BROWN AND THEO VOURAKAS VOURAKAS CORPORATION SYDNEY AUSTRALIA THESE PEOPLE SHOW HIGH DISCOUNTS FISHING FOR BUYERS AND COMPLETE NONPERFORMERS EXTREMELY DECEPTIVE WITH A FAKE MANDATE FOOLS GOLD
Jeffery Lininger07-Jun-2013 07:06AUSTRALIA WATCH OUT FOR THESE CON MEN JASON BROWN AND THEO VOURAKAS VOURAKAS CORPORATION SYDNEY AUSTRALIA THESE PEOPLE SHOW HIGH DISCOUNTS FISHING FOR BUYERS AND COMPLETE NONPERFORMERS EXTREMELY DECEPTIVE WITH A FAKE MANDATE FOOLS GOLD
Ric06-Jun-2013 14:46Has anyone heard of Mrs,.Sandra Smith? she is claiming to be in possesion of a mother lode of gold bars and gold dust!!
Needs $36000 to pay security company!!!
M. Murrell05-Jun-2013 15:05In further diversification of out group of companies, we have aquired 150 hectares of licensed gold mining area in Tanzania. All govt requirements have been completed and all testing and confirmations done. We are now ready to cut in the access easement and commission the mine. Should anyone be interested in joining us through joint venture before the start of production, feel free to email me: admin@issg-scs.com Att: M Murrell, CEO or call me in Tanzania at +255 785 422 684
I am American and President of ISSG-SCS- Tanzania Ltd.
Keith31-May-2013 02:45Excellent site! Upon tiring of the scammers and incompetents, I entered into a joint venture and bought a small Ghanaian mining concession. I am an American, and my company has been in the silver business in Mexico (silver scammers in Mexico are very similar to gold scammers in West Africa) for 14 years. My level of comfort was higher than most as my brother has gas and oil dealings with the Ghanaian Ministry of Energy & Petroleum through his company Pan-Atlantic Exploration. My name is Keith Mullen and my company Sounds of Silver LLC can be found here:
www.soundsofsilverllc.com. My email is info@soundsofsilverllc.com and phone is 614?602?1702. I cannot sell gold at the scammer price, but I can sell Ghanaian gold in the USA for less than dealers.
ray25-May-2013 22:21have sent over 45000 us dollars to quantum consolidated with no return?what do i do now?
Rowland23-May-2013 08:44Thanks you for the nice information on scammers, it has really been helpful.
Below is their emails:
Dear Sir/Madam,
First of all, thank you for spending your precious time to read this email.
Now we are commissioned by the transformer manufacturers and the gold jewelry processors in China to order gold-mining, the information of the commodity we need as bellow:
1. Alluvial gold dust:Purity (92%-99%), Quantity (50kg)
2. Ore gold: Quantity (20kg)
Note: the quotation should include Tax, in USD or Euro (FOB).
If your company can supply them, pls do not hesitate to contact with us.
Best Regards,
Wangwei.
Xi?an Yalong Import &Export Trade Co. Ltd.
Tel phone: 0086+18789411596
Guest20-May-2013 04:13I know a man as CEO at Local Refinery in London. His name is Mark James. I didn?t keep in touch with him for along time. Who can help me ? Who is known him ?
Tina20-May-2013 04:12Does anyone know of a Comfort Kanodu in Accra. She told my husband she wants to be with him, but she needs to get 5 bars of gold into the US before she comes. Supposedly the gold is sitting in the US, but there are documents missing and she needs $3800 to get those 3 docs. In the meantime the freight company is charging my husband for storing the gold and if it needs to be shipped back, he is responsible for the shipping charge.
George17-May-2013 10:52watch out for Mohamed Tchabi (Agriscape) from Benin and Tavares Joaquim. They operate in Cologne and Paris.They submit small sample of gold dust for verification and approval after which payment is made and Brass deliveres.
Brass has the same specific weight as gold. Be aware.
Guest17-May-2013 10:45Hello En,
Is it Ken Akin the same with Ken Kwadjo from Ghana and the same company?
Thanks.
EN17-May-2013 03:27Hello,
Does anyone know anything about Ken Akin Mineral Enterprises in Ghana and gold? Is it a scam?
Thank you.
Thanks
Guest16-May-2013 21:02Hi,Hope you can find out if this is a scam:I got an email from a man from Ghana, Victor Yaw Asante. He wrote first on skype, he wrote this:
Hello Petrov, I am Victor Yaw ASANTE a citizen of federal Republic of Ghana . I have in my bank the existence of a big amount of money that belongs to a customer ?.., who happen to have the same surname as yours .The fund is now without any claim because Mr?.. died in a deadly earthquake in Japan in march 2011 . I want your cooperation so as to make the bank send you the fund as the beneficiary and next of kin to the fund. This transaction will be of a great mutual assistance to us. Send me your reply of interest so that I will give you the details .
Strictly send it to my private email account : ( victorasante01@hotmail.com )
At the receipt of your reply, I will give you details of the transaction. And a copy of the Deposit Certificate of the fund and also the Incorporation Certificate of the company that generated the fund .Yours Sincerely,Victor Yaw ASANTE.
I believed at him,because he first contacted me on skype,his Picture is also there.
Now Ive been researching and found out its alot of scam out there from Africa. Is this man a criminal? He keeps on contacting me on email and skype. I have been sending him all my details (Ive been talking to my bank,so he cant do nothing there),but I also sent a copy of my Passport?Should I contact the police? I start believing this man?
Guest16-May-2013 09:56Goldia Imc are scammers: (My company called goldia international mining company and is based in sierra-leone and guinea-conakry I am selling gold and diamond right now I am having few regular clients from usa, canada and dubai and I wish to have more clients interested on buying a large quantity because my father in law hand over his business to me he wants to rest he is old so I hope to succeed)
Guest15-May-2013 11:05does anyone know if this company is a scam Goldia Imc there supposed to be from Guinea Conakry
Todd S15-May-2013 07:49I have got relaible gold sellers that can work with PMMC of Ghana and on CIF.
If you re direct buyer and needs help kindly contact on Email: tseigmeister@aol.com
Thanks,
Todd
Aaron10-May-2013 12:35Hello Grant, please can you explain on this forum your ordeal with midtown traders,
Am waiting to hear from you, or kindly provide your email.
grant10-May-2013 09:06beware of steve richards from midtown traders in new york . dont ever trust these people or you will end up like me.
ken hindes09-May-2013 08:13hello there i have been dealing with a gold company based in singapore called
tianjin pudong global express pte ltd and i am getting concerned about it might be a scam
have you heard of this company
thanks ken hindes
JUS08-May-2013 03:55Veit Kraus is seriously in hot water, he is currently under investigation with severe consequences pending.
Note: From this point forward, the international codes will be strictly enforced to exculde all intruders that send out false information.
Those who submit false NCNDA/IMFPA, LOI, SCO, FCO, documents WILL BE CHARGED WITH A CRIME.
If there is no response from a sender in a timely manner, it will be reported t the FBI, ICC, and Interpol. THIS IS A FEDERAL OFFENCE.
This went into effect on the 15th of November 2008 after a meeting was held between the Federal Reserve, European Central Bank, Interpol, FBI, and CIA.
By alerting all Honest Brokers and hard working intermediaries is the correct and ethical thing to do and the reason behind me putting this up on the net.
This person Veit Kraus will lead you to nothing as he does not have the capacity or intellect to complete any commodity transaction, that he claims nor has he ever closes a transaction that he prides himself on.
We can all make claims and state our own success but the truth be known that this man is an absolute fraud, circumventor and is driven by pure ego and there is no support to all he claims
Here are some of the Claims Veit Kraus prides himself on.
Authorised Gold mandate for the Russian Govt ? and has been in meeting with Putin himself ?
Authorised Gold Mandate to the Saudi Royal Family ? to sell their Gold ?
Authorised Gold Mandate for a Japanese Multinational who has 500,000mt of Gold in Hong Kong at a 9/6 discount ?
Authorised Gold Mandate to American Express to sell their Gold Holdings Globally ?
Authorised Gold Mandate to UBS Switzerland and can supply any quantity you require ? Claims that the Head Person inside UBS is his next door neighbour ?
These are a just a few of his ridiculous claims in which i ask everyone to have him show you his Authorised papers and incase he has downloaded them himself of the net ( fake ) please call the person on the papers he might present and ask if it is at all Genuine, you will soon come to the conclusion that he is a fraud and you will save yourself the daily lies that he will conspire to keep you there until he can strip you off all the information you have and then work away to deceit you from any deal that has any chance of concluding.
If you ask yourself why would he make such claims ? the answer is very simple, he uses the global network of brokers to attain all information on who the sellers are or who the buyers are, as he plays both sides of the fence, to only collect this data and serve himself in the most selfish way possible with out including you at the end.
This pathetic and appalling attitude is why he has never transacted in Gold and the catalyst for him to move into the BOND Business now as he is in search of new victims as the Gold Circles are onto him.
So if he is claiming the same rubbish in Bonds with his partner Guenther, please walk away as you are surely walking into a mine field of trouble.
Let it be known that three years ago Veit was fired from his employment with Aldi, the try to setup and run a solar panels business ( Green-ray ) which collapsed and to further show how troubled this man is he ran off with his secretary in which his Mother and children have completely disowned him.
His stability above is a reflection of who you are dealing with , KEEP AWAY from this mentally ill old man.
Veit Kraus
CEO
element resources
Lohstr 23
D-92699 Bechtsrieth
Tel +49 961 2067 6056
Cell + 49 176 995 389 02
Fax +49 961 484 96106
email vk@element-resources.de
Skype greenray6
Yusup khan01-May-2013 13:37Gold dust n Gold bar scamer.
Al haji Tamimu of Accara-Ghana.
Monile :+233266534554
+233204206020
+233242974660
Faik Website of Courrier co of Accara,Ghana.
Name : Ship to any place in time . com
Mobile: +233248141997.
They will ask 7% to export charge and never deliver the goods
Yusup khan01-May-2013 13:34Gold dust n Gold bar scamer.
Al haji Tamimu of Accara-Ghana.
Monile :+233266534554
+233204206020
+233242974660
Faik Website of Courrier co of Accara,Ghana.
Name : Ship to any place
Www.shiptoanyplaceintime.com
Mobile: +233248141997.
They will take the 7% cost to export from their country to any place in the world and then they will never deliver the gold.
ANON27-Apr-2013 11:51STAY AWAY FROM THIS SCAM LEADER NAMED: ?SOLO?
OUAGADOUGOU, BURKINA FASO.
HE SAYS HE HAS GOLD POWDER AND AT THE LAST MOMENT OF TRANSACTION THE GOLD POWDER IS SAND.
ANON27-Apr-2013 11:51STAY AWAY FROM THIS SCAM LEADER NAMED: ?SOLO?
OUAGADOUGOU, BURKINA FASO.
HE SAYS HE HAS GOLD POWDER AND AT THE LAST MOMENT OF TRANSACTION THE GOLD POWDER IS SAND.
Kingtide26-Apr-2013 04:56Quantum csld..stay away from these rogues
Kingtide26-Apr-2013 04:43Quantum consolidated are yr friends till you deposit money into their account.DO not trust them.They do know what they ate talking about regards to gold so take their knowledge and invest yr money independently into the market.A guy called jacob will call and try to con you into investing with them.
renjith23-Apr-2013 16:33is anybody knows about VEEKAY GOLD TRADING LTD. or Mr.Victor of these company, if u know the company or about there dealings pls mail me on adithyadealers@gmail.com thanks
renjith23-Apr-2013 16:31is any body deal with VEEKAY GOLD TRADING LTD. if any body know more abt these company and there deal pls mail me to adithyadealers@gmail.com
Liz23-Apr-2013 13:05Good information
1. CHARL & JP: R CO LIMITED
P.O.BOX 5021 ACCRA.
ACCRA-GHANA
Phone: Cell:+233?245?663406/ 245663406
charljprcoltd@gmail.com
2. SAWYER GOLD COMPANY GHANA
15,DADEBAN ST ACCRA,GHANA
TEL;+233?540?906?706
+233?274?826?434
+233?241?769?064
+233?272?892?767
EMAIL:doctorsawyer2324@gmail.com
doctorsawyer@yahoo.com
skype; doctor.sawyer
3. MTMC Gold Corporation
Fifth Burges Road,
New ham,
London E6 2EU,
United Kingdom.
Telephone: + 44 (70) 31816548 / 7031816548
Telephone: + 44 (70) 31831748 / 7031831748
Fax: + 44 (70) 23075956 / 7023075956
Email: mtmc@mail2uk.com
Telephone: + 233 (26) 6844856 / 266844856
Telephone: + 233 (24) 1920242 / 241920242
Email: mtmc@mail2uk.com
4. Gold Mark Mining Company
CONTACT INFORMATION:
HEADQUARTERS,
GOLD MARK MINING COMPANY LIMITED
224 FANEFA WAY,
ACCRA-GHANA,
00233.
TEL: 00233?24?1141613 / 241141613
FAX: 00233?21?785409 / 21785409
KUMASI BRANCH
GOLD MARK MINING COMPANY LIMITED
7 OLD MINE ROAD
KUMASI-GHANA
Benin Branch
4 Port way
Cotonu-Benin
+229?97?441675 / 97441675
Dr.Kojo Banku (Managing Director)
goldmarkcompany@yahoo.com
goldmarkcompany@gmail.com
5. AFRICA PURE GOLD COMPANY LIMITED
JOHN MANSON
P.o.Box 17416
Accra // GHANA
Email africapuregold@gmail.com
Email africapuregold@zoomshare.com
TELL 00447031746630 / 7031746630
Mobile 00233243432615 / 243432615
6. Aviamash Diamond Comapny
Name: Smith Adjei | Phone: 233?28?7276053
Country: 86 | Code: | Fax: 233?21?216511
Address: Adom House, Assin Ofosu street, East Accra Accra Accra 00233 Ghana
Any offer from this group is a scam.
Thanks;
Noel Megumichan
Email. noelmegumichan@yahoo.com
1. Aduku Addai Group Mining Co.,
Executive Trust Building
Suite 700
Accra Central ? Ghana
Nana Aduku Addai (Director)
Tel: 233 244 467 291 / 244467291
233 266 646 076 / 266646076
E-mail: admin@adukuaddaimines.com
Skype: goldfeathers88
2. Gold Stone Resources
Address:
Motoway roundabout 7 floor Gyau Towers
Near the Asokwa Agyaku towers 2 floor
Tema And Kumasi Greater Accra 00233 Ghana
Tel:+233030302361 / 030302361 Email:stoneghana@mail-me.com
Line1:+233277199227 / 277199227
Line2:+233243977094 / 243977094
Line3:+233287300738 / 287300738
3. Otingo Mining Limited
ERNEST DOGBEY CALDWELL
+233245678092 / 245678092
Quantity: 1000 kilograms available monthly
Quality: 22. karat alluvial Au
Origin: Ghana, West Africa
Price: $7.500.00 per kilogram
4. Michael Nikiforuk, President
Email: majn@goldtradingsarl.com
Marco Durante, Vice President
Email: mjd@goldtradingsarl.com
Nana Ado, Director of Operation
Email: dnado@goldtradingsarl.com
Mensah Alice, Financial Secretary
Email: malice@goldtradingsarl.com
5. KERYONG MINING CO. LTD.
mining_keryong@yahoo.com
P. O. Box AN6662* Accra * Ghana
To contact us by phone:
+233 27 690 7643 / 276907643
+233 20 739 8186 / 207398186
Or by fax: +233 22 403 151 / 22403151
GOLD AND DIAMOND SCAMS23-Apr-2013 12:42Certified List of Scammers and non performers in Gold business, beware of any offer from these group.
1. Company: Tetremma Consultancy Ltd
Contact Person: Boakye Dankwah, Executive Director
Postal Code, City: 23321, Accra
Country ? Province: Ghana ? Greater Accra
Phone: 233?21?258339
Fax: 233?21?258339
2. Escco Company Limited
Address:
Oxford Street, Osu Re, Accra, Accra, Ghana
Telephone: 233?28?7276053
3. Mr. Raymond Akase
Company Name: Tetremman Marketing Limited
Street Address: P. O. BOX NB 46
City: NiiBoi Man
Province/State: Accra
Country/Region: Ghana
Zip: 00233
Telephone: 233?243?755503
4. Government Approved Gold Dealer Company Limited
We Need a Customers for our Fresh RAW GOLD And DIAMOND Oct 28, 2010
Jerry Nelson Mensah
Tel: 0545392666?0265120629 / 545392666 / 265120629
Office tel: 021916286 / 21916286
E-mail: jerry.mensah88@yahoo.com
5. Aduku Addai Group mining Co.
Executive Trust Building
Suite 700
Accra Central ? Ghana
Nana Aduku Addai (Director)
Tel: 233 244 467 291 / 244467291
233 266 646 076 / 266646076
E-mail: adukuaddai@yahoo.com
Skype: goldfeathers88
Tom19-Apr-2013 17:12Hello
I am a buyer from the Bahamas and I became interested in your company after reading your posted message a few times:
However I would like some more details like: what is your price per kilo of 22karat gold bar;
would you ship to the Caribbean; and will I have to come to Ghana to personally finalize a transaction ? ?
I WILL BE AWAITING YOUR RESPONSE , ?
THANK YOU
Tom
Melvin15-Apr-2013 13:45Vey nice place to get information, I will send some scammers to this list also.
Thanks,
Melvin
m_akridge@aol.com
pete12-Apr-2013 12:44tash i would like to have a private conversation witn you may i have your details?
Guest12-Apr-2013 06:39BE AWARE OF ANOTHER SCAM ARTIST .. HIS NAME IS MATTHEW MUNRO. THIS GUY CLAIMS TO HAVE SAND FILLED WITH GOLD, SILVER, TITANIUM, ECT AND HE?S NOTHING BUT A BROKE ASS BUM !!!! HE ALSO CLAIMS TO HAVE DEALINGS WITH PRECISION DRILLING, WHICH HE DOESN?T, HE CLAIMS HE CAN BRING UP THE PH BALANCE IN CONTAMINATED WATER HE CAN?T, HE CLAIMS HE HAS DEALINGS WITH QUANTUM SILVER .. HE DOESN?T. BE WELL AWARE OF THIS MAN !!!!!
Tash28-Mar-2013 04:59Ok so I just found out that quantum consolidated aka quantum csld are a scam company.. emails:s.richards@quantumcsld.com k.paxton@quantumcsld.com and so on do not deal with this company?
Darryl24-Mar-2013 14:06hi, can anyone help me on how i can get the full list of licence exporter of gold from ghana. im having a hard time checking on the internet and some links. hope someone can help or does the government of ghana can help us to verify the authenticity of a certain export license.
thanks for anyone who can help me.
Guest22-Mar-2013 16:09Anyone heard of gold coast investment? Please respond
Guest20-Mar-2013 10:19Mr. Madi how to contact u??????.priyesh.chanu@gmail.com
Guest
spenc09-Mar-2013 12:55Well they keep coming, will call him a time waster and let you decide if scam ring.
There is Seller / Company from Benin Alleging to have AU in Dubai 31kg and London 51kg, in bonded warehouse, however need upfront payments before assay of around $181,000usd to be made to release shipment. In addition the Seller wanted monies firstly to be sent via western union for hotel for his representative in Dubai. Buyer was in Dubai waited to meet representative in Dubai to sort out monies and transaction, sellers representative no show, no evidence of SKR or Documents could be provided by the seller only interested in buyer personnel and company details, before any information given out.
Company: family gold
Country / origin: Benin
Skype: family gold and diamonds
Contact name: Ahmad Shola Ousman
Contact numbers used: +22967440755 / +22968476255 / +447035924108
Email: family.gold@hotmail.com
This person contacted the buyer direct, who happened to be visiting Dubai last minute, we have no idea how he got his details. Luckily the Buyer passed the details over for us to follow up and push if there was a deal to be done. However it is found to be time wasters, who are more interested in upfront payments before giving details of product or proving.
Checks on contact number undertaken, found linked to other people and alleged business. Please understand I will tell time wasters. We have buyers and Sellers of AU(genuine). THIS IS GREAT PLACE FOR INFO. Lessons to be learned don?t jump or pay upfront fee?s until due-diligence is done on buyer or Seller.
Domenico07-Mar-2013 07:23Good evening Steve and Michael, I am typing from Italy and I have been looking for serious and professional suppliers of gold based in Ghana and Tanzania, who could also work on CIF basis with POF against POP sent in advance(possibly genuine documents, because we have some proper intelligence instruments to discover cheaters). I would be pleased to cooperate with you, so feel free to contact me at domenico.decclesis@libero.it
Steve05-Mar-2013 23:50Hi, Michael, am looking to buy gold bars in small quantities of 5kilos, please kinldy
Contact me. My mail is: martinstv007@hotmail.com
Thanks,
Steve
Micheal Smith02-Mar-2013 10:50We for the first time succesfully bought 10kilos of gold from Accra Ghana for the first time, all thanks to this site and the admins help. We are grateful.
Guest27-Feb-2013 21:27Excebra International Limited, headed by its CEO Emmanuel Alade, Blue Metals Mining & Export, and Custom Cargo Handlers supply digitally altered documents to include the information of the transaction. Not sure who Falsified the documents, but I do know that the telephones used as Blue Metals telephone is a cellphone associated with another company, +255 779113857. Watch out for these people.
SUPREME COURT22-Feb-2013 22:42This is to announce to the general public to be careful of Diplomat Li Dal Park, Dr Richard Osei and the fake Armor Group Security Company Ghana. They are all one person, a very High Profile cheats and scamsters. They make you believe every other people are thieves like them, We encountered problem recently on their various tricks to fool Americans, Europeans and mostly Asian and extract money from them that one fake diplomat Li Dal Park is coming with consignment.They are con artists.
Friend17-Feb-2013 09:12prisma agencies and barax mining at Tanzania is operated by Simon kabila and pino kabila both are scammers. Stay away from those peoples. If any body wants any evidence of there scam plz check with me. They have chopped my money.
gloria16-Feb-2013 19:49There is a steve blanson on here. This is a group of scammer?s from ghanda and I have their phone number. These men are all over the scocial net work scamming women for money. Thses naes and opics of them are stolen off the netwroths.
Tash15-Feb-2013 03:25Hey all Just wandering, I saw someone down the list ask if anyone knows of quantum csld aka quantum consolidate.. please if anyone knows anything about this company get bak a.s.a.p.. Tyuh
Joseph13-Feb-2013 18:05We have gold bars available. Kindly contact me for more details.
FOB GHANA ONLY.
Email: nkanetetegold2011@gmail.com
Guest08-Feb-2013 12:54Beware of Ali Conte, Mousa Jabiru Toure, Drissa Konate, Doumbouya Lancinet. They are all from Conakry, Guinea. High Profile cheats and scamsters. They make you believe every sob story, I just wasted 14,000 USD on their various tricks to fool me and extract money. Fake documents. They are con artists.
Michael M01-Feb-2013 01:26Jason,
I am really sorry that your father lost a lot of money on gold scams, but you bring up some good points. There are a few simple rules just to start with that should always be observed to avoid being scammed.
First of all, never even consider a gold deal on a cold call or unsolicited email. This will always be a scam.
Remember that there is no legitimate person or company that will sell you large amounts of gold direct to you. Legitimate gold is sold to refineries.
Anyone offering a huge discount on gold should be immediately flagged as a scam. Even refineries do not pay outright for gold, until it has been refined. Then they pay according to the weight of gold after the refining process, and at the rate of pure gold at that point.
Playing the market on gold is different as the gold is bought and sold through the market, you will never touch it or see it. It is like any other commodity where you buy and sell according to the current rates.
Gold is at a great rate now and will probably continue to go up. the only way to earn on gold is to invest in the actual mining of the gold. There is a risk no matter how you enter into this type of situation. You can either invest in yourself and go out there and dig it up yourself, or you can invest in a mining license or claim for the production of gold.
We opted to go through the process and obtain primary mining licenses for 150 hectare of area to mine alluvial gold in Tanzania. The process was long and the effort huge to finally obtain the proper licensing, but worth it in order to control our own capability and not rely on others.
There is no ?too good to be true? ventures out there.
Brigitta Alano29-Jan-2013 02:14Anyone heard of a Charles Kweh trying to sell over 200kg of gold? Over a quarter of a million dollars have been siphoned out of people including a friend of mine. Charles in Ghana.
Michael M24-Jan-2013 15:53I am happy to say that our Environmental Impact Assessment has finally been approved. This was the last step in the ?Legal? process to conduct mining operations in Tanzania. Just as a note, I had come down with Malaria on one of my needed trips to Africa, but now better prepared.
Guest24-Jan-2013 09:06Confirmed Scammers and absolute time wasters
Xavier Oliver Onyango
Eastern Trans Line Tanzania
Phone: +254718614869
+255752599999
Tel:+255222647865
Mbezi Beach, Plot №712, House
Number 324 Kawe Road
Dar es Salaam
United Republic ofTanzania
Michael M22-Jan-2013 18:27Ronald,
You are absolutely correct. If you actually invest in a proper licensed mining operation you can earn. However, this is like any other investment and always has a risk. Certainly make sure that the operation is legitimate and not another scam. We have spent months to get tour licensing in Tanzania and now can get underway with the actual operation. There is money to be made but not buying gold.
Ronald18-Jan-2013 08:47I have been in Ghana and got scamed by these crooks?..There is no Gold with these people, one more thing I noticed is that Gold price is published on front page of newspaper daily?PMMC buys gold from anyone at these published rate without any question?then why they want sell in dicounted rate? If we buy at market rate we will end up in loss due to transportation, insurance cost?.the only way to get Gold is official way through mining..
Roger T15-Jan-2013 14:56Am currently in Accra Ghana right now for a 500kg gold deal to USA, to be assayed
At PMMC. Email: rojertaylor@aol.com
South Africa14-Jan-2013 11:40biggest crooks in Mali and Ghana. in Mali is Mr Brehima Gakou and Mr Diallo Abdarahmane. Gakou of Sicomp Sarl Company and Diallo has a travel agency and Clearing Company. Very big crooks without care and concern. Dont waste your time with the authorities in Mali . they are all bought with your money. We should take this up on International level. Even Interpol in the country is corrupt. Justice system even worse. Why wont Interpol list them ? i dont know. anyone who thinks they have a genuine deal in Mali < Guinea or Ghana is fooling themselves. Get a gold mine direct from the authorities and work thru the hard way thru their Investment Promotion Centres. If i save one person with my words , perhaps the Lord will help me bring these thugs to justice.
Michael M12-Jan-2013 06:50Good day, I can only speak in regards to Tanzania and gold. From personal experience, and having the mining licensing in place for gold mining, you will never find any gold to purchase personally in Tanzania. If by some miracle you actually found an amount of gold and purchased it, you would never legally get it out of the country. No legitimate gold mine would ever sell their gold at these huge discounts that I see on this page and generally on the net.
The only way to make money on gold is to be part of the mine. That being said, I am not encouraging everyone to go and try to find a mine to become part of, as you can get scammed just as easily on that.
There are very specific and time consuming processes to go through for obtaining licensing to operate. It had taken us 6-months just to get our Environmental impact statement and feasibility studies approved, and that is not free.
The good part is, that once you have the proper licensing, exporting of the produced gold is relatively straight forward and not difficult. Therefore, a legitimate producer does not need to sell gold at a discount to individuals.
Michael M12-Jan-2013 05:37I really like your site. I can tell you that we operate in Africa, specifically Tanzania and that in our experience, you will never find an actual gold purchase deal from anyone. Any legitimate mine that produces gold, already has the resource to sell it out and export. There is a lot of government documentation that must be done through legitimate means and this requires licensing.
Rojer Taylor03-Jan-2013 18:10Thanks for all the post, I will be travelling to Ghana on the 15th of January to initiate a gold business transaction with reliable and trusted gold sellers. Buyers looking for sellers are free to contact me. Email: rojertaylor@aol.com
Bizking03-Jan-2013 14:04Hey guys you all are doing a wonderfull job by contributing to this blog. Great. I would like to inform you all that even TC HOLDING AG , from Europe is a scammer . The company is represented by Gunter Monseller and their mandate Sumeet Gupta. Please be aware from these people as they are real scammers.My client has given them $10000 for a RWA/pre advise for leasing a BG but in vain. My client would be filing a legal sue very soon.
I really want to know if someone has really closed a deal of leasing any bank instrument. There are so many clients in the market who are looking for leased bank instruments , Are they just wasting their time ?
Amanida30-Dec-2012 12:07Visit us today for all your gold business and transaction. With us you are 100% guaranteed to get gold dore bars.
www.amanida.getafricaonline.com
Madi30-Dec-2012 04:38I have been dealing with the Barax Mining for a while and we are going to close the deal soon. They haven?t asked for any cent from me but just the SBLC from my bank. Will it be safety? Please guide me. Mr.guest, how did they con you?
Guest30-Dec-2012 04:05I have been dealing with the Barax Mining for a while and we are going to close the deal soon. They haven?t asked for any cent from me but just the SBLC from my bank. Will it be safety? Please guide me. Mr.guest posted on Dec.21, how did they con you?
Madi30-Dec-2012 03:57I?ve been dealing with Barax Mining for a while. We are about to close the deal. They haven?t asked for any cent from me but just the SBLC from the bank. Is it safety? How did they con you Mr. guest? Please guide me. Thanks.
Michael A27-Dec-2012 13:00I lost money to someone in Mali, is it posssible to get my money back? Someone please help.
lucy27-Dec-2012 09:25Attention here is the list of broker floating around collecting information ? These linkedin brokers are real scammer what is the meaning of scam is deceit;
Norman, William Burt, Carl Dutcham, Brad hostseller skype: osanjoe, Aide be careful dealing with these people FCO and Manifest cut and paste they are fake Contact: Mr. Steve Roach steve@trintexinternational.com tammy@trintexinternational.com goldbroker
Hoftman GUZMAN hguzman@kingdomcapital.ch Herr H. GUZMAN, Partner gold broker
hguzman@kingdomcapital.ch Corporate Finance Praxis
+41 0(76) 206?9599 Kingdom Capital (Z?rich) AG
PIN:287C192C Bahnhofstrasse 92
Follow us on Twitter: @kingdomcapita CH-8001 Z?rich
Switzerland
Rizwan Alam R. A. International gold/diamond agent USA
Anthony Eccles? caga311@googlemail.com gold bullion/buyer mandate UK
Saleh M.A.Wahashi salehmaw@yahoo.com agent /diamond and gold Saudi Arabia
Jeremy Sulzbacher 2nd Your Newsletter is Important ? to YOU diamond /buyer agent
Antwerp Area, Belgium
Mr. Kanwar BS Salwan; 4 gold group Ltd. scammer
21 Dundas Square Suite 618
Toronto
MSB187 Ontario
Canada
Tel: + 416 214 2442
lucy27-Dec-2012 08:1324 gold group Ltd.
21 Dundas Square Suite 618
Toronto
MSB187 Ontario
Canada Tel: + 416 214 2442
Mr. Kanwar BS Salwan; this is the man who scam Ancient Mining Company 5 kilo worth $ 250,000 his broker in the name of Hadi Hossein be careful of this hustler buyer they are thieves.
hello27-Dec-2012 00:27hello
hello27-Dec-2012 00:27hello
Derick26-Dec-2012 18:29Johson am in Tanzania for three month now am looking for really supplier can you please confrim about the company
I am now in Tanzania I have been offered many gold deal but I have one company called Kasulu Trading we have done deal of 2kilos of gold nuggets and now we want to take big quantity to dubai they asked me to pay for all cost to dubai..
Is it safe for the first FOB we did well this second will it be safe
Cedric Basson26-Dec-2012 17:50Hello Friend,
Can you please help me on this I have one company in Tanzania we are about to close the gold deal 200kgs of gold nuggets and this people hven?t ask any single cent from me company name Kasulu Mine
Cedric Basson26-Dec-2012 17:48There is a company in Tanzania am about to do business with them we will close the deal after christmas ends 200kgs of gold nuggets it called kasulu Trading and they haven?t ask me for any single cent.
Guest21-Dec-2012 08:29Huge scammers, stay well away, Barax Mining, Simon Mukulu and Daves Myonkoni, confirmed scammers, have conned me.
Steve Constantine19-Dec-2012 17:40To all, please be aware of Martins Doukolo of STE International, Benin. Posed as plausible buyer, took the money and ran. I am inundated with false offers. I have genuine buyers who will purchase bullion and raw gold in large quantities on CIF basis, direct to refineries too. Please help if you are genuine miner/seller. Thank you.
Guest19-Dec-2012 15:10i have had dealings with iris washington. in my experience she is honest and trustworthy. just because a transaction does not happen does not mean it was a scam.
Marco14-Dec-2012 11:14Xavier Oliver Onyango Eastern Transline Tanzania end Olipro??????
ken davies13-Dec-2012 08:11follow the proper guidelines when doing business in sierra leone.sellers need cash, so they do not hold large quantities of gold dust, unless you make a contract on the ground you will never get 1 ounce of gold.sellers need export certificate which costs 40.000 usd .use governt ggdo to test goods prior to shipment,if seal is not in place before shipment take it back to ggdo and test and reseal.
kevin o brien13-Dec-2012 08:09follow the proper guidelines when doing business in sierra leone.sellers need cash, so they do not hold large quantities of gold dust, unless you make a contract on the ground you will never get 1 ounce of gold.sellers need export certificate which costs 40.000 usd .use governt ggdo to test goods prior to shipment,if seal is not in place before shipment take it back to ggdo and test and reseal.
Guest11-Dec-2012 17:19MERCI INTERNATIONAL GOLD MINE Ouagadougou ?Ouga? BURKINA FASO
Warning do NOT deal with these guys they are time wasters scammers and petty thieves.
The scammers time wasters & petty thieves are.
Mr. Kabore 0022678864582 the head of the company
The Dr. 0022678626006
Issac Sawadoga 00226 78434749, 00226 60032888
Ifada. ?petty thief?
0022679069613
0022672448898
0022666752410
Website: mercinternationalgoldbf.com does not work
Skype: merci.international.gold.mines.company
They will lure you in by offering a good price (US$35,000.00) with a pro-forma invoice / contract, then demand money for taxes. If you pay the taxes they then increase their price to LBMA -8%.
They start scamming you from the moment you deal with them, firstly a demand for monies for visa payment, then you pay for the actual visa when you arrive in Ouagadougou ?Ouga?.
We know one company who paid for TTI they were told the goods were shipped to Paris but theres been a problem so the gold had to be returned to Ouga. Three months later they still haven?t received their consignment.
All the employees are offering to cut side deals ?behind Kabore?s ?back claiming they can get small ? large amounts from villages but need petty cash for it to happen. +- $3,000 ? $10,000. This too is a fraud / scam.
The whole company are in on any side deals etc. they all share the same skype address and take turns answering calls pretending to be each other.
Guest10-Dec-2012 19:21Does anyone know of a Duncan Karim?
Guest10-Dec-2012 07:39Confirmed scammer and time waster.
AWUDU YAHAYA ? passport no. H1344842
Company: HELAL MINING COMPANY LTD
P.O Box CFC 9 STREET, 611 TESANO ACCRA WEST
preciousmetal25@gmail.com
PHONE +233 231157086
Your Friend09-Dec-2012 08:24Be aware of Barax mining in Tanzania, Simon mukulu kabila, pino Kabila, Minja , Moases they all are one team . Simon mukulu kabila, pino Kabila are congolean operating in Dar e sallam . Stay away from these peoples they are big scammers.
BUYER08-Dec-2012 22:03[14:09:24] johnson.msaki2: Bring client ,we steal.we share money together 50%
[14:09:35] BUYER:steal ???
[14:09:53] BUYER:do you really think i am that kind of person
[14:10:01] BUYER:steal something from another one ???
[14:10:09] BUYER:i never do and will never do that
[14:10:12] BUYER:shame
[14:10:33] johnson.msaki2: Ok
[14:11:02] BUYER:just the same you do with michelle
[14:11:08] BUYER:50 /50 to steal me
[14:13:06] johnson.msaki2: Michelle
[14:13:08] johnson.msaki2: No
[14:13:32] johnson.msaki2: She just steal her self
[14:14:00] BUYER:you are the good one and michelle is the bad one
[14:14:05] BUYER:that is how you play now
[14:14:20] johnson.msaki2: Yes
[14:14:23] BUYER:ha ha ha
[14:14:34] BUYER:you really think i am crazy
[14:14:36] johnson.msaki2: Eat white people money
[14:15:47] johnson.msaki2: So you need money bring client and pretend you know nothing then we eat together
[14:15:58] BUYER:no thanks
[14:16:06] BUYER:i rather die before i do something like that
BUYER08-Dec-2012 22:03[14:09:24] johnson.msaki2: Bring client ,we steal.we share money together 50%
[14:09:35] BUYER:steal ???
[14:09:53] BUYER:do you really think i am that kind of person
[14:10:01] BUYER:steal something from another one ???
[14:10:09] BUYER:i never do and will never do that
[14:10:12] BUYER:shame
[14:10:33] johnson.msaki2: Ok
[14:11:02] BUYER:just the same you do with michelle
[14:11:08] BUYER:50 /50 to steal me
[14:13:06] johnson.msaki2: Michelle
[14:13:08] johnson.msaki2: No
[14:13:32] johnson.msaki2: She just steal her self
[14:14:00] BUYER:you are the good one and michelle is the bad one
[14:14:05] BUYER:that is how you play now
[14:14:20] johnson.msaki2: Yes
[14:14:23] BUYER:ha ha ha
[14:14:34] BUYER:you really think i am crazy
[14:14:36] johnson.msaki2: Eat white people money
[14:15:47] johnson.msaki2: So you need money bring client and pretend you know nothing then we eat together
[14:15:58] BUYER:no thanks
[14:16:06] BUYER:i rather die before i do something like that
Guest08-Dec-2012 15:03Confirmed Scammer and absolute time wasters. Dont waste even a second of you life on them.
Golden Age Mining Centre
MR.KWAME AKYEMPEM
Address; # 2 Boaposem street.
Nana Kofi Ansah House,
Akyempem ? Tarkwa, Ghana.
Landline: +233?3070?34409
Email: gageminingcentre@yahoo.com
Guest08-Dec-2012 14:59Confirmed Scammer and absolute time wasters. Dont waste even a second of you life on them.
Emes Business Agency. Ltd.
Mining consultant
PO . Box 101 AC. Accra Ghana .
Tel/ +233243118005
E-mail: emesbusinessagency@gmail.com
Website:
www.emes.biz.lymail you if you need any information.
RAMIZ07-Dec-2012 10:12Please be aware of Eastern trans line Tanzania limited,
www.easterntransline.com It does not make sense to sell gold at $42 000 to anyone. Apparently they need 6% cash to arrange export documents. BE AWARE, YOU WILL GET TAKEN FOR A EXPENSIVE RIDE!!!!!
DEE06-Dec-2012 13:28FOR REAL BUYERS OF GOLD, PLEASE CONTACT US WE DO NOT ACCEPT ANY CASH UPFRONT OR RIPPING WE SHIP THROUGH BRINKS. CONTACT ME ON.
real buyer real seller01-Dec-2012 07:47Dear all, could you please forward us all information of scammers to our sequretrade dot com website? We are compiling a working list of scammers in Africa in order to verify ligit sellers as well as buyers. We encounter numerous scams and do verification as well as transactions on behalf of our clients, making a blacklist an important factor. And they adapt as fast as internet virusses.
Guest28-Nov-2012 04:19DOes anyone know QuantunCSLD, or Quantum Consolidated
M.J Lourens27-Nov-2012 05:23Plse advise if destiny international in sierra leone is real gold
thys lourens26-Nov-2012 13:33please advise if any of this names are scams
family inheritance gold Dr Wilson bakari
amin toure city king sari
khader Salif
nana aduku addai
aa minerals group
samuel mensah
sunu borum
thys lourens26-Nov-2012 13:10please advise if any of this names are scams
family inheritance gold Dr Wilson bakari
amin toure city king sari
khader Salif
nana aduku addai
aa minerals group
samuel mensah
Reyes Trust & Finance26-Nov-2012 10:35Cameroon: Beware Abenelang Abessolo, so called Director of Mines working with Elias Hans of alledged IM Logistics Cameroon and Bamusi Cor Miners, Mrs Dondy Techlaire Syble. All fake. They use fake passports, Airwaybills etc. The only thing that is real is the money we sent them.
Reyes Trust & Finance26-Nov-2012 10:35Cameroon: Beware Abenelang Abessolo, so called Director of Mines working with Elias Hans of alledged IM Logistics Cameroon and Bamusi Cor Miners, Mrs Dondy Techlaire Syble. All fake. They use fake passports, Airwaybills etc. The only thing that is real is the money we sent them.
Guest25-Nov-2012 07:39Edward williams from Guinea and serria leone
williamsedward377@gmail.com
Guest16-Nov-2012 18:13***** STAY AWAY FROM THE FOLLOWING SCAMMERS*****
1. MERCI INTERNATIONAL GOLD MINES COMPANY (MIGMC)
Taore Doura
REGISTERED: RCCM/GDI-INC/0992825B/1997
migmc@live.com
skype: merci.international.gold.mine-co
Cell # 011 226 780 76055
Home # 011 226 503 245650
Office # 011 254 701 023 449
THEY WILL ASK YOU FOR SHIPPING FUNDS AFTER YOU SEND THEM SHIPPING FUNDS THEY WILL COME UP
WITH EXCUSES FOR YOU TO TRY & SEND THEM MORE FUNDS, OR TELL YOU THAT THEY NEED MORE FUNDS TO CLEAR THE GOODS AT THE AIRPORT. THEY ARE VERY GOOD WITH MAKING THEIR DOCUMENTS LOOK VERIFIABLE DO NOT DO BUSINESS WITH THEM THEY ARE ALSO BLACKLISTED WITHIN A FEW REFINEIES WORLDWIDE AGAI STAY AWAY FROM THEM OR YOU WILL REGRET IT
***** STAY AWAY FROM THIS MAN & HIS SO CALLED COMPANY YOU HAVE BEEN WARNED *****
COMPANY # 2
STAY AWAY FROM MR. EVANS YUBOKU FROM GHANA, PRETENDS TO ALSO BE IN THE UK ( LONDON ) OR DUBAI
Guest16-Nov-2012 18:13***** STAY AWAY FROM THE FOLLOWING SCAMMERS*****
1. MERCI INTERNATIONAL GOLD MINES COMPANY (MIGMC)
Taore Doura
REGISTERED: RCCM/GDI-INC/0992825B/1997
migmc@live.com
skype: merci.international.gold.mine-co
Cell # 011 226 780 76055
Home # 011 226 503 245650
Office # 011 254 701 023 449
THEY WILL ASK YOU FOR SHIPPING FUNDS AFTER YOU SEND THEM SHIPPING FUNDS THEY WILL COME UP
WITH EXCUSES FOR YOU TO TRY & SEND THEM MORE FUNDS, OR TELL YOU THAT THEY NEED MORE FUNDS TO CLEAR THE GOODS AT THE AIRPORT. THEY ARE VERY GOOD WITH MAKING THEIR DOCUMENTS LOOK VERIFIABLE DO NOT DO BUSINESS WITH THEM THEY ARE ALSO BLACKLISTED WITHIN A FEW REFINEIES WORLDWIDE AGAI STAY AWAY FROM THEM OR YOU WILL REGRET IT
***** STAY AWAY FROM THIS MAN & HIS SO CALLED COMPANY YOU HAVE BEEN WARNED *****
COMPANY # 2
STAY AWAY FROM MR. EVANS YUBOKU FROM GHANA, PRETENDS TO ALSO BE IN THE UK ( LONDON ) OR DUBAI
luca Garbato09-Nov-2012 17:39Hell? Sir,
Do you have a serious address of gold seller.
Regards
Luca
Jansson09-Nov-2012 13:44TO WHOM IT MAY CONCERN
FRAUD ELMAHROSE MINES LTD :
Faked export documents from International Maritime Logistics Mr Hans Elias Faked invoices and collecting fee from Ministry of Mines ( this is a group using Ministry of Mines name in the fraud operation ).
The Seller Elmahrose Ltd/Mr Ndo Tchana Patricka has appointed and introduced Ministry of Mine and International Maritime Logistics in this transaction.
The seller signed a SPA to deliver 20 Kg gold dore bars CIF and Ministry of Mine collected fees during 4 weeks and no Gold was delivered and this is a fraud factory of false documents.
Name
? ? ? -
Mr Ndo Tchana Patricka
Mrs Nwaa Stephanie Bille
Dr Mohamed Ahmed
Ms Dr. Oma Oma
E-MAIL ADDRESSES
? ? ? ? ? ? ? ? ? ? ? -
elmahroseltd@gmail.com
elmahroseminesltd@hotmail.com
asongd2@gmail.com
We the above Company hereby offer this product as follows
1. COMMODITY DESCRIPTION
The commodity/particulars that the Seller has offered and will supply to the Buyer are as follows:
COMMODITY : AU ( GOLD ) DUST AND BARS
FINENESS : 22+ Carats
PURITY : 96.7%
QUANTITY :xxkg AS FIRST ORDER
PRICE : $25,000usd per kg CIF
2. TRANSPORTATION DOCUMENTS
This delivery shall be accompanied by:
1. Certificate of Origin
2.Certificate Of Ownership
3.4 copies of Commercial Invoice
4.Preliminary Assay Certificate5.
5. Certificate of Non Criminal Origin
6.Certificate of Photosynatry
7.Shippers Instruction for GOLD BARS
CIF Procedures
-Seller issues FCO with CEO Passport Copy -Buyer signed and returned back to seller with a passport copy -Seller send a contract for buyers approval -Buyer signed and return back to seller .
-Seller takes update pictures of gold dore bars with the buyers name and inside the gold box on the eve before traveling with the gold dore bars and signed contract to the Freight and Export Agency and Ministry respectively -Seller deposit gold to the Freight and Export Agency Safe keeping ware house and forward the signed contract to the Ministry of mines,Industry and technological development for approval -Both parties by ministry procedures take care of the safe keeping fee of the gold dore bars in the Government Recognized Freight and Export Agency few days before the approval of the approval of the contract seller pays 75% of the fee while buyer pays 25% ( This is a new Policy introduced by the Ministry of mines, All Precious metals contracts must be approved by the ministry before any shipment proceed and the goods must be shipped by the ministry recognized freight and export agency.
They are doing so in other to protect their home Primary Industries and the buyer as well. Dated Pictures of the product carrying buyers names and address would be provided) -Ministry approved contract and forward copies to both parties -Seller pays in the shipment allocation fee, customs taxes, insurance and other necessary taxes -Export and freight agency forward all shipping documents to buyer including an airway bill -Gold dore bars shipped to buyers Destination Airport -Gold dore bars received and cleared by buyer to his refinery -Gold dust refined and Payment released Through Bank to Bank Transfer
NOTE
it is the ministry of mines that is in charge of all precious metals in Cameroon. they do the shipment through a recognized freight and export agency. they are doing so in order to protect their home primary industries and to prevent any fraud between the buyer and the seller
Advise so that we can proceed
Chief Ndo T. Patrika
Elmahrose Mines Ltd
35 Road West street
Eastern Region
Tell: +237 792 949 52
Skype:elmrhose
On behalf of my Board, I remain
Yours Faithfully
FAKED DOCUMENTS AND INVOICES
? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?
Mr.Abenelang Abessolo
Director of Mines
Ministry of Industry,Mines and Technological Development
Department of Mines and Geology.The Property Storage House
Boite Postale 1604 2nd Floor Buyamasi Building Yaounde Cameroon
Tel: 00237 22 12 73 62
Fax: 00237 22 66 22 83
Mobile: 00237 78975128
? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?
FAKED SHIPPING DOCUMENTS
Mr Elias Hans
Branch Manager
Address: B.P 341 Akwa Douala Cameroon
Tel: +237 95239758
Fax:+237 33298320
Email:infoslogistic@mail2cameroon.com
Website:
http://www.intmaritimelog.com_______________________________________________________________
If you require any further information do not hesitate to contact me.
Kind regards
Christer Jansson
Jansson09-Nov-2012 13:44TO WHOM IT MAY CONCERN
FRAUD ELMAHROSE MINES LTD :
Faked export documents from International Maritime Logistics Mr Hans Elias Faked invoices and collecting fee from Ministry of Mines ( this is a group using Ministry of Mines name in the fraud operation ).
The Seller Elmahrose Ltd/Mr Ndo Tchana Patricka has appointed and introduced Ministry of Mine and International Maritime Logistics in this transaction.
The seller signed a SPA to deliver 20 Kg gold dore bars CIF and Ministry of Mine collected fees during 4 weeks and no Gold was delivered and this is a fraud factory of false documents.
Name
? ? ? -
Mr Ndo Tchana Patricka
Mrs Nwaa Stephanie Bille
Dr Mohamed Ahmed
Ms Dr. Oma Oma
E-MAIL ADDRESSES
? ? ? ? ? ? ? ? ? ? ? -
elmahroseltd@gmail.com
elmahroseminesltd@hotmail.com
asongd2@gmail.com
We the above Company hereby offer this product as follows
1. COMMODITY DESCRIPTION
The commodity/particulars that the Seller has offered and will supply to the Buyer are as follows:
COMMODITY : AU ( GOLD ) DUST AND BARS
FINENESS : 22+ Carats
PURITY : 96.7%
QUANTITY :xxkg AS FIRST ORDER
PRICE : $25,000usd per kg CIF
2. TRANSPORTATION DOCUMENTS
This delivery shall be accompanied by:
1. Certificate of Origin
2.Certificate Of Ownership
3.4 copies of Commercial Invoice
4.Preliminary Assay Certificate5.
5. Certificate of Non Criminal Origin
6.Certificate of Photosynatry
7.Shippers Instruction for GOLD BARS
CIF Procedures
-Seller issues FCO with CEO Passport Copy -Buyer signed and returned back to seller with a passport copy -Seller send a contract for buyers approval -Buyer signed and return back to seller .
-Seller takes update pictures of gold dore bars with the buyers name and inside the gold box on the eve before traveling with the gold dore bars and signed contract to the Freight and Export Agency and Ministry respectively -Seller deposit gold to the Freight and Export Agency Safe keeping ware house and forward the signed contract to the Ministry of mines,Industry and technological development for approval -Both parties by ministry procedures take care of the safe keeping fee of the gold dore bars in the Government Recognized Freight and Export Agency few days before the approval of the approval of the contract seller pays 75% of the fee while buyer pays 25% ( This is a new Policy introduced by the Ministry of mines, All Precious metals contracts must be approved by the ministry before any shipment proceed and the goods must be shipped by the ministry recognized freight and export agency.
They are doing so in other to protect their home Primary Industries and the buyer as well. Dated Pictures of the product carrying buyers names and address would be provided) -Ministry approved contract and forward copies to both parties -Seller pays in the shipment allocation fee, customs taxes, insurance and other necessary taxes -Export and freight agency forward all shipping documents to buyer including an airway bill -Gold dore bars shipped to buyers Destination Airport -Gold dore bars received and cleared by buyer to his refinery -Gold dust refined and Payment released Through Bank to Bank Transfer
NOTE
it is the ministry of mines that is in charge of all precious metals in Cameroon. they do the shipment through a recognized freight and export agency. they are doing so in order to protect their home primary industries and to prevent any fraud between the buyer and the seller
Advise so that we can proceed
Chief Ndo T. Patrika
Elmahrose Mines Ltd
35 Road West street
Eastern Region
Tell: +237 792 949 52
Skype:elmrhose
On behalf of my Board, I remain
Yours Faithfully
FAKED DOCUMENTS AND INVOICES
? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?
Mr.Abenelang Abessolo
Director of Mines
Ministry of Industry,Mines and Technological Development
Department of Mines and Geology.The Property Storage House
Boite Postale 1604 2nd Floor Buyamasi Building Yaounde Cameroon
Tel: 00237 22 12 73 62
Fax: 00237 22 66 22 83
Mobile: 00237 78975128
? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ?
FAKED SHIPPING DOCUMENTS
Mr Elias Hans
Branch Manager
Address: B.P 341 Akwa Douala Cameroon
Tel: +237 95239758
Fax:+237 33298320
Email:infoslogistic@mail2cameroon.com
Website:
http://www.intmaritimelog.com_______________________________________________________________
If you require any further information do not hesitate to contact me.
Kind regards
Christer Jansson
Marcel08-Nov-2012 10:24Dear sir,
Is Mr Michel Amani a fake seller. What i see is only a small advertisement
and there are no comments behind his name.
Guest07-Nov-2012 18:16Beware of Brenu Joseph and Europa Pee company in Ghana ? Big liars and scammers
guest06-Nov-2012 00:51Just copying from one of the above comments and pasting it here.
I had declined to transfer funds thru western union but accepted to send
ADVANCE FEE SCAM : AFLAO METALS IS A SCAM ? Memsah Williams of Lome, Togo, is a clever thief. Beware of AFLAO METALS ADVANCE FEE FRAUD! They are listed in nearly every B2B directory, but they are scammers and phony document specialists. Report all contact with relevant authorities. Also beware of his accomplice Frank at
www.safariagencesdevoyages.com. They will try to extort Western Union / Moneygram payments out of you. Also beware of an unauthorized passport scan of Tanja Cesar, who is supposed to be their Slovak Republic gold courier. This passport was either stolen, phished from the internet, or lifted from the files of SCAM operation SAFARI AGENCES DE VOYAGES in Lome Togo. Be warned not to send advance fees to scammers Memsah Williams of Afloa Metals or Frank of Safari Agences de Voyage!
The above also happened with me. I had declined to make the payment via western union to SAFARI AGENCES DE VOYAGES but had accepted to make the payment via wire tranfer as Memsah willaim from AFLAO METALS had promised me to have the tickets issued if i just produced the copy of swift tranfer. The wire transfer was being made to SAFARI AGENCES DE VOYAGES for ticket exp. More than 2000 USD. I had requested my bank to send it via wire and also got a receipt for the same which was forwarded to them. a day later
they declined to issue the ticket saying they will only issue the ticket once the payment hit their account, ie almost 10?14 days later. At this stage even Memsah William becomes helpless and will not be able to convince SAFARI AGENCES DE VOYAGES to get the ticket issued. Since it was a day later after i had send the proof of fund tranfer, they assumed the transfer might have already taken. Luckily for me, i was able to recall the swift transfer just moments before it was transmitted. SAFARI AGENCES DE VOYAGES always maintains that they will issue the ticket only after payment hits their account. Its Memsah willaim who says that he had talked to the agency and SAFARI AGENCES DE VOYAGES will issue the ticket once they had the copy of swift.
Even if you agree to send flight ticket from LOME,TOGO to the buyers destination, Memsah willaim will guide you to SAFARI AGENCES DE VOYAGES saying that this is the ONLY agent whiach can transport gold from Lome,TOGO to airport in Accra, GHANA from where it will fly to buyers international destination.
Guest06-Nov-2012 00:50Just copying from one of the above comments and pasting it here.
I had declined to transfer funds thru western union but accepted to send
ADVANCE FEE SCAM : AFLAO METALS IS A SCAM ? Memsah Williams of Lome, Togo, is a clever thief. Beware of AFLAO METALS ADVANCE FEE FRAUD! They are listed in nearly every B2B directory, but they are scammers and phony document specialists. Report all contact with relevant authorities. Also beware of his accomplice Frank at
www.safariagencesdevoyages.com. They will try to extort Western Union / Moneygram payments out of you. Also beware of an unauthorized passport scan of Tanja Cesar, who is supposed to be their Slovak Republic gold courier. This passport was either stolen, phished from the internet, or lifted from the files of SCAM operation SAFARI AGENCES DE VOYAGES in Lome Togo. Be warned not to send advance fees to scammers Memsah Williams of Afloa Metals or Frank of Safari Agences de Voyage!
The above also happened with me. I had declined to make the payment via western union to SAFARI AGENCES DE VOYAGES but had accepted to make the payment via wire tranfer as Memsah willaim from AFLAO METALS had promised me to have the tickets issued if i just produced the copy of swift tranfer. The wire transfer was being made to SAFARI AGENCES DE VOYAGES for ticket exp. More than 2000 USD. I had requested my bank to send it via wire and also got a receipt for the same which was forwarded to them. a day later
they declined to issue the ticket saying they will only issue the ticket once the payment hit their account, ie almost 10?14 days later. At this stage even Memsah William becomes helpless and will not be able to convince SAFARI AGENCES DE VOYAGES to get the ticket issued. Since it was a day later after i had send the proof of fund tranfer, they assumed the transfer might have already taken. Luckily for me, i was able to recall the swift transfer just moments before it was transmitted. SAFARI AGENCES DE VOYAGES always maintains that they will issue the ticket only after payment hits their account. Its Memsah willaim who says that he had talked to the agency and SAFARI AGENCES DE VOYAGES will issue the ticket once they had the copy of swift.
Even if you agree to send flight ticket from LOME,TOGO to the buyers destination, Memsah willaim will guide you to SAFARI AGENCES DE VOYAGES saying that this is the ONLY agent whiach can transport gold from Lome,TOGO to airport in Accra, GHANA from where it will fly to buyers international destination.
Guest06-Nov-2012 00:50Just copying from one of the above comments and pasting it here.
I had declined to transfer funds thru western union but accepted to send
ADVANCE FEE SCAM : AFLAO METALS IS A SCAM ? Memsah Williams of Lome, Togo, is a clever thief. Beware of AFLAO METALS ADVANCE FEE FRAUD! They are listed in nearly every B2B directory, but they are scammers and phony document specialists. Report all contact with relevant authorities. Also beware of his accomplice Frank at
www.safariagencesdevoyages.com. They will try to extort Western Union / Moneygram payments out of you. Also beware of an unauthorized passport scan of Tanja Cesar, who is supposed to be their Slovak Republic gold courier. This passport was either stolen, phished from the internet, or lifted from the files of SCAM operation SAFARI AGENCES DE VOYAGES in Lome Togo. Be warned not to send advance fees to scammers Memsah Williams of Afloa Metals or Frank of Safari Agences de Voyage!
The above also happened with me. I had declined to make the payment via western union to SAFARI AGENCES DE VOYAGES but had accepted to make the payment via wire tranfer as Memsah willaim from AFLAO METALS had promised me to have the tickets issued if i just produced the copy of swift tranfer. The wire transfer was being made to SAFARI AGENCES DE VOYAGES for ticket exp. More than 2000 USD. I had requested my bank to send it via wire and also got a receipt for the same which was forwarded to them. a day later
they declined to issue the ticket saying they will only issue the ticket once the payment hit their account, ie almost 10?14 days later. At this stage even Memsah William becomes helpless and will not be able to convince SAFARI AGENCES DE VOYAGES to get the ticket issued. Since it was a day later after i had send the proof of fund tranfer, they assumed the transfer might have already taken. Luckily for me, i was able to recall the swift transfer just moments before it was transmitted. SAFARI AGENCES DE VOYAGES always maintains that they will issue the ticket only after payment hits their account. Its Memsah willaim who says that he had talked to the agency and SAFARI AGENCES DE VOYAGES will issue the ticket once they had the copy of swift.
Even if you agree to send flight ticket from LOME,TOGO to the buyers destination, Memsah willaim will guide you to SAFARI AGENCES DE VOYAGES saying that this is the ONLY agent whiach can transport gold from Lome,TOGO to airport in Accra, GHANA from where it will fly to buyers international destination.
james morange05-Nov-2012 20:06i friend was given 7kg of gold from the chief of the orphage she work at and no doc and he says he dosnt have on is this poss because she cant sell it without doc
james morange05-Nov-2012 20:06i friend was given 7kg of gold from the chief of the orphage she work at and no doc and he says he dosnt have on is this poss because she cant sell it without doc
james morange05-Nov-2012 20:06i friend was given 7kg of gold from the chief of the orphage she work at and no doc and he says he dosnt have on is this poss because she cant sell it without doc
james morange05-Nov-2012 20:04i friend was given 7kg of gold from the chief of the orphage she work at and no doc and he says he dosnt have on is this poss because she cant sell it without doc
james morange05-Nov-2012 20:04i friend was given 7kg of gold from the chief of the orphage she work at and no doc and he says he dosnt have on is this poss because she cant sell it without doc
james morange05-Nov-2012 20:04i friend was given 7kg of gold from the chief of the orphage she work at and no doc and he says he dosnt have on is this poss because she cant sell it without doc
james morange05-Nov-2012 20:04i friend was given 7kg of gold from the chief of the orphage she work at and no doc and he says he dosnt have on is this poss because she cant sell it without doc
james morange05-Nov-2012 20:04i friend was given 7kg of gold from the chief of the orphage she work at and no doc and he says he dosnt have on is this poss because she cant sell it without doc
TAPAN MUKHERJEE03-Nov-2012 07:17RECEIVED A MAIL FROM EL SHEIKH IBRAHIM A LIBYAN CITIZEN LIVING IN REPUBLIC DU BENIN.HE ASKED
ME TO HELP SELL 750 KG OF GOLD BAR/GOLD DUST.
majapahit31-Oct-2012 18:49Email : laksmihadi@gmail.com
majapahit31-Oct-2012 18:47Send email to me about Mali gold sellers
Guest31-Oct-2012 13:01ADVANCE FEE SCAM : AFLAO METALS IS A SCAM ? Memsah Williams of Lome, Togo, is a clever thief. Beware of AFLAO METALS ADVANCE FEE FRAUD! They are listed in nearly every B2B directory, but they are scammers and phony document specialists. Report all contact with relevant authorities. Also beware of his accomplice Frank at
www.safariagencesdevoyages.com. They will try to extort Western Union / Moneygram payments out of you. Also beware of an unauthorized passport scan of Tanja Cesar, who is supposed to be their Slovak Republic gold courier. This passport was either stolen, phished from the internet, or lifted from the files of SCAM operation SAFARI AGENCES DE VOYAGES in Lome Togo. Be warned not to send advance fees to scammers Memsah Williams of Afloa Metals or Frank of Safari Agences de Voyage!
Joseph A26-Oct-2012 12:46For Gold buyers and Diamonds, we have in Stock large quantities of gold and diamonds now in Accra, If you are a serious buyer please kindly contact me for serious bussiness, NO TIME TO WASTE. We work mainly on FOB basis, but might consider CIF if the conditions are good.
EMAIL: nkanetetegold2011@gmail.com
Sam26-Oct-2012 00:02Tasuma Village Miners 223?65?236399
Rue 714 Para Jikoron I Port 3325 Seminikoni Bamako Mali
Oumer Fofona, Oumer Fafona Assn?t Director
oumerfofona2012@gmail.com
oumerfofona2012@yahoo.com
223?70?399249
Passport # B0333221
Modibe Keita 223?75056724
ModibeKeita2012@yahoo.com
Tasuma Village Miners
Kalana Village Miners
Sedjiola In Kayes Mali
Kenjiba Village Miners
Guest23-Oct-2012 20:57Beware of Orisi Vukinavanua.
He?s the most horrible time waster on Earth
He claims to have gold, he has NOTHING.
big fat liar.
Guest22-Oct-2012 09:05Mr Abullahi Coulibaly
Passport Number: A1461808
physical address at Porte 14 Hippodrom, Rue 10 Bamako Mali West Africa.
he switch phones a lot in order not to be tracked down with his 419 Scams. He stole $500 from me asking me to send the funds to Western Union, and in return will send me 5 kgs as test trial.
Company name: Traore Gold/Diamonds Trade
Company Director: Mr. Traore Ousmane
Company address: Lambangne Rue Porte 78 Conakry, Guinee Conakry.West Africa, Guinea 0224
Phone# 223?22372810228
he will tell you he wants this money for the elders who control the gold in his village. He is a crooked and not to be trusted, he will ask you to send money than he will ship out gold, but than you send it, he will ask to send more money for some declaration papers before he can ship the gold to you. Stay far away from this crook he is very dangerous.
Guest22-Oct-2012 09:00Everyone be warned that Gold Trading Sarl, the name they go by now Royal Gold Sarl in Benin are running a very sophisticated gold trading scam. website address:
www.royalgoldsarl.com, I have been scammed $545.00 last week and was told per Mr.Sacko Mahamadou passport # B0447659 it might not even be a good passport # perhaps something he made up.
Mr. Sacko asked to send him $545 by western Union and will ship me 5 kgs of gold bars as a test trial. Little do I know I was getting scam once I send him the funds. There are using a fake shipping company called Eco Courier?and there are a large group running that scam.
Danielles19-Oct-2012 14:01Hello Sir?s, please did any anybody here know about this Company? are they real or Scam?
MAGBRUKA, KONO, BO MINERS ASSOCITION
74 main motor road Freetown, Sierra Leone Tel: +232?78?68?16?32
Email goldminers15@yahoo.com http//www.magbrukaminers.com
Daniells19-Oct-2012 13:51GOOD DAY SIR?S PLEASE CAN SOMEBODY TELL ABOUT THIS GOLD SELLER BELOW ??? HE ASKED ME TO TRAVEL DOWN TO BENIN REPUBLIC.
BAKARI FAMILY GOLD
Tel : +229 96623429
Email: goldsfamily2010@gmail.com
Also if buyer can?t come down or send his Rep, let them contact the Family Trusted shipping company ( Brinks-Co Express Couriers Limited.
www.brinkscoexpress.int.tc ) OR Through Diplomatic Agent Shipper/ Send seller fright Money to come with some first shipment.Mr.Robert Bakari FOR THE FAMILY M-D.
Melvin A19-Oct-2012 02:08Beware of Mali gold sellers not truthful. Contact me for more details, I have been to Mali on two occassions. Email: m_akridge@aol.com
William burt18-Oct-2012 23:49Sorry it was w.a.p. Info@wapmida.com. Any info on them please thank you
William burt18-Oct-2012 23:24Is any one herd of w.a.m.p. email is info@wampmida.com
William burt18-Oct-2012 22:33Any hear of group mines
William burt18-Oct-2012 21:25Has anyone herd of dr Alfa at metal augold in Mali
He asking me to come to his mine to inspect and get sample
Please can any one help me . Or direct me to a real Africa gold seller
Guest17-Oct-2012 11:43Please be aware of doing business in Tanzania, 99,99% you will be scammed and the crooks get help from madini, TRA, central police and customs police as well as from high ranking persons. just check the tanzanian fraudwatcher
Lucien Sonard17-Oct-2012 08:05Dear Madam / Sir;
We are looking to buy gold for our buyers in Dubai. So we contacted a ?seller?) from Mali who names Ahmed babou ( CITY KING- SARL IMPORT ? EXPORT MALI,
A company incorporated in and under the laws of MALI,
LICENSE N?: MA BKO 2011 B4347
Address At: Rue 223, Port 102/ Bamako , ACI 2000 Hamdallaye
TEL: (+223) 60001208,
Represented By: AHMED BABOU
Possport N?: A1443514
E-mail: ahmedbabou69@yahoo.com ) wowuld like to help us to erify if the company and person are real & trusted.
Best Regards
Lucien Sonard
Guest13-Oct-2012 08:34Beware of Gold Trading Sarl in Benin, they are running a sophisticated gold trading scam.
GOLD TRADING SARL
C/222 SIKECODJI
COTONOU REPUBLIC OF BENIN
DIRECTOR: KAFADNAM HAMIDOU.
EMAIL: GOLDBROKERSARL@YAHOO.FR
ONLYKAFADNAM@GMAIL.COM
PHONE: +229 97464567
+229 97441675
WORKING WITH FAKE COURIER CALLED ECO INTL COURIER SERVICE.
Togo Branch: ECO INT?L COURIER SERVICE 255 Emule La-Pass Lome- Togo Tel/Fax: +228 64 03 98 / 228640398 E-mail: togo@ecointcservice.com Ghana Branch: ECO INT?L COURIER SERVICE 3 Tete kwashi Circle Accra -Ghana Tel/Fax: +233 248 879 789 / 233248879789 E-mail: ghana@ecointcservice.com
Peet Booysen10-Oct-2012 18:18Please advise on the legitimacy of gold offered by Chief Ibrahim who claims to be the spokesperson for His Royal Majesty, Nana Osombour 2. His address is his.royal.majesty.nana.osombourii@gmail.com who offered me 50 kgs gold at $45 000 per kg.
Guest09-Oct-2012 09:42Please be aware of Mr Paul Sesay Norman Freetown Sierra Leone Gold scam You pay shipping but shipment gets waylaid and they keep asking for money to help it complete its journey to your destination . Itnever arrives His Number23278802087. He is doing this In conjunction With Sierra Group Express ,Charles Banjura Manager Freetown , your shipment cannot be properly traced at any time and no information will be provided . Do not believe or tust these two men at any time they are professinels in taking your money . Sierra group express has internet site , dont trust them 23277336571 all phones are mobiles .
Roger Taylor08-Oct-2012 18:26Hello,
Genuine buyer looking for a reliable gold miner, kindly contact me for more details
of my supplier, if he has no product for you he can also link you up to one of their mining partners.
Roger Taylor
Email: rojertaylor@aol.com
tango08-Oct-2012 12:52careful Roger, very careful???.
Roger Taylor08-Oct-2012 12:03Hello,
Genuine buyer looking for a reliable gold miner, kindly contact me for more details
of my supplier, if he has no product for you he can also link you up to one of their mining partners.
Roger Taylor
Email: rojertaylor@aol.com
Roger Taylor08-Oct-2012 09:35Hello,
Genuine buyer looking for a reliable gold miner, kindly contact me for more details
of my supplier, if he has no product for you he can also link you up to one of their mining partners.
Roger Taylor
Email: rojertaylor@aol.com
Noel A.M06-Oct-2012 07:39STAY AWAY FROM THIS GROUP OF SCAMMERS:
REAL GOLD VENTURES
ACCRA, GHANA.
Mr. Steve Mensah
+233540829999
Project Manager
Email: thomgold55#gmail.com
STAN GOLD LIMITED
NO 90 0XFORD STREET
ACCRA GHANA.
+233542407468
Mr Williams A George.
Email: stangoldghltd@aol.com
Skype:stangoldghltd1.
Raymond Collins
Chairman and Ceo
Favor Miners Inc.
www.favourminers.com
Email: purchase@favourminers.com
Thanks,
Noel Megumichan A
Email: noelmegumichan@yahoo.com
Guest05-Oct-2012 18:56BEWARE OF THIS SCAMMER:
Mr Ali Ahmed Passport number H 2415134 EMAIL ADDRESS alight202@yahoo.com ph# : +233?24?15581 Ghana and his secretary Ms Caroline Richards ID number H 2165535 Address H-HCG 121 Niiboi Town Accra Ghana. ALI Ahmed Richard and his wife Caroline Richard both are very good at what they do- he goes by Ali Ahmed only on all his transactions. He try to make people believe he is a Christian and would pretend he is a true friend, he will work on your trust for as long as it takes to gain a friendship relationship, and can assist you with other sellers for you not fall into trap, and you can trust him but bottom line is he is a crook, he tries to find the opportunity to take funds from you. He stole a lot of money from innocent people by asking them to send them money by western Union under is wife name Caroline Richard. He is a fake seller he has no gold ? a bum on the street live a criminal life, he very soft spoken most of the time he is very hard to understand. Be VERY CAREFUL HE IS THE HEAD CRIMINAL IN GHANA PRAYING ON INNOCENT BUYERS?BEWARE DO NOT DO BUSINESS WITH HIM?HE WILL EVEN MAKE YOU BELIEVE EVERYTHING PEOPLE ARE SAYING ABOUT HIM IS NOT TRUE?WHICH HE MADE ME BELIEVE NOBODY CAN STOP HIM, HE WILL CONTINUE PRAYING ON PEOPLE AND SAM PEOPLE FOR AS LONG PEOPLE WANTS TO BUY GOLD.
Guest05-Oct-2012 09:07Tanzania Scammer: known as Jimmy James Skype ID: jimmy.james30 pretends to have gold.
Works from Dar es Salaam, Tanzania.
Uses various companies: BUTEZI TRADING, phone number: +255714404025
tango02-Oct-2012 18:25DORIAN, NOT ADVANCE MONEY???.
dorian01-Oct-2012 21:36hello, does somebody here know this company: G.V.O.B
GROUPEMENT VILLAGEOIS DES ORPAILLEURS DE BOUDA
08BP 12243 OUAGA 08 COMPTE N 0113022400 CORIS BANK
Guest01-Oct-2012 18:32Eugne Nana Korankye of Spiodikal Company Ltd. in Ghana is 100% fake gold seller and scammer. His phone number is +233?543?567?277. His fake team members are Kwame Korankye, Alexander Korankye (Builders Accessories Ltd., George Sweeney Joseph (Akuafo Gold Mining Company Ltd.), and Benjamin Issac. They took over U$30,000 from us but they didn?t send any gold for the last 11 months.
Edward Eui Yull Hwang
tango30-Sep-2012 07:43Hello ?scamposter?, now no longer have to wonder about anything, in West Africa is the most scam in gold, unfortunately this is a reality. The only thing you can do is to open the western people, and spread alarm as much as possible. But the scam link very greed of the victims for this reason are cheated. My job is to recover the money by hook or bad manner by crook or just tracked down the gangs of crooks. But when I do an interview with the client cheated to get information, I realize how stupid the people who were victims of the scam. If there are scammers is because often there are people who take the bait easily, this is the problem. AFRIK.EURO.COMPANY.LTD
OUMER FOFONA -
DO SOMETHING ABOUT THIS CRIMINAL SCAMMER !!!
READ THE WHOLE STORY AND SEE THE EFFORTS THEY GO !!!
Kalana, Tasuma Yatela websites listing on fraudreporters as they ARE FAKE COME FROM CANADIAN
EAST COAST WEB SITE WORD FOR WORD !!!!
DO SOMETHING ABOUT THIS CRIMINAL STREET BROKER !!! RAT !!!
He is listed with the ad below on every site B2B FAKE B/S- DOCS !!!
He is listed with the ads below on every site B2B
We are here to advertise our main product alluvia gold dust as we are capable to produce up to 50kg weekly and 200kg monthly
for our potential buyers.Our company are here in Mali and we are ready to supply to any potential gold buyers from around the
world at a very reasonable price below the international gold rate and we are also capable to provide the best service and security
to our customers.
Following is the information?s of our product and we strictly transact on FOB basis. SOME SITES CIF ? ha ha for a price of your
life non performer
Price??$27.500 per kg some sites as low as 20,000 as of now 38,000
Quality?. 22karat plus
Commodity? Alluvial Gold Dust
Purity?? 93.5% Better some site 92.5
Quantity Available Now? 150kg currently claims of OUR 250 kgs !!!
Origin?..Mali
Delivering: Within 72Hours after all the necessary export documents
issued to the buyer or buyers representative and the product will be accompanied by two of our workers to the buyers country
of destination.
Assay reports provided by Laboratories, Mali, NMG. Our Company is in possession of the Gold Export Certificate issued by the
Government of the Republic of Mali. SCAMMED DOCUMENTS !!!
We can provide service to any part of the world. ( NO THEY CAN NOT )
We are prepared to offer the quantity of gold required to the Buyer or
their representative.
Best regards,
Oumer Fofana
Chief Agent , kayes gold miners association
Skype.Oumer6
Telephone +22366314099 ( ONE OF MANY )
Email.oumerfofana@yahoo.com ( ONE OF MANY EMAILS )
Another very heavily listed AD on many B2B sites !!
We are here to advertise our main product alluvia gold dust as
we are capable to produce up to 50kg weekly and 200kg monthly for our potential buyers.
Our company are here in Mali and we are ready to supply to any potential gold buyers from around the world at a very
reasonable price below the international gold rate and we are also capable to provide the best service and security to
our customers.Following is the information?s of our product and we strictly transact on FOB basis.
Price??$20.500 per kg
Quality?. 22karat plus
Commodity? Alluvial Gold Dust
Purity?? 93.5% Better
Quantity Available Now? 50kg
Origin?..Mali
Delivering: Within 72Hours after all the necessary export documents
issued to the buyer or buyers representative and the product will be accompanied by two of our workers to the buyers
country of destination.
Assay reports provided by Laboratories, Mali,Our Company is in possession of the Gold Export Certificate issued by the
Government of the Republic of Mali. We can provide service to any part of the world. We are prepared to offer the quantity
of gold required to the Buyer or their representative.
Best regards,
Oumer Fofana PASSPORT NUMBER B0333221
Chief Agent , kayes gold miners association
Skype.Oumer6
Telephone +22366314099
Email.oumerfofana2012@gmail.com
REPRESENTATIVES
1-Mrs.Sissoko Fatou fatoumata/ Passport Number: 03RC68268
2-Mr.Mangane Kissima / ?Passport Number: D9005463
Dear Friend ? ? ? ? ? ? N E X T V I C T I M
We are here to advertise our main product alluvial gold dust as We are capable to produce up to 50kg weekly and 200kg
monthly for our potential buyers. Our company is here in Mali and we are ready to supply to any potential gold buyers from
around the world at a very reasonable price below the international gold rate and we are also capable to provide the best
service and security to our customers.
Following is the informations of our product and we strictly transact on FOB basis.
Price&& $31000 per kg
Quality&. 22karat plus
Commodity& Alluvial Gold Dust
Purity&& 92.5% Better
Quantity Available Now& 215kg
Origin&.. Mali
Delivering: Within 72Hours after all the necessary export documents Issued to the buyer or buyers representative, and the
product will be accompanied by Two of our workers to the buyers country of destination. Assay reports provided by Laboratories,
DNG Mali. We can provide service to any part of the world We are prepared to offer the quantity of gold required by the Buyer.
Kindly view our website bellow and please first contact me to confirm your interest before you communicate with the mining
company because I am a registered agent to this mining company so always communicate with me so that i will facilitate the
transaction between you and the mining company.
Best regards,
Mr Hassan Oumer
Passport # Mali Commercial Agent B0333221
Chief Agent
Mali West African
Mobile +22364428388
skype : oumer6
223?652?81565
223?703?99249 +++ most recent 2012
223?644?28388
223?600?56880
223?663?14099
223 079?4408
223?648?88210
223?652?36399
223?7142?20753
OUMER- FOFONA, KONARIT,HASSEN,MAMADO,LOOKMAN, AHMED
Alpha Oumer Konare, Tenaji Konari,
Phonetic spelling of past MALIAN PRESIDENTS !!!
Claims of Stock keeping, keeper, Manager, Assnt. Director, Director, Owner
Legal Rep CEO
Metalsplace, Topix, Tradekey,Agriscape
Known EMAIL ADDRESSES
oumerfofona@hotmail.com
oumerfofona@yahoo.com
oumerfofona2012@yahoo.com
oumerfofona2012@gmail.com
mamdououmer@hotmail.com
mamadoumer@yahoo.com.ph
mr.hassen.oumer@yahoo.com
mr.hassenoumer@yahoo.com
mr.konaaritoumer@yahoo.com
mr.konaritoumer@hotmail.com
goldminers@consultant.com
ALL WEBSITES SAME SKYPE !!!
skypeumer6 all sites !!!!
LinkedIn Fofona, Fofana
metalsandsteel.com #3458
Tradekey, Ecplaza, Agriscape,Metalsplace,Ten Yellow Pages yp.theemeriatesnetwork.com
CLAIMS TO BE ASSOCIATED WITH ALL THESE MINES AS A RAT !!!
Tasuma Village Miners ? tasumavillagegoldmine@rediffmail.com
tasuma-gold.jigsy.com
DO SOMETHING ABOUT THIS CRIMINAL
He is listed with the ad below on every site B2B
Kenjiba Community Gold
Kayes and Bougini Community
Tabako Village Miner
Iberi Gold Mining and trading
Tasuma Village Gold Mine 223?62263152, 223?523?36399,660?74389
Iberi Gold Mining Trading Company
Sobodala
Sadiola Mining Village
Sanjiba
Yalea
Segala
Yatela
Dallas Group Express HiSupplier.com
Kayes and Bougini
Yacubu Balla Gold Mine
Kayes Gold Mines Association
Kalana Gold Miners
Senou Elders in Mali
SCAM LISTING SITES
Scammers.com Pbase, Scamwarners,419.Baiter,Fraudsters.org
P.Base same as listed on Scamwarners:Baiter base, Scamtacular
mr.konaritoumer@yahoo.com
mr.konaritoumer@hotmail.com
Keita Modibe, Director Passport # B0234096 modibekeita21012@yahoo.com
223?75?56724 (Past President Name)
Zemilla Boubacar Cisse Western Union Fraud
Jimmy James Emmanuel Western Union Fraud
Tony
Faye Abdulaye Atty, SOGOTRAD SARL BAMAKO MALI FAKE DOCUMENTS
ADVANCE FEE SCAMMER NAD NON PERFORMANCE !!!
SogoTrad Sarl : info.sogotradsarl_mali@yahoo.commalisogotrad.sa@yahoo.com
SogoTrad Sarl : info.sogotradsarl_mali@yahoo.com
La Poste Courier Service (FAKE DOCS ) Kon Laroche was going to smuggle
the gold out in boxes !!! parisagency@consultant.com
223?645?77308
SEE ALL OTHERS POSTINGS BOTH ON THE WEB AND THIS SITE
centenial29-Sep-2012 22:21Ali Ahmed ? Ali?s Mining Group Limited located in Accra, address Ghana ? 21, Industral area. accra Ghana accra accra 21233 Ghana ? 233?24?5115581 ? fake gold seller ? will make beleive that he is good seller, and can do large quantity of gold ? he has no expport license to do so.
Nick Harvey29-Sep-2012 16:41Hi, im a gold miner and Diamond buyer in Ghana,, ive been here 5 years,, and please all listen to what i have to say,, and you will get to spend your own money,,,,
There is no cheap gold,, gold anywhere in the world is a convertable,, its as good as cash,, there are gold buyers in all the small villages ,, there are 10 refineries in and around Accra who will pay cash for any real gold taken to them and pay 1.5% under LME , at assay, ,, it just doesnt happen so why im hell would these guys sell you a dollar for 60c,, they may be black,, but they sure aint stupid,,,,,
These guys job,, 24hrs a day is to relieve you of your money,, they have no morals,, will tell any lies they have to,, to get even $20 from you.
There is some small amounts of gold here for sale at 1.5% under LME at assay,,,but this is in the bush at the small scale mines,,and it is not commercially viable to drive around Ghana with a heap of cash trying to buy it.
I was here 5 years ago ,, and within one week i lost $120,000.00,,, I GOT CONNED BY A WHITE BRIT AND HIS 3 GHANIAAN PARTNERS,,Now ,, the Police here wont do anything,,,they will ask you to pay them to arrest the scammers,, and then go to them and get money from them,,not to arrest them,,,This place is totally corrupt,, And if you complain too much,, you get thrown out of the country.
Their names are as follows:
Martin Avent ( Brit) now i think in Mali doing the same.
Peter Thompson ( was a investment advisor with the Brittish High Commission) untill sacked.
Patrick Banfo,, Ghanaaian,, with UK passport
Max Lanyoh( Mansro Lanyoh),,,
Uncle Fi
If you want gold,,, invest some money in a real mine,, with real bona fide,,, because you will waste your time and money trying to buy it.
Cheers
Nick Harvey
tango28-Sep-2012 13:50In Ghana and West Africa Legal action is not needed, the only solution is to isolate these people by putting them in a black list, and if you have defrauded money, send a team to the forced recovery, there are no other solutions. AFRIK.EURO.COMPANY.LTD
Dirandra Makanjee28-Sep-2012 13:23Amorsac Mining Company Ltd.,
BOX 1515 TARKWA, ACCRA, BLOCK 110, ACCRA, NEWTOWN, GHANA.
Mr. David Akwasi Nimoh
Telephone : +233 271 959 000
Emails : docariste2008@yahoo.com OR akwasinimoh2012@gmail.com OR akwasinimoh@yahoo.com
Passport No : H1243528
Real Scammer. He get?s a financial instrument first. If he can?t advance money from that, he says the financial instrument is useless even afert signing the Draft verbiage of the financial instrument.
Don?t get caught. He doesn?t have gold. He only want the financial instrument to encash it. You won?t receive any gold. He and his company should be blacklisted in Ghana and should take legal action against cuprits like this
Guest27-Sep-2012 16:23given below company also scammer, plz entertain this company
General Fdiled Mining Company Ltd, Ghana
Signore Metals PVT Ltd, India, UK, ghana
david Blount-Porter25-Sep-2012 18:48In my experience Mr Alpha Bendor Sylla takes your money and doesn?t deliver. He send me 10g sample. I paid him for it and then sent him money two more times (silly me). He promised much and delivered nothing. Tried to scam us for $16,000 but it didn?t work.
david Blount-Porter25-Sep-2012 18:41In my experience Mr Alpha Bendor Sylla takes your money and doesn?t deliver. He send me 10g sample. I paid him for it and then sent him money two more times (silly me). He promised much and delivered nothing. Tried to scam us for $16,000 but it didn?t work.
Guest21-Sep-2012 13:05Has anybody dealt with Mr Kojo Newman of Liberty Mining in Accra Ghana?
Berndt Roenning21-Sep-2012 12:27Dear Sirs, my name is Berndt Roenning from Finland and I want to know if your company has an agent in Amsterdam by the name of Sir K. Baafo, who handel shipments from Ghana to Europe and vice versa. I got a mail from him that I have got 50 kg gold bars from Ghana last friday, sender Berndt Roenning and Humu Adam, to Berndt roenning Finland. Have you sent any gold last thursday a week ago to Amsterdam?
Kindly,
Berndt
justine19-Sep-2012 15:34We have had contact with an Australian company called RHB Group PTY fronted by two criminals in Jan Michel van Kapel and Rhonda Bowden. Beware these people they are known gold scammers and have been getting genuine buyers to post instruments to their trust accounts when they have NO gold and are trying to borrow against these financial instruments. Also we have reports they have stolen money from an unsuspecting buyer from the US. There are other reports from Dubai that they have tried to scam some royals there. Spread the word about these scammers, name and shame them so they can not rip off anymore people!!!!!
These people are true scammers, I know many people they have tried to scam. They send out contracts after contracts agressively pressing buyers to post money or instruments to their own accounts but they have no gold. Stay clear of these people!!!!
Mr J Michel van Kapel & Rhonda H Bowden
RHB Group PTY Ltd
PO Box 560,
Kippa-Ring QLD 4021,
AUSTRALIA
Phone: + 61 7 3204 1809
Fax: + 61 7 3204 8544
Roger Taylor17-Sep-2012 20:21Hello,
Genuine buyer looking for a reliable gold miner, kindly contact me for more details
of my supplier, if he has no product for you he can also link you up to one of their mining partners.
Roger Taylor
Email: rojertaylor@aol.com
Ricco Juregen17-Sep-2012 16:33Beware of KELVIN OPOKU OF ASHANTI KINGS MINES with his so claimed sister company. Mr. Opoku and his so called has no gold, no company but has all the fake documents to scam innocent. He is working with a lot of scammers in Ghana and has scammmed to the amount of $7500. Please anyone who know his where about should report to nearest police for a ramsome
reward.
Please all must beware.
Guest17-Sep-2012 13:57Be aware of Cooperative Miniere Dekisenge, their ?headquarters? they claim is B.P 342, Kolowezi, Katanga ? DRC. This company is not registered with the ministry of mines in Congo, they are operating illegally and trying to sell ?gold? in Lusaka,Zambia.They expect buyers to pay for the TTI costs and pay for their Operations Director ? Samar Kambale Hussein? to fly with the gold to the destination. But they won?t show you all the documents, and their agent in Lusaka ? Mette Chishimba from Guardian Cargo Ltd or Suleen Investments in Lusaka,Zambia, he is also part of this scam. The CEO or Director for Cooperative Miniere Dekisenge is Zagabe Kimputu, and his secretary ? Jean Marie Kapenda. DO NOT DEAL WITH Emmanual Kazali and Samar Kabale they are all Congolese and big time scammers operating out of Zambia. They do not have gold!! copmindekisenge@gmail.com, samar.husseink@gmail.com, emmakazali@yahoo.com
William Mautner12-Sep-2012 19:50Dear sphill0562 contact us directly through ceo@internationalfacilitationgroupinc.com for more details on how to conduct due deligence on any company you intend to deal with.I have dealt with ESI Miami under Thierry Boinnard but so many people use the company name and other security companies like G4s to conduct fraudulent activities..
CEO.INTERNATIONAL FACILITATION GROUP INC.NEWBERG OREGON.
Email. ceo@internationalfacilitationgroupinc.com.
Guest12-Sep-2012 05:41Is anyone aware of Quantum csld investers
darrell kennedy11-Sep-2012 00:20i want to know if a lady by the name of kojo nunno is a scamer and she is useing a atterny named robert safo are goes by the name of robert sarfo
sphill056209-Sep-2012 01:22A company called Franko Mines Company Limited No 17th Harbor road Accra-Ghana West Africa represented by Jimmy Lawal for Raymond Dogbe Marketing Director with a mandate from Gideon Kweikuma Quaye of High Court of Ghana have stated they call sell gold bouillon and gold alluvial gold concentrate. They use ESI security to transport the gold. Has anyone heard of this company or these people? Any advise would be greatly appreciated.
Guest03-Sep-2012 06:32ALMA OFARI ? METALS PLACE- EZPLAZA- TRADEKEY- AGRIBIZ- MANY B2B ?SS ALL SCAMMING WATCH OUT !!!MICHAEL OFARI METALSPLACE SCAMMER !!!!NAME CHANGES AND COMPANY NAME CHANGES ?
Guest03-Sep-2012 06:32ALMA OFARI ? METALS PLACE- EZPLAZA- TRADEKEY- AGRIBIZ- MANY B2B ?SS ALL SCAMMING WATCH OUT !!!MICHAEL OFARI METALSPLACE SCAMMER !!!!NAME CHANGES AND COMPANY NAME CHANGES ?
Guest03-Sep-2012 06:30ALMA OLIFARI-OLD MAN ? SENDS PASSPORT AND FAKE DOCS !!! MICHAEL OLIFAI FRANCE RELATIVE? 223265275585 GHANA GOLD SCAMMER- NU LIFE CO- EXMART MARKETING AND TRADING CO LTD. ACCRA GHANA-ERSIME MINING COMPANY- COTTON T-SHIRTS SALES FAKE GHANA GOVERNMENT CONTRACTS-
MANY LISTINGS OF SCAMMING- MANY EMAILS AND PHONE NUMBERS !! DIPLOMATE KWAME HARRISON SCAMMER ? NEW YORK CITY SCAMMER 646?543?8722, 917?503?9851, 233?209089921 NOT A DIPLOMAT GHANA EMBASSY HELPS THESE SCAMMERS-WANTED 18,000 AT THE 11TH HOUR TO DELIVER ALL LIES SCAMMING !!!!
Guest03-Sep-2012 06:16HE sought you out on dating website? seriously?are you crazy?you are reading a live writing?a in life book?a novel?!!!! A LIE. ARE SERIOUSLY SO EMPTY THAT YOU WOULD EVEN TAKE THAT IN?.desperate people do desperate things by desperate decsions,
get involved with real life situations and stop waisting your thoughts on a story !!!!
Ken02-Sep-2012 17:32Jane,
Sounds like Michael CArter, ask him if he is also known as Michael Carter. this guy did the same thing with a lady I know. if he is the same, then he is a scammer??
Jane Dumont31-Aug-2012 19:40I have been contacted by a person who calls himself Denis Mcloughlin supposedly from Quebec City Canada who is on a business trip in Accra, Ghana to purchase gold. He has had phone contact from this phone number: 1?324?365?3559. He sought me out on a dating site.
Jane Dumont31-Aug-2012 19:39I have been contacted by a person who calls himself Denis Mcloughlin supposedly from Quebec City Canada who is on a business trip in Accra, Ghana to purchase gold. He has had phone contact from this phone number: 1?324?365?3559. He sought me out on a dating site.
Guest28-Aug-2012 06:35real buyer in china.wanna have cooperate.contact junlongwu@163.com
Guest27-Aug-2012 20:37Only do CIF your country and no upfront money and POP is with the assay. All real buyers
know the shitck !!! Don?t get caught up with the possibilty proooof is prooof at assay
and real gold sellers do not give any rhetoric. Scammers try everything?from phone and hang up to have you call back to screaming for this and that, if and only if then and
then the future?.so POP is after clearance at any customs and assay at the refinery or private assayers!! If you choose to play you pay and they hope you do !!!
Guest27-Aug-2012 20:29Akin Musa Dembele representing DOGOKO ? DOGOGO Miners scammer.Dogogo Miners reconnected but non performance and back peddling about scenario !2012
lev.oleg@bk.ru25-Aug-2012 23:18Hello, am Oleg from Moscow, Hassan is a good seller of gold and he supplies us gold here in Moscow. MOnthly basis. If you re buying gold buy from Hassan.
Mine email: lev.oleg@bk.ru
Thanks,
Oleg
lev.oleg@bk.ru25-Aug-2012 23:17Nice site for gold buyers and Investors, Thank you Sir for the help you offered to us while in your country, keep on being positive my friend.
Thanks,
Oleg
Ken25-Aug-2012 17:41anyone know a Michael Carter who is doing business in Accra, Ghana. his e-mail is michaelcarter237@yahoo.com, phone number 354?314?6871. he says that he is Ghana and can?t get the gold out unless he gets $11,800.00.
I beleive he is a scammer and may use other names when scamming people. I have not nor will sned him the money
Guest23-Aug-2012 10:55hello if you have been scammed in tanzania then give me your contacts and i will lead you to the people that scammed you providing that you give me details
Guest22-Aug-2012 07:16assd
Rocky Welch19-Aug-2012 06:55Here is another scammer his name is Adjei Okore Issac located out of Kasoa district Accra Ghana phone number is 0233?332?092?716 and poses to have gold bars and when the fees are paid he says he will ship the bar but doesn?t. He claims that the ownership needs to be changed over through a attorney and refuse to refund the money. DO NOT CONTACT THIS GUY OR YOU WILL BE BURNT I and my attorneys are contacting the Embassy and minerals commission in Ghana to put this guy out of business and have him arrrested for theft by conspiracy.
Priyesh garg15-Aug-2012 14:54Plz tell me about Ancient African mining co. ltd. And his director Justice Akoto as he hv offered me cheap gold
Guest14-Aug-2012 03:25hi,
kindly verify these persons with email add. frank.cmensah@yahoo.com and maxwell cole from ghana and working in a gold mining company in your area.They claim to sell gold in our country.May I be informed immediately thanks
Guest13-Aug-2012 09:01Anyone who deals with Keith Owino/ Keith M. Owino ? a Ugandan national ? be prepared to lose your money, waste your time and never close a deal.
The company Platinum Rock/Platinum Rock Advisory/ Platinum Rock FZE, does not exist, it is not registered anywhere in the world (even though he claims it is registered in the Cayman Islands) he is a pathological liar and uses people for their contacts and money. He pretends to be some big time trader, when he has NO experience and has no idea what he is doing,he is a big time fraud broker!!He will lie & tell you what ever you want to get money out of people,and will leach money off others!
Do not bother dealing with this idiot as he is the BIGGEST waste of time and will ruin your networks and contacts.
keith@platinumrock.org / keithowino@yahoo.co.uk
Garry13-Aug-2012 08:35Anthony R. Sterle, President/CEO
The Akropolis Group , Akropolis Venture Inc ,Akropolis Foundation
ANTHONY STERLE
Private Placement Program (PPP) SCAM SCAM SCAM
THIS IS THE SCAM OF PAST DECADES RE-HATCHED
ONLY DIFFERENCE HE SELLS GOLD AND PUTS ON A PLATFORM !!!
SO HE SAYS THIS FINE PIECE OF WORK, NOTHING BUT AN EGOTISTICAL MANIAC !!!
PRIVATE PLACEMENT PROGRAM WITH A TWIST.
THE TWIST IS HE TAKES YOUR MONEY AND DISAPPEARS
HOW ? SIMPLE HE IS A CON-ARTIST AND MANIPULATIVE
I WILL SPARE YOU ALL HIS PATHETIC METHOD THAT HE DOES IT IN
AND SIMPLY WARN YOU ALL TO STAY AWAY FROM THIS CYNICAL MAN
UNTIL THE FEDS ARREST THIS CROOK
FRAUD ALERT HIGH !!
Anthony R. Sterle
Anthony R. Sterle, President/CEO
Akropolis Foundation
Office Phone: (702) 735?2000
Mobile Phone: (702) 860?2443
Fax: (702) 260?4188
E-mail: Akropfoundation@aol.com
Skype: Akropolis.Foundation1992
Guest13-Aug-2012 07:49Anthony Sterle and Akropolis Foundation are total scammers!
Never believe this guy, anthoney sterle, and his akropolis foundation LIES
their iron ore projects are total scams and only waste your time and scam your money
they are simple brokers ,but act as some big time sellers, they are really nobody but a big sham and swindlers
never waste your time with Mr
anthony Sterle and Akropolis Foundation
Guest13-Aug-2012 00:05Has anyone hear o Theresa Ansaba Opoku,from Toronto ?? Director of Derby Kaemon Ghana Limited.Please let me know as I am about to invest 25.000 into this gold mine?Thank you.
Sergio Herrandiz Gil08-Aug-2012 07:30Hi, I?m a serious Gold Buyer ?direct? Swiss Company working with supervision of the Swiss Federal Ofice of Precious metals.
We do not make any kind of advanced payment nor bank garanties. We buy only FCO Airport Z?rich with payment after certification of the Swiss Federal Office of Precious Metals. We do have our own reffinery.
Please send your offers?.
sh@alfaaurum.com
Sergio Herrandiz Gil
President
Alfa Aurum Holding SA
SM Aurum Protect Ltd.
Switzerland
Sergio Herrandiz Gil08-Aug-2012 07:28Hi, I?m a serious Gold Buyer ?direct? Swiss Company working with supervision of the Swiss Federal Ofice of Precious metals.
We do not make any kind of advanced payment nor bank garanties. We buy only FCO Airport Z?rich with payment after certification of the Swiss Federal Office of Precious Metals. We do have our own reffinery.
Please send your offers?.
sh@alfaaurum.com
Sergio Herrandiz Gil
President
Alfa Aurum Holding SA
SM Aurum Protect Ltd.
Switzerland
Frank04-Aug-2012 15:02Has anyone heard of this outfit maligoldtradelink01@gmail.com. I have been chatting to Chinese woman ? syysiizhang@yahoo.com and she is asking me to contact this group and make enquiries because she is in Southern Mali as Procuremnet Officer working for company building Federal Finance building for next 4 months. She was quoting $US 30.000 per Kilo and asked me to check what deal I could get. Suggested bring to Aus to sell as if we were partners. Enquired if I knew Gold sellers out of Australia.Maybe she is being scammed or is a scammer.
Frank04-Aug-2012 14:26Has anyone heard of this outfit maligoldtradelink01@gmail.com. I have been chatting to Chinese woman ? syysiizhang@yahoo.com and she is asking me to contact this group and make enquiries because she is in Southern Mali as Procuremnet Officer working for company building Federal Finance building for next 4 months. She was quoting $US 30.000 per Kilo and asked me to check what deal I could get. Suggested bring to Aus to sell as if we were partners. Enquired if I knew Gold sellers out of Australia.Maybe she is being scammed or is a scammer.
tris02-Aug-2012 13:52yaw.jon has a phone number: +61488722230
thankyou
tris02-Aug-2012 13:50yaw.jon has a phone number: +61488722230
thankyou
tristan02-Aug-2012 13:47Hey, I got added by a man from ghana and his username is: yaw.jon and he claims his name is michael, which im sure is fake. he told me that if i send him money he?ll buy gold and send it to me so i can sell it here, in australia? ha! i just said i have no money and ended call, i got annoyed about how persistant he was, he also stated he wanted to open a internet cafe. hahahaha
tristan02-Aug-2012 13:46Hey, I got added by a man from ghana and his username is: yaw.jon and he claims his name is michael, which im sure is fake. he told me that if i send him money he?ll buy gold and send it to me so i can sell it here, in australia? ha! i just said i have no money and ended call, i got annoyed about how persistant he was, he also stated he wanted to open a internet cafe. hahahaha
tristan02-Aug-2012 13:45Hey, I got added by a man from ghana and his username is: yaw.jon and he claims his name is michael, which im sure is fake. he told me that if i send him money he?ll buy gold and send it to me so i can sell it here, in australia? ha! i just said i have no money and ended call, i got annoyed about how persistant he was, he also stated he wanted to open a internet cafe. hahahaha
Kent26-Jul-2012 13:38Has anyone heard of John Amos from Ghana?
Kent25-Jul-2012 23:29Has anyone heard of John Amos from Ghana?
Kent25-Jul-2012 23:21Has anyone heard of John Amos from Ghana?
FELIX25-Jul-2012 10:03another criminell company:
AFRICAN ANCIENT MINING
MR JUSTICE AKOTO
DON?T GET IN CONTACT WITH THESE PEOPLE
David24-Jul-2012 08:54Hello,
I have a gold seller from Africa who delivers both on CIF and FOB.
For direct buyers only.
Email: dcheiferl@gmail.com
TIMOTHY D. MEROLA23-Jul-2012 12:09adonagold@yahoo.com GOLD BUYERS BEWARE OF THIS EMAIL ADDRESS
TIMOTHY D. MEROLA23-Jul-2012 12:09adonagold@yahoo.com GOLD BUYERS BEWARE OF THIS EMAIL ADDRESS
TIMOTHY D. MEROLA23-Jul-2012 12:05GOLD BUYERS BEWARE-ADONA GOLD LTD,CEO KENNEY GIWA,ACCRA,GHANA ARE SCAMMERS, CALL OR CONTACT ME, TIM MEROLA, PALM BEACH,FLORIDA USA 561?284?2406 OR EMAIL AT tmerola973@aol.com.. THIS MAN IS A VERY SLICK CON MAN, HE NEVER DELIVERED THE GOLD, HE HAS TAKEN OVER $8,000 US DOLLARS FROM ME AND HAS CREATED A FINANCIAL NIGHTMARE WITH TWO BANKS, AND SEVERAL CREDIT CARDS. A POLICE REPORT HAS BEEN FILED WITH PALM BEACH SHERIFFS OFFICE, FBI, US POSTAL INSPECTORS,INTERNET CRIME INVESTIGATORS, ALL CREDIT AGENCIES, ETC.
TIMOTHY D. MEROLA23-Jul-2012 12:05GOLD BUYERS BEWARE-ADONA GOLD LTD,CEO KENNEY GIWA,ACCRA,GHANA ARE SCAMMERS, CALL OR CONTACT ME, TIM MEROLA, PALM BEACH,FLORIDA USA 561?284?2406 OR EMAIL AT tmerola973@aol.com.. THIS MAN IS A VERY SLICK CON MAN, HE NEVER DELIVERED THE GOLD, HE HAS TAKEN OVER $8,000 US DOLLARS FROM ME AND HAS CREATED A FINANCIAL NIGHTMARE WITH TWO BANKS, AND SEVERAL CREDIT CARDS. A POLICE REPORT HAS BEEN FILED WITH PALM BEACH SHERIFFS OFFICE, FBI, US POSTAL INSPECTORS,INTERNET CRIME INVESTIGATORS, ALL CREDIT AGENCIES, ETC.
Rosental21-Jul-2012 01:07Nana Tettey ?ex police? Accra Ghana scammed us on the promise of delivery but pulled the plug but kept the funds
BIG20-Jul-2012 17:05WHAT PEOPLE FROM BENIN? I HAVE A SO CALLED SELLER SKYPING ME EVERYDAY FROM BENIN. WHAT IS THE NAME? ARE THERE ANY OTHERS?
BIG20-Jul-2012 16:59WHAT PEOPLE FROM BENIN? I HAVE A SO CALLED SELLER SKYPING ME EVERYDAY FROM BENIN. WHAT IS THE NAME?
Rosental20-Jul-2012 06:12Name Dorand Bonay Sika Global Ghana scammer.
Kofi Adjei Tom?s Eastern World Scammer
Smith Abdul14-Jul-2012 09:34DEAR SIR,
BE AWARE OF THESE DANGEROUS SCAMMERS FROM BENIN.THEY SCAMMED MANY PEOPLE AND CONTINUE.YOU WILL NEVER HAVE YOUR GOLD.THEY HAVE PEOPLE IN AIRPORT TO TAKE AWAY YOU GOLD.YOU WILL LOOSE YOUR MONEY AND YOUR GOLD.
THANKS
OLD COMPANY:
COMPAGNIE BENINOISE DE NEGOCE
10 B.P 319 COTONOU/BENIN
CELL. 00229 97 97 31 00
DIRECTEUR: JULES ZANVO AND PETER/ PIERRE
jzenvo@yahoo.fr
NEW COMPANY
STE RTAE
COMPTOIR D?ACHAT,DE VENTE D?OR,DIAMAND ET AUTRES METAUX PRECIEUX
IMPORT-EXPORT/ COMMERCE GENERAL
05 B.P.1309 COTONOU/ BENIN
RCCM RB/ COT/10 B 5669 TEL. 00229 95 40 93 03
MANAGER: MOHAMED TOURE
E-MAIL: rtaemetal@ymail.com
Guest13-Jul-2012 15:27Stefano Gobbato Scam Artist of the Century
This is a very sophisticated Fraud System
HIGH ALERT !!
Stefano Gobbato
Co-Founder & Director
Elite Portable, Physical, Precious
Asset Provider since 2000
www.digholding.com
Skype: maskyo GMT+1
PS ALSO KNOWN AS STEFANO BIGGOB , MOST VEIN & UP HIMSELF
Guest13-Jul-2012 15:21Stefano Gabboto Scam
Seffano Gabboto Scammer
Stefano Gobbato
Co-Founder & Director
Elite Portable, Physical, Precious
Asset Provider since 2000
www.digholding.com
Skype: maskyo GMT+1
Guest13-Jul-2012 15:13AKROPOLIS FOUNDATION
i see these guys Anthony and Nancy Sterle all over scam sites across the board
They are also on ali baba . com selling Gold with Cheap Finance to buy it ?
Why are the Authorities not all over them ? can someone tell me please
Guest10-Jul-2012 17:31Let no-one be fooled by this scammer with ?four? names. He alleges to be on sayyidasaadalsaid@gmail.com and will ask all sorts of seemingly intelligent questions. However, this is bogus. He will run rings around you and eventually get you if you don?t do your homework carefully. This scammer will refer you to International Services, the alleged private financial brokers of the Al Sayyid Investment Company and talk about inviting you to Dubai for the signing of paperwork etc. Key to this nonsense is the desperation of the deposit which is dressed as an ?Investment Insurance Deposit?. DONT FALL FOR IT. his other alias is Dr Adan Markell. Ha ha!
Guest10-Jul-2012 17:29Let no-one be fooled by this scammer with ?four? names. He alleges to be on sayyidasaadalsaid@gmail.com and will ask all sorts of seemingly intelligent questions. However, this is bogus. He will run rings around you and eventually get you if you don?t do your homework carefully. This scammer will refer you to International Services, the alleged private financial brokers of the Al Sayyid Investment Company and talk about inviting you to Dubai for the signing of paperwork etc. Key to this nonsense is the desperation of the deposit which is dressed as an ?Investment Insurance Deposit?. DONT FALL FOR IT. his other alias is Dr Adan Markell. Ha ha!
GUEST10-Jul-2012 10:06FRAUD ALERT.
PLEASE BE AWARE OF THE COMPANY AFRICAN ANCIENT MINING THEY ARE PROFESSIONAL SCAMMERS. THE CEO IS MR JUSTICE AKOTO AND HIS FATHER THE CHIEF OF THE VILLAGE. THERE WEBSITE IS
WWW.ANCIENT MINING.COM MR AKOTO PASSPORT NUMBER H 1088033 ADDRESS 9TH YAA ASANTEWAA ROAD UNITY BUILDING, HOUSE T34/20 GHANA EMAIL ADDRESS aancientminingcompanylimited@yahoo.com THE BROTHER OF MR AKOTO IS THE ONE WHO WILL DO ALL THE DRIVING IS MR KOFFI CELL NO; +233546 564966 MR AKOTO CELL NO; +233202 622351. PLEASE STAY FAR AWAY FROM THESE THIEVES.
Faiyaz10-Jul-2012 08:34Thanks,very good job done to help innocent guys who cannot get involved themselves with these dirty people
Guest09-Jul-2012 08:22Smargow Resources Limited based in Pawtucket USA ? has anyone heard of these guys?
Selling Gold from Ghana at a low price. Scam ?
thanks .
Mark.
Dino08-Jul-2012 21:07There is someone who knows Frank Niguessan in Cote d ?ivoire , Gold seller from AKAR Metal Ldt, we are searching for real seller
mutsa chikede06-Jul-2012 12:37THANK YOU FOR THESE SCAMMERS, MAY YOU send me updates of these scammers, i am in the bussines of repairing mining glass fibre utensils, i have been made to travel long distances in search for mine repair bussiness only to end up trapped in gold scam traps
munaf05-Jul-2012 21:40thanks, i am going to deal with Ankomah and sons company kindly tell me this is fack or what
GUEST01-Jul-2012 16:23TONY STERLE SCAM
INCLUDES PPIP SCAM GOLD SCAM RESOURCES SCAM
THIS IS ONE EVIL INDIVIDUAL
Anthony R. Sterle, President/CEO
Akropolis Foundation
Office Phone: (702) 735?2000
Mobile Phone: (702) 860?2443
Fax: (702) 260?4188
E-mail: Akropfoundation@aol.com
Skype: Akropolis.Foundation1992
Guest01-Jul-2012 16:03Name: Nancy Sterle
Aka: Nancy Alder
Age: 65
Location: US
Address: unknown
Phone: unknown
Email: akrop2000@aol.com
On web sites: Unknown
Report: Scammer a la carte Warning do not approach
Robert30-Jun-2012 15:19Anthony Sterle AKA Tony the phonie
Scam Lies and more Scam and lies , someone stop this old bastard
Anthony R. Sterle
Anthony R. Sterle, President/CEO
Akropolis Foundation
Office Phone: (702) 735?2000
Mobile Phone: (702) 860?2443
Fax: (702) 260?4188
E-mail: Akropfoundation@aol.com
Skype: Akropolis.Foundation1992
Lisa30-Jun-2012 15:16ANTHONY STERLE SCAMMER
NANCY STERLE SCAMMER
I was warned but fell for there bullshit , best thing to do everyone is report them to the correct authorities as they deserve to be jailed
Anthony R. Sterle
Anthony R. Sterle, President/CEO
Akropolis Foundation
Office Phone: (702) 735?2000
Mobile Phone: (702) 860?2443
Fax: (702) 260?4188
E-mail: Akropfoundation@aol.com
Skype: Akropolis.Foundation1992
Garry Johns30-Jun-2012 15:13ANTHONY STERLE SCAMMER
NANCY STERLE SCAMMER
PLEASE STAY AWAY FROM THIS COUPLE ??????FRIENDS HAVE BEEN RIPPED OF FOR $$$$$$$$$$$$$$
THEY WILL SELL YOU ANYTHING YOU SAY YOU NEED, THEY HAVE NOTHING BEHIND THEM OTHER THAN THE INTENTION TO RIP YOU OFF
Anthony R. Sterle
Anthony R. Sterle, President/CEO
Akropolis Foundation
Office Phone: (702) 735?2000
Mobile Phone: (702) 860?2443
Fax: (702) 260?4188
E-mail: Akropfoundation@aol.com
Skype: Akropolis.Foundation1992
adamadam29-Jun-2012 14:07hello sir
Do you know called Sam Cody(00233547843102,00233244204567)&another person wich called Robrt Djan(00233261975450)
Where I dealt with them in huge amounts in order to get the gold dust
But I did not get anything
Note
They sent me a copy of their passports
But I think they?re crooks people
With my appreciation
thomas Wright29-Jun-2012 13:22ANTHONY STERLE SCAM AND NANCY STERLE SCAM
PLEASE KEEP CLEAR OF THIS BONNIE AND CLYDE SHOW
Anthony R. Sterle
Anthony R. Sterle, President/CEO
Akropolis Foundation
Office Phone: (702) 735?2000
Mobile Phone: (702) 860?2443
Fax: (702) 260?4188
E-mail: Akropfoundation@aol.com
Skype: Akropolis.Foundation1992
Terry Powell28-Jun-2012 17:24Beware of Tommy Jepperson. He is asking for money to get his gold shipped to the United States and he is doing it by romance promises to any and all age women. He says it is family business and he wants to come home to America and live in Georgia again where he says he lived before going to Ghana. This man is all over facebook, yahoo messenger and just about every chat site there is.
Guest26-Jun-2012 12:01Be aware of Cooperative Miniere Dekisenge, their ?headquarters? they claim is B.P 342, Kolowezi, Katanga ? DRC. This company is not registered with the ministry of mines in Congo, they are operating illegally and trying to sell ?gold? in Lusaka,Zambia.They expect buyers to pay for the TTI costs and pay for their Operations Director ? Samar Kambale HUssein? to fly with the gold to the destination. But they won?t show you all the documents, and their agent in Lusaka ? Mette Chishimba from Guardian Cargo Ltd or Suleen Investments in Lusaka,Zambia, he is also part of this scam. The CEO or Director for Cooperative Miniere Dekisenge is Zagabe Kimputu, and his secretary ? Jean Marie Kapenda. Also involved is Emmanual Kazali,they are all Congolese and big time scammers.
Guest26-Jun-2012 11:59Be aware of Cooperative Miniere Dekisenge, their ?headquarters? they claim is B.P 342, Kolowezi, Katanga ? DRC. This company is not registered with the ministry of mines in Congo, they are operating illegally and trying to sell ?gold? in Lusaka,Zambia.They expect buyers to pay for the TTI costs and pay for their Operations Director ? Samar Kambale HUssein? to fly with the gold to the destination. But they won?t show you all the documents, and their agent in Lusaka ? Mette Chishimba from Guardian Cargo Ltd or Suleen Investments in Lusaka,Zambia. The CEO or Director for Cooperative Miniere Dekisenge is Zagabe Kimputu, and his secretary ? Jean Marie Kapenda, also involved is Emmanual Kazali,they are all Congolese and big time scammers.
B Mullaney22-Jun-2012 11:18Has anyone heard of Mary Birch (Tema Ghana0 she regons that she has 30kgs of gold and needs money to get it out of the Gold Security Company she has some type of documents ( not too sure if they are authentic )
B Mullaney22-Jun-2012 11:18Has anyone heard of Mary Birch (Tema Ghana0 she regons that she has 30kgs of gold and needs money to get it out of the Gold Security Company she has some type of documents ( not too sure if they are authentic )
Guest22-Jun-2012 04:51Dear Thomas
Funny you should list these guys as i have had nothing but bad reviews and they rope you in with empty promises
If anyone else has had this experience please list them on all sites as these scammers should not be able to operate.
Robert
? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? -
Akropolis Group
Anthony Sterle and Nancy Sterle SCAMMERS
BE AWARE AND DO NOT ENGAGE
Thomas Wright22-Jun-2012 04:43Akropolis Group
Anthony Sterle and Nancy Sterle SCAMMERS
BE AWARE AND DO NOT ENGAGE
Guest21-Jun-2012 10:54I am in contact with a man called mensah adjei from accra in ghana , company rich mine company email metalminerals@lycos.com ? is this guy for real ? he advertised on alibaba and how trade etc. i googled it and it did come up with an address in ghana , but when i googled the company address it didnt show any results ? does anyone know anything about this man , i have been proposed to send him 7.5% of 22,000 for a sample ( ship cost) to pay the rest when it arrives ? he dosnt want to disclose any documentation til august til we do the transaction for various reasons ? what should i do ?
JP17-Jun-2012 12:19Just to confirm BBC Impex ? Tanzania, as scammers! Names that might be envolved: Armando Cardoso (Portuguese), Julian Kilonzo and Michael Ngongo (Tanzanians). Stay away from these crooks!
JP
Oleg11-Jun-2012 14:48For your information please, there is no gold in Cotonou, all bullshit and full of scams and thieves. I have visited there two times and came back empty handed.
Mark09-Jun-2012 13:04Eastern Translines is a fake company from Tanzania
African Union Mining in Ghana has a fake licence
N and K Trading in Tanzania is fake
Adul mining in Ghana is a fraud
hector j.sepulveda09-Jun-2012 12:56if any one know any real gold seller in cotunou plaese put hin in contact with me
we are interested go into contract of 650 kilos by month for 24 month is urgently thank you
best regard hector julio sepulveda skype contact,, hector.herrera39
Marcus Bassilis09-Jun-2012 09:36Hello do any vary know hassan alidou from cotonou in benin we are trying to buy gold fron him. true a company maned / ste groupe j.nastelle sarl/DIRECTED BY DEHOHOU JONAS in porto novo if is any scamer act or information fron him just let me know.or if there is some that
knows a rear seller in benin cotonou just let me know
thank you
Oleg08-Jun-2012 19:52Hello Victor, I deal with him before, he will ask for upfront and no shipment to you.
You can write me: lev.oleg@bk.ru
Ken Brown08-Jun-2012 17:06Hi ? has anyone had any dealings or contact with Mr Victor Lutanga Bongo from the MINING NYANZA COMPANY B.P 147 Kibali, Ituri P.OR R Congo ? your information would be helpful ? he is selling gold in Kenya ? KEN BROWN
Guest08-Jun-2012 16:32Hi ? has anyone had any dealings or contact with Mr Victor Lutanga Bongo from the MINING NYANZA COMPANY B.P 147 Kibali, Ituri P.OR R Congo ? your information would be helpful ? he is selling gold in Kenya ? KEN BROWN
Fall andre05-Jun-2012 06:32Be aware of this impostor company in Benin:AFRIMA SARL
It?s a band of at least 6 persons:
Remember their names:
Sebastien DELCANO Tolinou / Felix YETO /JONAS GNOLONFOUN /CYPRIEN K.BALLO?
These guys are very dangerous,big Thiefs-liars!
Guest22-May-2012 15:24Eastern Translines profile on tradekey is under investigation for fraud. Their account is now suspended
Guest22-May-2012 15:03
Domain Name: EASTERNTRANSLINE.COM
Registrar: DIRECTI INTERNET SOLUTIONS PVT. LTD. D/B/A PUBLICDOMAINREGISTRY.COM
Whois Server: whois.PublicDomainRegistry.com
Name Server: NS1.EACDIRECTORY.CO.KE
Name Server: NS2.EACDIRECTORY.CO.KE
Status: clientTransferProhibited
Updated Date: 17-mar-2012
Creation Date: 17-mar-2012
Expiration Date: 17-mar-2013
Registrant:
Eastern Trans Line Tanzania Limited
Eastern Trans Line Tanzania Limited ( mailto:jeanclaudembemba@gmail.com)
Mkwepu street, Mikocheni
P.O. Box 35061
DAR ES SALAAM
DAR ES SALAAM,35061
TZ
Tel. +255.255682724425
Guest22-May-2012 14:59Eastern Translines is a fake, Jean Claude Mbemba and Marc Peter promised to deliver my gold in April. I am still waiting. God will hand you justice my friend.
the fraudsters in Eastern Translines have the same contact details of a known scamming company. Call any of their phone numbers, nobody answers. Legimate people can be contacted easily not hide behind skype and gmail.
Guest22-May-2012 14:54Anybody ever hear of African Union Mining? Osei Owusu is the CEO? Or is it really Mike Owusu
Guest22-May-2012 14:48Paul Frimpong is now operating in Nyarsu mines as Yaw Frimpong
Guest22-May-2012 14:47Paul Frimpong is now operating in Nyarsu mines as Yaw Frimpong
GreatGemsGreatPrices18-May-2012 03:31Nana Kofi Adjei is a big time waster he never pass any proper business dealings very very few of these gold seller have any real gold. I have in my experience only had to international firms every pass any real background checks and banking checks if your getting into gold do it right never send money upfront ever always set up a lawyer trust account with a lawyer you trust where the laywer doesnt release money till gold is at your personal refiners account
We dont even buy unless its delivered to Canada anymore and wont even consider issuing invite letters unless i receive same at sellers expense yes next to none will do this because next to none are real seller.
you will make more buying Scrap Gold locally from people in Your city then buying gold dust
thanks
Mike09-May-2012 00:25We buy gold please help us clear some issues.
Damir03-May-2012 19:22Hahhahaaa This one is best ahhahaa fuck face
From: hct111@live.hk
To: hct111@live.hk
Subject: approved
Date: Fri, 4 May 2012 00:30:18 +0530
I am the most happy as I want to inform you that I just received news that the funds have been approved. There is nothing as good as seeing the remuneration for hard work I must say we truly deserve this reward. I am on my way to see our attorney so that I can see the original copy of the approval. This calls for celebration I will get back to you as soon as I can. Please also let the bank know about the urgency in the account opening so they can be quick about the account opening. and you let me have the account details as soon as you get it please.
I will be forever indebted to you for this success in this transfer transaction and I am grateful that I found someone like you in the process.
Ho.
Guest29-Apr-2012 18:09Thank you for posting the Amad investment group. something seemed funny to us so I set up a meeting in Dubai. a bunch of idiots. beware of name Dr. Mustapha, he is just a nigger thief.
Jean Claude Mbemba27-Apr-2012 18:36Hello
I am Jean Claude Mbemba from Eastern Trans Line Tanzania Limited. I just realized that some one called Ken on this site posted non scene saying that we sold brass in the form of gold to someone. Please Mr. Ken I want to inform you that there is another company with a similar names as our going by Eastern Trans Line. You are clearly confusing this company with ours and posting comments that deform the reputation of our company. Please try to do your due diligence properly and you will find out that we are not the company that you think we are. Please try to respect our company and retrieve that comment which is causing so much harm to our company.
Regards
suresh Peter27-Apr-2012 08:45I am looking for a real GOLD seller ? i have real buyers
Guest18-Apr-2012 17:29
The correct and confirmed email contacts for Tawfeek AlNabelsey and Associates Law firm in Oman is : tawfeeekalnabelsey@gmail.com, do not respond to any other email that does not come from this address.
Guest15-Apr-2012 07:51Brima Coker is a scammer pure mineral investment
stewart12-Apr-2012 14:40here is another one Vinod Nair an from Tirupur in Indian skype : nairvinod1
email : vinodnair1806@gmail.com he also uses vinod nair
Scott10-Apr-2012 18:29Noble Base Metals are criminals, they are not gold miners and have no gold to offer, keep away from them.
Agent10-Apr-2012 13:06Gold Scammers:
?Eastern Trans Line? from tanzania sells brass as gold on behalf of ?Noble base metals & gemstones? of tanzania. Eastern trans acts as the shipping company and does the dirty scam.
As mentioned on this page they are also considered very dangerous.
Has anybody heard or dealt with ?Noble? ??
Noel A. M10-Apr-2012 09:55BEWARE OF THE FOLLOWING INVESTMENT SCAMMERS:
1) His Highness Al Sayyid Asa?ad bin Tariq Al Said
Chief Executive Officer
Asad Investment Company
Getco Tower, M.B.D. Ruwi
(P.O. Box 971) 113
Al Hamriya,
Muscat, Oman
Email: sayyidasaadalsaid@gmail.com
Phone: +968 2 470 4444, Fax: +968 2 661 4333
2)Tawfeek AlNabelsey and Associates
Muscat Int?l Centre, Beit Al Falaj St.
P.O. Box 2027 Ruwi, Oman
Phone No. : +968 248 777 92
EMail : tawfeekalnabelsey@gmail.com
3)Muzanni Bin Kaamil.
Chief Public AdministrantDubai Emirates Investors (DEGIA).
DUBAI EMIRATES INVESTORS
Dubai Emirates Foreign Investment Representative Office:7th Floor, 125 Pall Mall, London SW1Y 5EA, UKP.O.Box, 40741,Phone:+447031859841, +447031827781 Fax: +4470457 01805
4)Terry Smith
All four are the same person, advance fee, 419 scammers, with Banking details;
C/O Terry Smith, Oman Investment Authority, Ministry of Finance
Building, P.O. Box 506, Muscat 100, Sultanate of Oman
International Business Account;
Account name ; Oman Investment Authority
Bank Name ; LLOYDS TSB BANK
Bank address ; 95 George St, Croydon, Surrey CR9 2NS England
Account Number ; 37202168
Bic ; LOYDGB21
Sort Code ; 309245
IBAN NUMBER ; GB79LOYD30924537202168
5) Sky High Finance ?.email; skyhighfinance@gmail.com???.. ?
Robert Cole
6) Mr Ray Laurence??. equityloanfirm221@gmail.com
josep05-Apr-2012 17:58royal continental limeted is a big fake seller becarefull with this big scammer
also GOLDMAN from accra mr komlas ?.
stelios koskinas05-Apr-2012 17:21please can you tell me if this gold company from ghana is legal?
ANKOMAH & SONS LTD
TEL: +233 572656068
Email:diamondhouse@consultant.com
ken02-Apr-2012 18:29beware of
JEAN CLAUDE MBEMBA
SALES DIRECTOR
EASTERN TRANS LINE TANZANIA LIMITED
SKYPE: jean80.claude
MOBILE: +255 682724425
Email:jeanclaudembemba@easterntransline.com
jeanclaudembemba@gmail.com
WEBSITE:
www.easterntransline.comblacklisted by the Tanzanian government and classified as extremely dangerous. They sent a stolen passport as proof of identity. Probably someone who was also scammed. their scam is they ask you to pay the taxes and export to a bogus government office..
etang16-Mar-2012 14:16Gregg Lyell, Dutch , George Wagner gangs online they are scammer and criminal they are big time scammer online. Now Victor you are one of the victim buying his book.
agnes16-Mar-2012 14:13Victod I know Gregg Lyell he is big time scammer he sale books online to earn money he is real scammer. Victor why did you buy his books ? He has no job is to scamm people linkedin promoting his scam book.
Melvin Akridge15-Mar-2012 16:18Scammer Alert!
BBC Import & Export company Ltd Tanzania are non performers and advanced fee fraudsters. They will present legitimate looking documents and sign any SPA / contract you may send to get your interest. Avoid wasting your time and resources by not engaging in any communications with them. Take this advise.
Melvin Akridge
Email: m_akridge@aol.com
Andrei13-Mar-2012 20:11Asonia Gold mining fraud or not please tell me.
Thank you.
satpal07-Mar-2012 06:59Dear sir/ mam
Mr Maxwell from accra Ghana he send me all certificate of rich mining investment limited. is this true? his ph no is +233244811223.he given me opportunity for this Gold business.
GOLDACCESS CONSULTANTS LIMITED
HINCHLEY DRIVE WESTWARD ROAD
LONDON ENGLAND E4898QG
Email:goldaccessconsultantslimited@yahoo.com
Tel:+44 (0)704 309 8919 Fax:+44 (0)704 308 2161
Mr.David Addo
Global Transaction Ghana Limited .
Tele phone :+233 20833 4663 .
davidaddo99@gmail.com
Paul Frimpong.
Skype: paul.frimpong7
paulfrimpong46@yahoo.com.ph
Erick Ankomah
Taskas Ventures Cooperative Ent
North Kaneshie
Accra, Ghana
Mayland Courier Services
56 Liberty Ave. Achimota Accra
www.mlcservices.50webs.com
Email: mtldcs606169@consultant.com
Email: gdcsvs@diplomats.com
Tel/Fax: +233302937100
Fax: +233244484629
Todd05-Mar-2012 15:48I Have contacts with a reliable gold seller from Africa, He has been supplying gold to our refinery for the past two and half years now, and I must say he is trusted and efficient in business.
Gold buyers looking to buy gold should kindly contact me.
Email: tseigmeister@aol.com
Guest29-Feb-2012 13:26Ali Ahmed cell number +233 245115581 please add to his name just sent in
Guest29-Feb-2012 13:22Mr Ali Ahmed Passport number H 2415134 EMAIL ADDRESS alight202@yahoo.com Ghana and his secretary Ms Caroline Richards ID number H 2165535 Address H-HCG 121 Niiboi Town Accra Ghana
Scammed us we sent them money via western union for three kg and they vanished. PLEASE BE CAFEFUL DONT BE COUGHT BY THESE TRICKSTERS.
ALI IS A CRIMINAL.
paul20-Feb-2012 15:46does anyone now a Ali Kamara or a Tejan WIlliams from sierra leone are they genuine people who sell rough diamond and gold dust as im very suspicious of these guys
Art04-Feb-2012 00:19Has anyone heard of Gao Village Gold miners and had positive dealings? Republic of Mali Are they people of honor?
MUZZA27-Jan-2012 11:22Hello can you help Please think I am being scrammed
is there a company in Ghana named.
lustre security company limited
Guest17-Jan-2012 15:43MUHUMUZA NTALE. From Kampala, Uganda. Asks for money to be send via Western Union to him or his associate: OWINY JONATHAN. Stay away from him.
GALLEY KWAJOH27-Dec-2011 17:59We are in receipt of your email, and your demands are not reasonable enough to this office.
What do you want to do with the presidents Email and Telephone?
Your business is to come down here and clear your fund from the ministry and once that is done your fund will be transferred to your bank account in Kuwait of where ever you want it to be transferred.
If you are unable to travel down here at this time you have been advised to provide the document procurement fee of $6200 with the information below on or before the 30th of this month otherwise your fulled will be moved to the reserved treasury as unclaimed fund.
Fund could be send sent through Western or Moneygram with the information below.
RECEIVING INFORMATION.
NAME: GALLEY KWAJOH
CITY: ABIDJAN
COUNTRY: COTE D?IVOIRE
Note that all proceeding has been completed we are just awaiting the procurement of the documents to enable us obtain authorization for the swift transfer of your fund to your choice bank, once this is obtained and verified, your fund will arrive you chosen designation with 2?3 banking days..
For further clarification contact Dr Galley Kwajoh on Tel:+225 666 06350 Email:nfabivorycoast1@bol.com.br
You may contact me alternative on this Telephone Number: +225 465 949 81
Dr Galley Kwajoh
Head of committee
National Financial Audit Board
Cote D? Ivoire
dont send for money this is big frot madar fucker bladi nonsens dont send for money
kwaja27-Dec-2011 17:56We are in receipt of your email, and your demands are not reasonable enough to this office.
What do you want to do with the presidents Email and Telephone?
Your business is to come down here and clear your fund from the ministry and once that is done your fund will be transferred to your bank account in Kuwait of where ever you want it to be transferred.
If you are unable to travel down here at this time you have been advised to provide the document procurement fee of $6200 with the information below on or before the 30th of this month otherwise your fulled will be moved to the reserved treasury as unclaimed fund.
Fund could be send sent through Western or Moneygram with the information below.
RECEIVING INFORMATION.
NAME: GALLEY KWAJOH
CITY: ABIDJAN
COUNTRY: COTE D?IVOIRE
Note that all proceeding has been completed we are just awaiting the procurement of the documents to enable us obtain authorization for the swift transfer of your fund to your choice bank, once this is obtained and verified, your fund will arrive you chosen designation with 2?3 banking days..
For further clarification contact Dr Galley Kwajoh on Tel:+225 666 06350 Email:nfabivorycoast1@bol.com.br
You may contact me alternative on this Telephone Number: +225 465 949 81
Dr Galley Kwajoh
Head of committee
National Financial Audit Board
Cote D? Ivoire
Guest27-Dec-2011 17:55We are in receipt of your email, and your demands are not reasonable enough to this office.
What do you want to do with the presidents Email and Telephone?
Your business is to come down here and clear your fund from the ministry and once that is done your fund will be transferred to your bank account in Kuwait of where ever you want it to be transferred.
If you are unable to travel down here at this time you have been advised to provide the document procurement fee of $6200 with the information below on or before the 30th of this month otherwise your fulled will be moved to the reserved treasury as unclaimed fund.
Fund could be send sent through Western or Moneygram with the information below.
RECEIVING INFORMATION.
NAME: GALLEY KWAJOH
CITY: ABIDJAN
COUNTRY: COTE D?IVOIRE
Note that all proceeding has been completed we are just awaiting the procurement of the documents to enable us obtain authorization for the swift transfer of your fund to your choice bank, once this is obtained and verified, your fund will arrive you chosen designation with 2?3 banking days..
For further clarification contact Dr Galley Kwajoh on Tel:+225 666 06350 Email:nfabivorycoast1@bol.com.br
You may contact me alternative on this Telephone Number: +225 465 949 81
Dr Galley Kwajoh
Head of committee
National Financial Audit Board
Cote D? Ivoire
Victor18-Dec-2011 13:57Do you know Gregg Lyell:
Be aware buying book of Gregg Lyell another scammer he is most another big-time scammer when i read his book it?s full of fantasy. You know how much he charge to read his scam gold and diamond about africa book 35,000 dollar.
Victor18-Dec-2011 13:55Do you know Gregg Lyell:
Be aware buying book of Gregg Lyell another scammer he is most another big-time scammer when i read his book it?s full of fantasy. You know how much he charge to read his scam book 35,000 dollar.
Guest06-Nov-2011 10:48Stay away from these scammers:
Mr J Michel van Kapel & Rhonda H Bowden
RHB Group PTY Ltd
PO Box 560,
Kippa-Ring QLD 4021,
AUSTRALIA
Phone: + 61 7 3204 1809
Fax: + 61 7 3204 8544
Guest02-Nov-2011 17:10The Perkins Mining Company is almost certainly fake. The supposed CEO Claudia Perkins Quaofio contacts men on dating web sites, and performs strip tease for them on a webcam for money. She has several elaborately constructed stories that she uses to persuade the men that she scams money from, and one of them involves her as CEO of Perkin?s Mining Company.
Bakari Family17-Oct-2011 10:37To whom it may con-cine this Post Dr.Wilson Bakari
office in Cotonou Benin Rep/box 18604
Tel: +22998854263
Fax: 0867290220
Email: E-mail:gera.do@live.fr Is not right we are the Bakari Family know as a Gold Family In Burkina Faso, we have a Rep call Dr. Wilson, as we all know that scammers can used any real name to make look as there, just to use it to fraud people, so on No account can our family be of any thing like this.
Bakari Family17-Oct-2011 10:36To whom it may con-cine this Post Dr.Wilson Bakari
office in Cotonou Benin Rep/box 18604
Tel: +22998854263
Fax: 0867290220
Email: E-mail:gera.do@live.fr Is not right we are the Bakari Family know as a Gold Family In Burkina Faso, we have a Rep call Dr. Wilson, as we all know that scammers can used any real name to make look as there, just to use it to fraud people, so on No account can our family be of any thing like this.
Guest09-Oct-2011 23:39Received an email offer from Perkin?s Mining in Ghana. CEO Claudia Perkins Quaofio. Offers big rewards too good to be true. This company has a website but could find no other mention of it in any government or mining news listings. Looks highly suspicious.
KPM24-Aug-2011 08:31Please be careful of a person named John Able Moiwo. He is a scammer that steal people?s money. His details are as follows:
E-mail:johnsonmoiwo@yahoo.com
SIERRA EXPORT AUTO AND CONSTRUCTION SERVICES
135B, HANGHA ROAD
KENEMA
MOBILE
+23276747505
Tom18-Aug-2011 21:44Stay away from Kalou Oumar another Scamer from Mali
Tom18-Aug-2011 21:43Stay away fro a Joseph David.
Mali Consult SARL.
Real Scammer From Bamako Mali
Alex20-Jul-2011 18:34Thanks Noel,
I?ve been searching Alibaba for a genuine supplier, lots of replies, 95% fraudsters,
many of them listed above, good job sir.
Regards
Noel Megumichan13-Jul-2011 18:21Stay away from the following group of AU scammers.
1.Ishmael Odum
Forest Friends Limited
P.O.Box KJ 485
Kejetia ? Kumasi
Tel: +233285333086,
Mobile: +233254240742
2. ARMORSAC MINING COMPANY LTD
EDWARD AGYEMAN
P. M. B. Accra North,
Accra ? Ghana.
Tel: + 233 206 759 954,
+ 233 264 442 277
Fax: + 27 866 031 325
3. West Africa Gold & Diamond
Mr. Mark P Touray
97 Cambell Street Freetown & Guinea Conakry
Tel: +232?76?359030
Mob: +232?33?909950
E-mail:EMAIL:mobileip@comcast.net
4.Kabala Mining Company (SL) Ltd.
Rep by : Mr. Ali Kamara/ Mr.Pratt S.O Redcliffe
Address: 8F Forest Road, Yogomayah, Sierra Leone
Phone: +232 77 782 700
Email: E-mail:ps_or@yahoo.com
5. Dufana Group Company Ltd
Rep by: Mr. Thomas Achaempong, CEO
Tel: +233?24?193?6973
Mr. Kwabena Davies, Director Sales & Marketing
el: +233?27?143?0822
Address:17, A-Lang Avenue, via A-Lag taxi rank, Accra, Ghana
Email: E-mail:dufana@gmail.com
6. FAMILY INHERIATNCE GOLD
Dr.Wilson Bakari
office in Cotonou Benin Rep/box 18604
Tel: +22998854263
Fax: 0867290220
Email: E-mail:gera.do@live.fr
7.The SELLER: BB IMPORT AND EXPORT
Address: Kip?, Commune de Ratoma, Conakry, BP : 4317
Contact Person: Mr Kaba Souleymane (Director)
Telephone: +224 6262 7881 / +225 6635 4162/+225 06353614
E-mail: E-mail:bb.cooperative@gmail.com E-mail:blde_brother@yahoo.fr
THANKS.
NOEL MEGUMICHAN
Email: E-mail:E-mail:noelmegumichan@yahoo.com
Skype: noel.megumichan
Noel Megumichan13-Jul-2011 18:18Dear Mr kofi,
If you are the owner and director of Rich Mining Investment, am sorry to say that someone is spoiling the name of your company. I have taken note of what you said.
Regards,
Noel
Noel Megumichan13-Jul-2011 18:15The offer here from PMMC is fake and from gold scammers, do not sent any emails to this group.
Nana Kofi Adjei05-Jul-2011 17:50Dear Sir,
This is the director of Rich Mining Investment Limited. I write to inform you that, my companny Rich Mining Investment Limited does not know this person below
6. Rich Mining Investment
p.o box Gp 537 ACCRA GHANA.
TEL: +233274014581
FAX: +233285280272
Email: hayford_nyarko10@yahoo.com
Scammer: Hayford Nyarko
Email: bightadams1971@yahoo.com
Kindly ammed your system since my company has never scamed any body off his money so please do well to delet this information above.
NB: Please erase the above information from your system since I do not know the above person using my company for any scam deals
Buggered21-Apr-2011 05:03Sammers Name i sent W.Union Bango Gamar is ?Peter Chukwveke? email : penymore200@yahoo.com
Guest09-Apr-2011 11:16anyone know if there is a scammer called KWAME ANSAH in Ghana selling GOLD DUST and Rough Diamonds
Noel Megumichan24-Feb-2011 08:34Stay away from these group of scammers.
1.Mrs. francina Nguza
Chairlady & CEO
Mnada Mining Company Limited
Democratic Republic of Congo.
Email: mnadamcltd@yahoo.com
2.Le Negoce International S.A.
Lot 1867B Fifadji
03bp 3812 Jericho.
Email:frank2001@Safe-mail.net
Frank Tom
3.Company Name: Blue River Mining Ventures
Address: 12 Ayi Kwei Lane, Achimota
City: Accra
Country: Ghana
Tel: +233285287030
Fax:+233302240584
4 Niza Mining Company
P.O. BOX CS 8140 TEMA, GHANA ,
TEL: 00233 26 4430001,
FAX: 00233 303 301322
Email: abexcomgroup@gmail.com
DAVID TWUMASI
Alot of scammers use Goldmine Investment here is
another one.
5.Goldmine Investment Company
High Tension Street NBT 820
Accra, Ghana.
Tel: +2332032807, +233247091215
Fax: +233285280272
6. Rich Mining Investment
p.o box Gp 537 ACCRA GHANA.
TEL: +233274014581
FAX: +233285280272
Email: hayford_nyarko10@yahoo.com
Scammer: Hayford Nyarko
Email: bightadams1971@yahoo.com
7. Peter Diera
CEO
Akubea Mining and Farming Company, LTD
c/155 Mines Arc Park
Rue De Independence
Cotonou, Benin Republic
8. GEORGE A.ALHASSAN
SAFFGUARD GOLD GH LTD. No 17 lamtey close osu,
p.o box 168 osu
Accra Ghana .
Mob: 00233542407468.
Emai: willmykuke5622@yahoo.co.uk
9. Mr. Nana Agema
RIVER and ROCK MINING CO.
Plot 112, Dandy Close,
Light Industrial Estate
Tell;+23324413602
Email: rockmining_co@libero.it
10. Beware of this impostor Dr Dick Wayn,
Email:wayn.dick@yahoo.com. He works with
a known scammer from Benin by name: Khader Salif.
EMAIL: khader.salif@gmail.com;
11.Robert Kweku
Email: geniunegold.trading@yahoo.co.th
Mob: +233?279523938
12.Paschal Solomon Aka
Email: solomonakaekpuchionwa@yahoo.com
No company, with offices in ABIDJAN IN COTE D`IVOIRE, BURKINA FASO, COTONOU IN BENIN REPUBLIC.GHANA (ETC).
13. AKWAABA Associates Co. Ltd
ACCRA GHANA and ABIDJAN COTE D?IVOIRE
Email:mike01hans@yahoo.fr
14. Mr. Edward Marah
Director of Marketing.
Skpe : golddiamond12
Tel .+232 33583748
E-mail:hozaify@aol.com
15. Sebastien Tolinou
Mob: 0022996962932
Email:tolinousebastien@yahoo.fr
16. Danielle Bartman based in South Africa
diamond scammer
Tel: 0027 72 609 4053
Email: dbartman27@gmail.com
Guest30-Jan-2011 16:02w.dafert@gmail.com this is an international philipian scammer
Ricco Mueller25-Nov-2010 11:20Hello Sir
Maybe you know this Criminell:
El Hadji Mining Company Ltd?)
21 Bp Ouagadougou 1921
Burkina ?Faso
This Criminell destroi the Business in Burkina Faso. we have arrange the Export Fee of 1kg to test this Company and this Seller is run away with this Money and Interpol is start on criminell File.
best regards Stardust Company
And we can send a many more from this Criminells and lot of them we have the Passports. So if your Office want this we can send this all to warning all other in this business.
Avoid Cemac permit Fraud
I was informed that some individuals in Africa and other countries outside the Cemac zone were easily cheated, scammed, and robbed of their hard-earned money by unscrupulous and dubious brokers who are not licensed to handle
CEMAC PERMIT EMAIL
cemacpermit@minister.com matters in Africa.
Avoid Cemac Permit Fraud
The brokers make these people believe that they have the power to give them an export permit from Ministry of Mines in Cameroon even when there is no legal contract between them.
How to Apply for Cemac Permit Authorization Buyer?s Gold License
How to Apply for Cemac Permit Authorization Buyer?s Gold License? You must visit EMAIL
cemacpermit@minister.com to buy the Cemac permit Gold License.
The Central Africa Economic Community (CEMAC) is an economic and monetary union that aims to promote the economic integration of its member countries. The
CEMAC PERMIT EMAIL
cemacpermit@minister.com was established on June 18, 1983, in N?Djamena by six founding members: Cameroon, the Central African Republic, Chad, Equatorial Guinea, Gabon, and the Republic of Congo.
Cemac Buyers Permit License
Any application for the grant of a mining title, authorization,
CEMAC BUYERS PERMIT EMAIL
cemacpermit@minister.com License shall be addressed to the Minister in charge of mines in Cameroon. including one original stamp at the rate in force. The following documents shall be appended to the application
Does a gold buyer from the USA, Europe, Australia, Asia, and Africa need a Cemac permit buyer?s license to import Gold to His or her country? Yes, you need this permit license from the Ministry of Mines in Cameroon, the Gold Permit in Cameroon. Always make sure to Avoid Cemac permit Fraud from a fake website claiming to supply Gold
How to get a gold buying permit in Cameroon
The Ministry of Mines in Cameroon EMAIL
cemacpermit@minister.com issues a gold buying permit in Cameroon. To get a gold buying permit visit
cemacpermit@minister.com. An interview will be scheduled and in the interview, one should be prepared to commit to gold quantities they can buy per month. How to get a gold buying permit in Cameroon, It is a must that this target is met.
https://bonasgold.net/gold-order-process-in-cameroon/ are issued every month and should the license holder not meet the monthly target the license will not be renewed.
How to Order Gold from Cameroon
Looking for How to Order Gold from Cameroon?
EMAIL
cemacpermit@minister.com Ministry of Mine is the best directive to purchase
Gold and
cemacpermit@minister.com from Cameroon Africa. Ready to purchase gold from Africa? Not too fast
. You may not be quite ready to place an order yet. Before you proceed to the order form, please read this vital piece of information below.
An
https://bonasgold.net/cemac-buyers-permit-application/ is required by anyone venturing into the business of buying gold and other precious metals in the EXIT region (Cameroon, Chad, the Central African Republic, Equatorial Guinea, Gabon, and the Republic of Congo). The EXIT Buyer?s Permit is a license that ensures that every transaction is done, certified, and verified by the government through the Ministry of Mines. How to
Order Gold from Cameroon
Buyers currently residing in Cameroon can apply for an EXIT Buyer?s Permit in person at the Ministry of Mines Minmiidt-gov.net, Industries, and Technological Development at the Ministerial Building, Yaounde.
If you are not currently in Cameroon and looking for How to Order Gold from Cameroon, obtaining the EXIT Buyer?s Permit won?t be a problem at all since you can do it directly online.
Note: Before buying from any seller in Cameroon, please request their seller?s license and check for its validity on the License Verification Page. If you notice that someone claiming to be a seller gave you an invalid license number, please
contact us for advice on How to Order Gold from Cameroon with your engagement because such a seller may not be authentic. How to Order Gold from Cameroon
Additionally, after Buying the permit, you are expected to pay the spot Shipment fee as a blow.
After the presentation of the
Exit Permit & Authorization of Spot Shipment document, the courier will now begin with the delivery of Gold to the Buyer
?s Refinery anywhere in the World. How to buy Gold from Cameroon https://bonasgold.net/contact/